1.httpd简介
httpd是Apache超文本传输协议(HTTP)服务器的主程序。被设计为一个独立运行的后台进程,它会建立一个处理请求的子进程或线程的池。
通常,httpd不应该被直接调用,而应该在类Unix系统中由 apachectl 调用,在Windows NT/2000/XP/2003中作为服务运行和在Windows 95/98/ME中作为控制台程序运行。
2.httpd版本
CentOS6默认提供:2.2版本的rpm包
CentOS7默认提供:2.4版本的rpm包
2.1httpd的特性
| 版本 | 特性 |
|---|---|
| 2.2 | 事先创建进程 按需维持适当的进程 模块化设计,核心比较小,各种功能通过模块添加(包括PHP),支持运行时配置,支持单独编译模块 支持多种方式的虚拟主机配置,如基于ip的虚拟主机,基于端口的虚拟主机,基于域名的虚拟主机等 支持https协议(通过mod_ssl模块实现) 支持用户认证 支持基于IP或域名的ACL访问控制机制 支持每目录的访问控制(用户访问默认主页时不需要提供用户名和密码,但是用户访问某特定目录时需要提供用户名和密码 支持URL重写 支持MPM(Multi Path Modules,多处理模块)。用于定义httpd的工作模型(单进程、单进程多线程、多进程、多进程单线程、多进程多线程) |
| 2.4 | httpd-2.4的新特性: MPM支持运行DSO机制(Dynamic Share Object,模块的动态装/卸载机制),以模块形式按需加载 支持event MPM,eventMPM模块生产环境可用 支持异步读写 支持每个模块及每个目录分别使用各自的日志级别 每个请求相关的专业配置,使用来配置 增强版的表达式分析器 支持毫秒级的keepalive timeout 基于FQDN的虚拟主机不再需要NameVirtualHost指令 支持用户自定义变量 支持新的指令(AllowOverrideList) 降低对内存的消耗 |
| 工作模型 | 工作方式 |
|---|---|
| prefork | 多进程模型,预先生成进程,一个请求用一个进程响应 一个主进程负责生成n个子进程,子进程也称为工作进程 每个子进程处理一个用户请求,即使没有用户请求,也会预先生成多个空闲进程,随时等待请求到达,最大不会超过1024个 |
| worker | 基于线程工作,一个请求用一个线程响应(启动多个进程,每个进程生成多个线程) |
| event | 基于事件的驱动,一个进程处理多个请求 |
2.2新增httpd-2.4的模块
| 模块 | 功能 |
|---|---|
| mod_proxy_fcgi | 反向代理时支持apache服务器后端协议的模块 |
| mod_ratelimit | 提供速率限制功能的模块 |
| mod_remoteip | 基于ip的访问控制机制被改变,不再支持使用Order,Deny,Allow来做基于IP的访问控制 |
3.httpd配置文件说明
3.1httpd自带的工具程序
| 工具 | 功能 |
|---|---|
| htpasswd | basic认证基于文件实现时,用到的帐号密码生成工具 |
| apachectl | httpd自带的服务控制脚本,支持start,stop,restart |
| apxs | 由httpd-devel包提供的,扩展httpd使用第三方模块的工具 |
| rotatelogs | 日志滚动工具 |
| suexec | 访问某些有特殊权限配置的资源时,临时切换至指定用户运行的工具 |
| ab | apache benchmark,httpd的压力测试工具 |
3.2rpm包安装的httpd程序环境
| 文件/目录 | 对应的功能 |
|---|---|
| /var/log/httpd/access.log | 访问日志 |
| /var/log/httpd/error_log | 错误日志 |
| /var/www/html/ | 站点文档目录 |
| /usr/lib64/httpd/modules/ | 模块文件路径 |
| /etc/httpd/conf/httpd.conf | 主配置文件 |
| /etc/httpd/conf.modules.d/*.conf | 模块配置文件 |
| /etc/httpd/conf.d/*.conf | 辅助配置文件 |
mpm:以DSO机制提供,配置文件为/etc/httpd/conf.modules.d/00-mpm.conf
4.web相关的命令
4.1curl命令
curl支持以下功能:
- https认证
- http的POST/PUT等方法
- ftp上传
- kerberos认证
- http上传
- 代理服务器
- cookies
- 用户名/密码认证
- 下载文件断点续传
- socks5代理服务器
- 通过http代理服务器上传文件到ftp服务器
//语法:curl [options] [URL …]
| options选项 | 说明 |
|---|---|
| -A/- -user-agent (string) | 设置用户代理发送给服务器 |
| -basic | 使用Http基本认证 |
| - -tcp-nodelay | 使用TCP_NODELAY选项 |
| -e/- -referer (URL) | 来源网址 |
| - -cacert (file) | CA证书(SSL) |
| - -compressed | 要求返回时压缩的格式 |
| -H/- -header (line) | 自定义请求首部信息传递给服务器 |
| -I/- -head | 只显示响应报文首部信息 |
| - -limit-rate (rate) | 设置传输速度 |
| -u/- -user <user[:password]> | 设置服务器的用户和密码 |
| -0/- -http1 | 使用http 1.0版本,默认使用1.1版本。这个选项是数字0而不是字母o |
| -o/- -output | 把输出写到文件中 |
| -#/- -progress-ba | 进度条显示当前的传送状态 |
4.2httpd命令
//语法:httpd [options]
| options选项 | 说明 |
|---|---|
| -l | 查看静态编译的模块,列出核心中编译了哪些模块。 它不会列出使用LoadModule指令动态加载的模块 |
| -M | 输出一个已经启用的模块列表,包括静态编译在服务 器中的模块和作为DSO动态加载的模块 |
| -v | 显示httpd的版本,然后退出 |
| -V | 显示httpd和apr/apr-util的版本和编译参数,然后退出 |
| -X | 以调试模式运行httpd。仅启动一个工作进程,并且 服务器不与控制台脱离 |
| -t | 检查配置文件是否有语法错误 |
5.httpd常用配置
切换使用MPM(编辑/etc/httpd/conf.modules.d/00-mpm.conf文件:
NAME有三种,分别是:
prefork
event
worker
[root@wyt1 ~]# vim /etc/httpd/conf.modules.d/00-mpm.conf
# Select the MPM module which should be used by uncommenting exactly
# one of the following LoadModule lines:
# prefork MPM: Implements a non-threaded, pre-forking web server
# See: http://httpd.apache.org/docs/2.4/mod/prefork.html
LoadModule mpm_prefork_module modules/mod_mpm_prefork.so
# worker MPM: Multi-Processing Module implementing a hybrid
# multi-threaded multi-process web server
# See: http://httpd.apache.org/docs/2.4/mod/worker.html
#
#LoadModule mpm_worker_module modules/mod_mpm_worker.so
# event MPM: A variant of the worker MPM with the goal of consuming
# threads only for connections with active processing
# See: http://httpd.apache.org/docs/2.4/mod/event.html
#
#LoadModule mpm_event_module modules/mod_mpm_event.so
访问控制法则:
| 法则 | 功能 |
|---|---|
| Require all granted | 允许所有主机访问 |
| Require all deny | 拒绝所有主机访问 |
| Require ip IPADDR | 授权指定来源地址的主机访问 |
| Require not ip IPADDR | 拒绝指定来源地址的主机访问 |
| Require host HOSTNAME | 授权指定来源主机名的主机访问 |
| Require not host HOSTNAME | 拒绝指定来源主机名的主机访问 |
| IPADDR的类型 | HOSTNAME的类型 |
|---|---|
| IP:192.168.1.1 | FQDN:特定主机的全名 |
| Network/mask:192.168.1.0/255.255.255.0 | DOMAIN:指定域内的所有主机 |
| Network/Length:192.168.1.0/24 | |
| Net:192.168 |
注意:httpd-2.4版本默认是拒绝所有主机访问的,所以安装以后必须做显示授权访问
[root@wyt1 ~]# vim /etc/httpd/conf.d/httpd-vhosts.conf
<Directory " /data/www.wang.com">
<RequireAll>
Require all granted
</RequireAll>
</Directory>
6.虚拟主机配置
虚拟主机有三类:
1.相同IP不同端口
1.1安装httpd
[root@wyt1 ~]# yum -y install httpd
1.2 关闭防火墙和selinux
[root@wyt1 ~]# systemctl disable --now firewalld
Removed symlink /etc/systemd/system/multi-user.target.wants/firewalld.service.
Removed symlink /etc/systemd/system/dbus-org.fedoraproject.FirewallD1.service
[root@wyt1 ~]# vi /etc/selinux/config
# This file controls the state of SELinux on the system.
# SELINUX= can take one of these three values:
# enforcing - SELinux security policy is enforced.
# permissive - SELinux prints warnings instead of enforcing.
# disabled - No SELinux policy is loaded.
SELINUX=disabled
# SELINUXTYPE= can take one of three two values:
# targeted - Targeted processes are protected,
# minimum - Modification of targeted policy. Only selected processes are protected.
# mls - Multi Level Security protection.
SELINUXTYPE=targeted
1.3添加配置文件
[root@wyt1 ~]# cd /etc/httpd/
[root@wyt1 httpd]# ls //配置文件
conf conf.d conf.modules.d logs modules run
[root@wyt1 httpd]# cd conf.d
[root@wyt1 conf.d]# ls //进入con.d配置
autoindex.conf README userdir.conf welcome.conf
[root@wyt1 conf.d]# find / -name *vhosts.conf //从根查找示例配置文件vhosts.conf
/usr/share/doc/httpd-2.4.6/httpd-vhosts.conf
[root@wyt1 conf.d]# cp /usr/share/doc/httpd-2.4.6/httpd-vhosts.conf . //复制示例配置文件到当前目录
[root@wyt1 conf.d]# ls
autoindex.conf httpd-vhosts.conf README userdir.conf welcome.conf
[root@wyt1 conf.d]# vim httpd-vhosts.conf //修改示例配置文件
#
# Please see the documentation at
# <URL:http://httpd.apache.org/docs/2.4/vhosts/>
# for further details before you try to setup virtual hosts.
#
# You may use the command line option '-S' to verify your virtual host
# configuration.
#
# VirtualHost example:
# Almost any Apache directive may go into a VirtualHost container.
# The first VirtualHost section is used for all requests that do not
# match a ServerName or ServerAlias in any <VirtualHost> block.
#
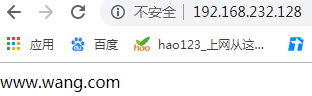
<VirtualHost *:80> //监听端口号(默认主配置文件有)
DocumentRoot "/data/www.wang.com" //网站放置位置
ServerName www.wang.com //域名
ErrorLog "/var/log/httpd/www.wang.com-error_log" //错误日志放置位置
CustomLog "/var/log/httpd/www.wang.com-access_log" common //正确日志放置位置
<Directory "/data/www.wang.com"> //修改目录访问权限
<RequireAll>
Require all granted //允许所有人访问
</RequireAll>
</Directory>
</VirtualHost>
listen 81 //添加监听端口
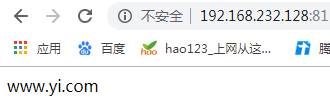
<VirtualHost *:81> //监听端口号
DocumentRoot "/data/www.yi.com" //网站放置位置
ServerName www.yi.com //域名
ErrorLog "/var/log/httpd/www.yi.com-error_log" //错误日志放置位置
CustomLog "/var/log/httpd/www.yi.com-access_log" common //正确日志放置位置
<Directory "/data/www.yi.com"> //修改目录访问权限
<RequireAll>
Require all granted //允许所有主机访问
</RequireAll>
</Directory>
</VirtualHost>
listen 82 //添加监听端口
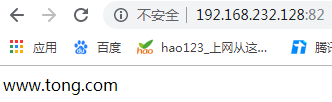
<VirtualHost *:82> //监听端口号
DocumentRoot "/data/www.tong.com" //网站放置位置
ServerName www.tong.com //域名
ErrorLog "/var/log/httpd/www.tong.com-error_log" //错误日志放置位置
CustomLog "/var/log/httpd/www.tong.com-access_log" common //正确日志放置位置
<Directory "/data/www.tong.com"> //修改目录访问权限
<RequireAll>
Require all granted //允许所有人访问
</RequireAll>
</Directory>
</VirtualHost>
1.4创建网页放置目录
[root@wyt1 conf.d]# mkdir -p /data/{www.wang.com,www.yi.com,www.tong.com} //创建目录和文件
[root@wyt1 conf.d]# ll /data/ //查看文件权限
total 0
drwxr-xr-x. 2 root root 6 May 9 23:25 www.tong.com
drwxr-xr-x. 2 root root 6 May 9 23:25 www.wang.com
drwxr-xr-x. 2 root root 6 May 9 23:25 www.yi.com
[root@wyt1 conf.d]# cd /data/
[root@wyt1 data]# ls //查看文件
www.tong.com www.wang.com www.yi.com
1.5生成网页及启动服务
[root@wyt1 data]# echo 'www.wang.com' > www.wang.com/index.html //生成网页
[root@wyt1 data]# echo 'www.yi.com' > www.yi.com/index.html //生成网页
[root@wyt1 data]# echo 'www.tong.com' > www.tong.com/index.html //生成网页
[root@wyt1 /]# tree /data //查看目录树
/data
├── www.tong.com
│ └── index.html
├── www.wang.com
│ └── index.html
└── www.yi.com
└── index.html
[root@wyt1 conf.d]# apachectl -t //查看语法
[root@wyt1 conf.d]# systemctl start httpd //启动服务
[root@wyt1 conf.d]# ss -antl //查看端口
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 :::80 :::*
LISTEN 0 128 :::81 :::*
LISTEN 0 128 :::82 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
1.6验证
2.不同IP相同端口
2.1安装httpd
[root@wyt1 ~]# yum -y install httpd
2.2添加配置文件
[root@wyt1 ~]# cd /etc/httpd/
[root@wyt1 httpd]# ls //配置文件
conf conf.d conf.modules.d logs modules run
[root@wyt1 httpd]# cd conf.d
[root@wyt1 conf.d]# ls //进入con.d配置
autoindex.conf README userdir.conf welcome.conf
[root@wyt1 conf.d]# find / -name *vhosts.conf //从根查找示例配置文件vhosts.conf
/usr/share/doc/httpd-2.4.6/httpd-vhosts.conf
[root@wyt1 conf.d]# cp /usr/share/doc/httpd-2.4.6/httpd-vhosts.conf . //复制示例配置文件到当前目录
[root@wyt1 conf.d]# ls
autoindex.conf httpd-vhosts.conf README userdir.conf welcome.conf
[root@wyt1 conf.d]# vim httpd-vhosts.conf //修改示例配置文件
#
# Please see the documentation at
# <URL:http://httpd.apache.org/docs/2.4/vhosts/>
# for further details before you try to setup virtual hosts.
#
# You may use the command line option '-S' to verify your virtual host
# configuration.
#
# VirtualHost example:
# Almost any Apache directive may go into a VirtualHost container.
# The first VirtualHost section is used for all requests that do not
# match a ServerName or ServerAlias in any <VirtualHost> block.
#
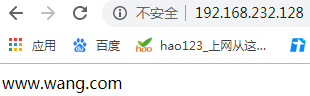
<VirtualHost 192.168.232.128:80> //主机及端口号
DocumentRoot "/data/www.wang.com" //网站放置位置
ServerName www.wang.com //域名
ErrorLog "/var/log/httpd/www.wang.com-error_log" //错误日志放置位置
CustomLog "/var/log/httpd/www.wang.com-access_log" common //正确日志放置位置
<Directory "/data/www.wang.com"> //修改目录访问权限
<RequireAll>
Require all granted //允许所有主机访问
</RequireAll>
</Directory>
</VirtualHost>
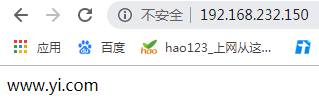
<VirtualHost 192.168.232.150:80> //主机及端口号
DocumentRoot "/data/www.yi.com" //网站放置位置
ServerName www.yi.com //域名
ErrorLog "/var/log/httpd/www.yi.com-error_log" //错误日志放置位置
CustomLog "/var/log/httpd/www.yi.com-access_log" common //正确日志放置位置
<Directory "/data/www.wang.com"> //修改目录访问权限
<RequireAll>
Require all granted //允许所有主机访问
</RequireAll>
</Directory>
</VirtualHost>
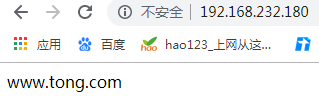
<VirtualHost 192.168.232.180:80> //主机及端口号
DocumentRoot "/data/www.tong.com" //网站放置位置
ServerName www.tong.com //域名
ErrorLog "/var/log/httpd/www.tong.com-error_log" //错误日志放置位置
CustomLog "/var/log/httpd/www.tong.com-access_log" common //正确日志放置位置
<Directory "/data/www.tong.com"> //修改目录访问权限
<RequireAll>
Require all granted
</RequireAll> //允许所有主机访问
</Directory>
</VirtualHost>
2.3创建网页放置目录
[root@wyt1 conf.d]# mkdir -p /data/{www.wang.com,www.yi.com,www.tong.com} //创建目录和文件
[root@wyt1 conf.d]# ll /data/ //查看文件权限
total 0
drwxr-xr-x. 2 root root 6 May 9 23:25 www.tong.com
drwxr-xr-x. 2 root root 6 May 9 23:25 www.wang.com
drwxr-xr-x. 2 root root 6 May 9 23:25 www.yi.com
[root@wyt1 conf.d]# cd /data/
[root@wyt1 data]# ls //查看文件
www.tong.com www.wang.com www.yi.com
2.4生成网页及启动服务
[root@wyt1 data]# echo 'www.wang.com' > www.wang.com/index.html //生成网页
[root@wyt1 data]# echo 'www.yi.com' > www.yi.com/index.html //生成网页
[root@wyt1 data]# echo 'www.tong.com' > www.tong.com/index.html //生成网页
[root@wyt1 /]# tree /data //查看目录树
/data
├── www.tong.com
│ └── index.html
├── www.wang.com
│ └── index.html
└── www.yi.com
└── index.html
[root@wyt1 conf.d]# apachectl -t //查看语法
[root@wyt1 conf.d]# systemctl restart httpd //启动服务
[root@wyt1 conf.d]# ss -antl //查看端口
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 :::80 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
2.5验证
3.相同IP相同端口不同域名
3.1安装httpd
[root@wyt1 ~]# yum -y install httpd
3.2创建配置文件
[root@wyt1 ~]# cd /etc/httpd/
[root@wyt1 httpd]# ls //配置文件
conf conf.d conf.modules.d logs modules run
[root@wyt1 httpd]# cd conf.d
[root@wyt1 conf.d]# ls //进入con.d配置
autoindex.conf README userdir.conf welcome.conf
[root@wyt1 conf.d]# find / -name *vhosts.conf //从根查找示例配置文件vhosts.conf
/usr/share/doc/httpd-2.4.6/httpd-vhosts.conf
[root@wyt1 conf.d]# cp /usr/share/doc/httpd-2.4.6/httpd-vhosts.conf . //复制示例配置文件到当前目录
[root@wyt1 conf.d]# ls
autoindex.conf httpd-vhosts.conf README userdir.conf welcome.conf
[root@wyt1 conf.d]# vim httpd-vhosts.conf //修改示例配置文件
#
# Please see the documentation at
# <URL:http://httpd.apache.org/docs/2.4/vhosts/>
# for further details before you try to setup virtual hosts.
#
# You may use the command line option '-S' to verify your virtual host
# configuration.
#
# VirtualHost example:
# Almost any Apache directive may go into a VirtualHost container.
# The first VirtualHost section is used for all requests that do not
# match a ServerName or ServerAlias in any <VirtualHost> block.
#
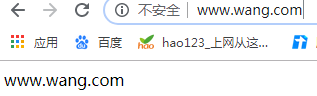
<VirtualHost *:80> //监听端口
DocumentRoot "/data/www.wang.com" //网站放置位置
ServerName www.wang.com //域名
ErrorLog "/var/log/httpd/www.wang.com-error_log" //错误日志放置位置
CustomLog "/var/log/httpd/www.wang.com-access_log" common //正确日志放置位置
<Directory "/data/www.wang.com"> //修改目录访问权限
<RequireAll>
Require all granted //允许所有主机访问
</RequireAll>
</Directory>
</VirtualHost>
<VirtualHost *:80> //监听端口
DocumentRoot "/data/www.yi.com" //网站放置位置
ServerName www.yi.com //域名
ErrorLog "/var/log/httpd/www.yi.com-error_log" //错误日志放置位置
CustomLog "/var/log/httpd/www.yi.com-access_log" common //正确日志放置位置
<Directory "/data/www.yi.com"> //修改目录访问权限
<RequireAll>
Require all granted //允许所有主机访问
</RequireAll>
</Directory>
</VirtualHost>
<VirtualHost *:80> //监听端口
DocumentRoot "/data/www.tong.com" //网站放置位置
ServerName www.tong.com //域名
ErrorLog "/var/log/httpd/www.tong.com-error_log" //错误日志放置位置
CustomLog "/var/log/httpd/www.tong.com-access_log" common //正确日志放置位置
<Directory "/data/www.tong.com"> //修改目录访问权限
<RequireAll>
Require all granted //允许所有主机访问
</RequireAll>
</Directory>
</VirtualHost>
3.3创建网页放置目录
[root@wyt1 conf.d]# mkdir -p /data/{www.wang.com,www.yi.com,www.tong.com} //创建目录和文件
[root@wyt1 conf.d]# ll /data/ //查看文件权限
total 0
drwxr-xr-x. 2 root root 6 May 9 23:25 www.tong.com
drwxr-xr-x. 2 root root 6 May 9 23:25 www.wang.com
drwxr-xr-x. 2 root root 6 May 9 23:25 www.yi.com
[root@wyt1 conf.d]# cd /data/
[root@wyt1 data]# ls //查看文件
www.tong.com www.wang.com www.yi.com
3.4生成网页及启动服务
[root@wyt1 data]# echo 'www.wang.com' > www.wang.com/index.html //生成网页
[root@wyt1 data]# echo 'www.yi.com' > www.yi.com/index.html //生成网页
[root@wyt1 data]# echo 'www.tong.com' > www.tong.com/index.html //生成网页
[root@wyt1 /]# tree /data //查看目录树
/data
├── www.tong.com
│ └── index.html
├── www.wang.com
│ └── index.html
└── www.yi.com
└── index.html
[root@wyt1 conf.d]# apachectl -t //查看语法
[root@wyt1 conf.d]# systemctl start httpd //启动服务
[root@wyt1 conf.d]# ss -antl //查看端口
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 :::80 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
3.5客户机配置映射
C:\windows\system32\drivers\etc\hosts //windos配置
192.168.232.128 www.wang.com
192.168.232.128 www.yi.com
192.168.232.128 www.tong.com
3.6验证
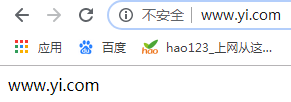
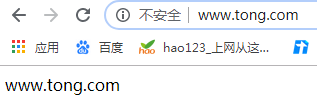
7.配置https步骤
1.生成证书
CA的配置文件:/etc/pki/tls/openssl.cnf
a) CA生成一对密钥
[root@wyt1 ~]# cd /etc/pki/CA
[root@wyt1 CA]# (umask 077;openssl genrsa -out private/cakey.pem 2048) //生成密钥,括号必须要
Generating RSA private key, 2048 bit long modulus
..............................................................................................................+++
..............................................................................................+++
e is 65537 (0x10001)
[root@wyt1 CA]# openssl rsa -in private/cakey.pem -pubout //提取公钥
b) CA生成自签署证书
[root@wyt1 CA]# openssl req -new -x509 -key private/cakey.pem -out cacert.pem -days 365 //生成自签署证书
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN
State or Province Name (full name) []:HB
Locality Name (eg, city) [Default City]:WH
Organization Name (eg, company) [Default Company Ltd]:www.a.com
Organizational Unit Name (eg, section) []:www.a.com
Common Name (eg, your name or your server's hostname) []:www.a.com
Email Address []:[email protected]
[root@wyt1 CA]# openssl x509 -text -in cacert.pem //读出cacert.pem证书的内容
[root@wyt1 CA]# ls
cacert.pem certs crl newcerts private
[root@wyt1 CA]# touch index.txt && echo 01 > serial // 生成一个空文件和一个里面写入内容的文件
[root@wyt1 CA]# ls
cacert.pem certs crl index.txt newcerts private serial
[root@wyt1 CA]# cat index.txt
[root@wyt1 CA]# cat serial
01
c) 客户端(例如httpd服务器)生成密钥
[root@wyt1 ~]# (umask 077;openssl genrsa -out httpd.key 2048) //生成密钥
Generating RSA private key, 2048 bit long modulus
.................................+++
......+++
e is 65537 (0x10001)
[root@wyt1 ~]# ls
anaconda-ks.cfg httpd.key
d) 客户端生成证书签署请求
[root@wyt1 ~]# openssl req -new -key httpd.key -days 365 -out httpd.csr //生成证书签署请求
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter '.', the field will be left blank.
-----
Country Name (2 letter code) [XX]:CN //输入国家
State or Province Name (full name) []:HB //输入省份
Locality Name (eg, city) [Default City]:WH //城市
Organization Name (eg, company) [Default Company Ltd]:www.a.com //域名
Organizational Unit Name (eg, section) []:www.a.com //域名
Common Name (eg, your name or your server's hostname) []:www.a.com //域名
Email Address []:[email protected] //邮箱
Please enter the following 'extra' attributes
to be sent with your certificate request
A challenge password []:
An optional company name []:
[root@wyt1 ~]# ls
anaconda-ks.cfg httpd.csr httpd.key
e) 客户端把证书签署请求文件发送给CA
[root@wyt1 ~]# scp httpd.csr root@CA端IP:/root //可不做此步骤,可以在同一台主机上面做
f) CA签署客户端提交上来的证书
[root@wyt1 ~]# openssl ca -in /root/httpd.csr -out httpd.crt -days 365 //签署客户端提交上来的证书
Using configuration from /etc/pki/tls/openssl.cnf
Check that the request matches the signature
Signature ok
Certificate Details:
Serial Number: 1 (0x1)
Validity
Not Before: May 12 18:18:43 2020 GMT
Not After : May 12 18:18:43 2021 GMT
Subject:
countryName = CN
stateOrProvinceName = HB
organizationName = www.a.com
organizationalUnitName = www.a.com
commonName = www.a.com
emailAddress = [email protected]
X509v3 extensions:
X509v3 Basic Constraints:
CA:FALSE
Netscape Comment:
OpenSSL Generated Certificate
X509v3 Subject Key Identifier:
72:64:B7:A1:AA:F9:B7:E0:D5:99:65:D0:B5:44:AA:DE:9F:96:C0:83
X509v3 Authority Key Identifier:
keyid:68:C3:F1:4B:C1:5D:85:05:34:EB:7D:AE:C7:17:25:37:95:4D:2C:33
Certificate is to be certified until May 12 18:18:43 2021 GMT (365 days)
Sign the certificate? [y/n]:y
1 out of 1 certificate requests certified, commit? [y/n]y
Write out database with 1 new entries
Data Base Updated
[root@wyt1 ~]# ls
anaconda-ks.cfg httpd.crt httpd.csr httpd.key
g) CA把签署好的证书httpd.crt发给客户端
[root@wyt1 ~]# scp httpd.crt root@客户端IP:/etc/httpd/ssl //可不做此步骤,可以在同一台主机上面做
2.安装mod_ssl模块
[root@wyt1 conf.d]# yum -y install mod_ssl
3.配置ssl及更改配置权限
[root@wyt1~]# cd /etc/httpd/conf.d
[root@wyt1 conf.d]# ls
autoindex.conf README userdir.conf
httpd-vhosts.conf ssl.conf welcome.conf
[root@wyt1 conf.d]# vim ssl.conf
<VirtualHost _default_:443> //默认443端口
# General setup for the virtual host, inherited from global configuration
DocumentRoot "/data/a" //修改存放目录
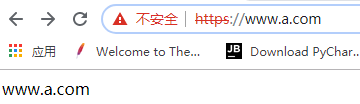
ServerName www.a.com:443 //修改域名
<Directory "/data/a">
require all granted //设置目录权限,所有主机可访问
</Directory>
# Server Certificate:
# Point SSLCertificateFile at a PEM encoded certificate. If
# the certificate is encrypted, then you will be prompted for a
# pass phrase. Note that a kill -HUP will prompt again. A new
# certificate can be generated using the genkey(1) command.
SSLCertificateFile /etc/httpd/ssl/httpd.crt //修改存放目录
# Server Private Key:
# If the key is not combined with the certificate, use this
# directive to point at the key file. Keep in mind that if
# you've both a RSA and a DSA private key you can configure
# both in parallel (to also allow the use of DSA ciphers, etc.)
SSLCertificateKeyFile /etc/httpd/ssl/httpd.key //修改存放目录
4.创建ssl证书存放目录
[root@wyt1~]# cd /etc/httpd
[root@wyt1 httpd]# ls
conf conf.d conf.modules.d logs modules run
[root@wyt1 httpd]# mkdir ssl //创建ssl证书存放目录
[root@wyt1 httpd]# ls
conf conf.d conf.modules.d logs modules run ssl
[root@wyt1 httpd]# cd ssl
[root@wyt1 ssl]# cp ~/httpd.* . //复制家目录CA证书到ssl文件中
[root@wyt1 ssl]# ls
httpd.crt httpd.csr httpd.key
5.重启服务及查看端口是否监听
[root@wyt1 conf.d]# systemctl restart httpd //重启服务
[root@wyt1 conf.d]# ss -antl
State Recv-Q Send-Q Local Address:Port Peer Address:Port
LISTEN 0 128 *:22 *:*
LISTEN 0 100 127.0.0.1:25 *:*
LISTEN 0 128 :::80 :::*
LISTEN 0 128 :::22 :::*
LISTEN 0 100 ::1:25 :::*
LISTEN 0 128 :::443 :::*
6.访问网站