一、安装openvpn服务
0、环境说明
公司希望搭建自己的VPN,方便员工远程办公,保障了数据传输安全,又没有足够的预算经费,可以使用开源vpn软件openvpn搭建自己的VPN服务,只需要使用一台服务器,占用少量的资源即可完成此需求。
本博客安装环境操作系统版本为centos7.6
[root@test2 ~]# cat /etc/redhat-release
CentOS Linux release 7.9.2009 (Core)
1、更新软件包
#yum -y update
2、安装epel扩展源
yum -y install epel-release
3、安装openvpn和easy-rsa
#yum -y install openvpn easy-rsa
4、复制easy-rsa文件
[root@test2 ~]# cp -r /usr/share/easy-rsa/ /etc/openvpn/easy-rsa
[root@test2 ~]# cd /etc/openvpn/easy-rsa
[root@test2 easy-rsa]# ll
total 0
lrwxrwxrwx. 1 root root 5 Dec 20 21:57 3 -> 3.0.8
lrwxrwxrwx. 1 root root 5 Dec 20 21:57 3.0 -> 3.0.8
drwxr-xr-x. 3 root root 66 Dec 20 21:57 3.0.8
[root@test2 easy-rsa]# rm -rf 3 3.0
[root@test2 easy-rsa]# cd 3.0.8
[root@test2 3.0.8]# find / -type f -name “vars.example” | xargs -i cp {} . && mv vars.example vars
二、证书制作
1、CA证书制作
1)、创建一个新的 PKI 和 CA
[root@test2 3.0.8]# ./easyrsa init-pki
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/3.0.8/vars
init-pki complete; you may now create a CA or requests.
Your newly created PKI dir is: /etc/openvpn/easy-rsa/3.0.8/pki
2)、创建新的CA,不使用密码
通过nopass设置不使用密码,如果需要设置密码取消改参数即可,如果设置了密码,在后面制作服务端证书和客户端证书的时候需要输入CA证书密码。
[root@test2 3.0.8]# ./easyrsa build-ca nopass
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating RSA private key, 2048 bit long modulus
…+++
…+++
e is 65537 (0x10001)
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [Easy-RSA CA]:test2 [此处输入名称后回车]CA creation complete and you may now import and sign cert requests.
Your new CA certificate file for publishing is at:
/etc/openvpn/easy-rsa/3.0.8/pki/ca.crt
2、服务端证书制作
1)、创建服务端证书
[root@test2 3.0.8]# ./easyrsa gen-req server nopass
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating a 2048 bit RSA private key
…+++
…+++
writing new private key to ‘/etc/openvpn/easy-rsa/3.0.8/pki/easy-rsa-76043.gohT64/tmp.yuQxiN’
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [server]:Keypair and certificate request completed. Your files are:
req: /etc/openvpn/easy-rsa/3.0.8/pki/reqs/server.req
key: /etc/openvpn/easy-rsa/3.0.8/pki/private/server.key
2)、签约服务端证书
[root@test2 3.0.8]# ./easyrsa sign server server
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017You are about to sign the following certificate.
Please check over the details shown below for accuracy. Note that this request
has not been cryptographically verified. Please be sure it came from a trusted
source or that you have verified the request checksum with the sender.Request subject, to be signed as a server certificate for 825 days:
subject=
commonName = serverType the word ‘yes’ to continue, or any other input to abort.
Confirm request details: yes
Using configuration from /etc/openvpn/easy-rsa/3.0.8/pki/easy-rsa-76179.WMc3sQ/tmp.isxUth
Check that the request matches the signature
Signature ok
The Subject’s Distinguished Name is as follows
commonName :ASN.1 12:‘server’
Certificate is to be certified until Mar 26 06:09:33 2023 GMT (825 days)Write out database with 1 new entries
Data Base UpdatedCertificate created at: /etc/openvpn/easy-rsa/3.0.8/pki/issued/server.crt
3)、创建交换密钥 Diffie-Hellman
[root@test2 3.0.8]# ./easyrsa gen-dh
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating DH parameters, 2048 bit long safe prime, generator 2
This is going to take a long time
…
如提示,此处会持续一段时间,需要1-3分钟
…
DH parameters of size 2048 created at /etc/openvpn/easy-rsa/3.0.8/pki/dh.pem
4)、整理证书
[root@test2 3.0.8]# cd /etc/openvpn/server/
[root@test2 server]# cp …/easy-rsa/3.0.8/pki/dh.pem .
[root@test2 server]# cp …/easy-rsa/3.0.8/pki/ca.crt .
[root@test2 server]# cp …/easy-rsa/3.0.8/pki/issued/server.crt .
[root@test2 server]# cp …/easy-rsa/3.0.8/pki/private/server.key .
3、创建客户端证书
1)、创建客户端证书
[root@test2 3.0.8]# ./easyrsa gen-req clienttest nopass
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Generating a 2048 bit RSA private key
…+++
…+++
writing new private key to ‘/etc/openvpn/easy-rsa/3.0.8/pki/easy-rsa-77836.9Cbgtc/tmp.ueZGma’
-----
You are about to be asked to enter information that will be incorporated
into your certificate request.
What you are about to enter is what is called a Distinguished Name or a DN.
There are quite a few fields but you can leave some blank
For some fields there will be a default value,
If you enter ‘.’, the field will be left blank.
-----
Common Name (eg: your user, host, or server name) [clienttest]:Keypair and certificate request completed. Your files are:
req: /etc/openvpn/easy-rsa/3.0.8/pki/reqs/clienttest.req
key: /etc/openvpn/easy-rsa/3.0.8/pki/private/clienttest.key
2)、签约客户端证书
[root@test2 3.0.8]# ./easyrsa sign client clienttest
Note: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017You are about to sign the following certificate.
Please check over the details shown below for accuracy. Note that this request
has not been cryptographically verified. Please be sure it came from a trusted
source or that you have verified the request checksum with the sender.Request subject, to be signed as a client certificate for 825 days:
subject=
commonName = clienttestType the word ‘yes’ to continue, or any other input to abort.
Confirm request details: yes
Using configuration from /etc/openvpn/easy-rsa/3.0.8/pki/easy-rsa-77882.lvODqq/tmp.J3yPdl
Check that the request matches the signature
Signature ok
The Subject’s Distinguished Name is as follows
commonName :ASN.1 12:‘clienttest’
Certificate is to be certified until Mar 26 06:34:07 2023 GMT (825 days)Write out database with 1 new entries
Data Base UpdatedCertificate created at: /etc/openvpn/easy-rsa/3.0.8/pki/issued/clienttest.crt
三、openvpn服务配置及启动
1)、配置openvpn服务配置文件
[root@test2 3.0.8]# cd /etc/openvpn/
#vi /etc/openvpn/server.conf
将如下配置添加到server.conf配置文件后保存
#自定义服务端口
port 18443
#自定义服务协议,可选TCP或者UDP,建议UDP
proto udp
dev tun
ca /etc/openvpn/server/ca.crt
cert /etc/openvpn/server/server.crt
key /etc/openvpn/server/server.key
crl-verify /etc/openvpn/easy-rsa/3.0.8/pki/crl.pem
dh /etc/openvpn/server/dh.pem
ifconfig-pool-persist /etc/openvpn/ipp.txt
##自己定义openvpn地址池
server 172.16.7.0 255.255.255.0
##内网路由根据需要添加
push “route 192.168.0.0 255.255.255.0”
push “dhcp-option DNS 114.114.114.114”
push “dhcp-option DNS 8.8.8.8”
client-to-client
keepalive 20 120
comp-lzo
tls-auth ta.key 0
user openvpn
group openvpn
persist-key
persist-tun
status openvpn-status.log
log-append openvpn.log
verb 1
mute 20
2)、防止VPN被DDOS攻击,生成ta.key
[root@test2 openvpn]# openvpn --genkey --secret ./server/ta.key
[root@test2 openvpn]# ll server
total 24
-rw-------. 1 root root 1147 Dec 20 22:18 ca.crt
-rw-------. 1 root root 424 Dec 20 22:18 dh.pem
-rw-------. 1 root root 4519 Dec 20 22:18 server.crt
-rw-------. 1 root root 1704 Dec 20 22:18 server.key
-rw-------. 1 root root 636 Dec 20 22:46 ta.key
3)、启动openvpn服务
[root@test2 openvpn]# systemctl start openvpn@server
[root@test2 openvpn]# systemctl status openvpn@server
● [email protected] - OpenVPN Robust And Highly Flexible Tunneling Application On server
Loaded: loaded (/usr/lib/systemd/system/[email protected]; disabled; vendor preset: disabled)
Active: active (running) since Sun 2020-12-20 23:19:43 PST; 17s ago
Main PID: 81477 (openvpn)
Status: “Initialization Sequence Completed”
CGroup: /system.slice/system-openvpn.slice/[email protected]
└─81477 /usr/sbin/openvpn --cd /etc/openvpn/ --config server.confDec 20 23:19:43 test2 systemd[1]: Starting OpenVPN Robust And Highly Flexible Tunneling Application On server…
Dec 20 23:19:43 test2 systemd[1]: Started OpenVPN Robust And Highly Flexible Tunneling Application On server.
四、客户端安装及使用
1、window客户端安装
1)、下载openvpn客户端
2)、解压后运行exe安装程序
3)、重命名虚拟网卡
安装完成后会多出一个虚拟网卡,将改网卡重命名为openvpn
4)、从服务器下载证书
将服务器上的ca.crt、ta.key、clienttest.crt、clienttest.key文件下载下来,并拷贝至C:\Program Files\OpenVPN\config目录下,需要管理员权限。
5)、创建客户端配置文件
用记事本创建文本文件myvpn.ovpn,将如下配置添加到配置文件,然后将配置文件拷贝至C:\Program Files\OpenVPN\config目录下
client
dev tun
proto udp
remote 192.168.0.125 18443 #按照服务器配置设置,IP地址为映射到公网后的地址
#dev-node配置请参考如下条件配置:
#windows请去掉注释填写控制面板的虚拟网卡名称,建议英文字符组成
#linux与MAC客户端请注释
dev-node openvpn #虚拟网卡名称
resolv-retry infinite
nobind
persist-key
persist-tun
ca ca.crt
cert clienttest.crt
key clienttest.key
remote-cert-tls server
tls-auth ta.key 1
cipher BF-CBC
comp-lzo
verb 3
mute 20
6)、启动客户端程序并连接
我的openvpn连接配置如下图

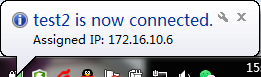
7)、连接成功后提示如下
2、linux客户安装
1)、执行以下命令安装OpenVPN客户端。
#yum install -y openvpn
2)、将client账户文件上传
将下载的证书解压拷贝到 /etc/openvpn/conf/目录。
3)、启动Openvpn客户端软件。
openvpn --config /etc/openvpn/conf/config.ovpn –daemon
配置文件参考window客户端安装步骤
四、QA
1、启动报错crl.pem文件找不到
报错信息如下
Options error: --crl-verify fails with ‘/etc/openvpn/easy-rsa/3.0.8/pki/crl.pem’: No such file or directory (errno=2)
解决方法:
生产crl.pem文件,此文件用于核验注销的client用户
[root@test2 3.0.8]# ./easyrsa gen-crlNote: using Easy-RSA configuration from: /etc/openvpn/easy-rsa/3.0.8/vars
Using SSL: openssl OpenSSL 1.0.2k-fips 26 Jan 2017
Using configuration from /etc/openvpn/easy-rsa/3.0.8/pki/easy-rsa-79518.a1A5dA/tmp.uUBPOAAn updated CRL has been created.
CRL file: /etc/openvpn/easy-rsa/3.0.8/pki/crl.pem
2、启动时报错Socket bind failed
报错信息如下:
TCP/UDP: Socket bind failed on local address [AF_INET][undef]:18443: Permission denied (errno=13)
解决方案:
关闭selinux安全策略
[root@test2 openvpn]# setenforce 0
[root@test2 openvpn]# getenforce
Permissive
五、NAT模式
建议openvpn使用路由模式,路由模式需要openvpn地址池网段在内网有路由,VPN连接后以VPN地址访问内网服务器,明确记录访问IP,可以在VPN客户账户创建时指定固定IP地址,内网安全更加安全可控。NAT模式情况下均转换为openvpn服务器地址访问内网,异常操作需要定位人员时比较困难。如果配置NAT模式,需要启用iptables进行源nat转换。
1、安装iptables
#yum -y install iptables iptables-services
2、开启转发
[root@test2 3.0.8]# vi /etc/sysctl.conf
net.ipv4.ip_forward = 1
[root@test2 3.0.8]# sysctl -p
3、参照截图配置转发和NAT策略

4、启用iptables防火墙
#systemctl restart iptables.service