一、网络环境介绍
USG防火墙调试IPSEC ***的时候发现官方的配置手册有些问题,所以详细整理下实施过程出现的问题及解决方法。
网络情况简介:有10个分支机构,只有总部可以确认为固定IP,分支机构无法确认,有的固定,有的用ADSL。本案例用2个分支介绍。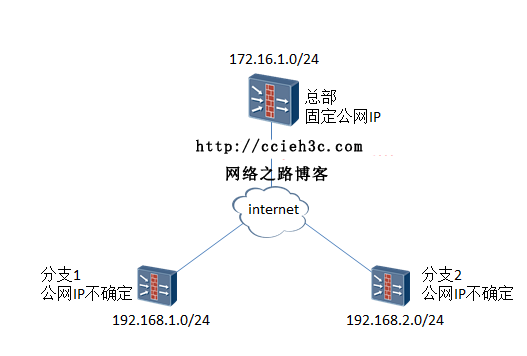
了解了客户的基本网络状况后开始跟客户商量设计调试方案,选用IPSEC野蛮模式组网。
在实施过程中发现以下问题:
1、 配置手册中IPSEC ***配置实例不完善,NAT部分没有写(要阻止***之间的数据访问做NAT转换),导致配置的时候不知道问题出在哪,在NAT中完善了转换策略后,问题解决。
2、 因为野蛮模式配置是用ike local-name进行验证的,初步在IKE协商参数配置中加入了remote-name这项,配置完成后IPSEC ***建立成功,分支和总部用内网IP可以直接访问,第二天总部防火墙重启了一次后***怎么都建立不起来,打400后发现在IKE协商参数配置中使用了remote-name出现问题,导致***连接不上,去掉remote-name后问题解决。
二、配置过程详细介绍
下面详细介绍下配置过程,总部内网用的172.16.1.0/24网段,其它分支采用192.168.X.X/24网段。防火墙的软件版本都是V100R005。
总部配置
1、 配置本地IKE本地用户名
ike local-name qndc
2、 配置ACL
acl number 3001 创建序号3001的高级访问控制列表
rule 5 permit ip source 172.16.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
总部到分支1的内网网段***触发策略
rule 10 permit ip source 172.16.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
总部到分支2的内网网段***触发策略
3、 配置IKE安全提议
ike proposal 10 创建名称为10的IKE安全提议
authentication-algorithm md5 选择加密的算法为md5
4、 配置IKE PEER
ike peer a 创建名称为a的IKE PEER
exchange-mode aggressive 模式选择野蛮模式
pre-shared-key ccieh3c.taobao.com IKE协商的密钥为123456
ike-proposal 10 绑定IKE安全提议
undo version 2 选择V1的版本
local-id-type name 使用野蛮模式的IKE local-name验证
nat traversal 打开NAT穿越
5、 创建IPSEC安全提议
ipsec proposal tran1 创建名称为tran1的IPSEC安全提议
esp authentication-algorithm sha1 选择安全算法为哈希算法sha1
6、 配置IPSEC安全策略模板
ipsec policy-template map 1 创建名称为map的策略模板
security acl 3001 绑定触发ACL
ike-peer a 选择前面创建的 ike-peer a
proposal tran1 选择前面创建的IPSEC安全提议tran1
7、 创建IPSEC安全策略
ipsec policy map1 1 isakmp template map 创建名称为map1的IPSEC安全策略绑定map策略模板
8、 在外网接口上应用IPSEC安全策略
interface Ethernet0/0/0
ip address 119.97.240.106 255.255.255.248
ipsec policy map1 应用map1的IPSEC ***策略
9、 配置目的地址为192.168.X.X/16网段不做NAT转换;这步不配的话内网数据直接做NAT转换了,不会通过***隧道,那么前面的配置就白做了。
nat-policy interzone trust untrust outbound 进入NAT配置视图
policy 1 策略1(这是优先级,数字越小越优先)
action no-nat 不做NAT转换
policy destination 192.168.0.0 0.0.255.255 目的地址为192.168.0.0/16不做NAT转换
policy 2 策略2
action source-nat 基于源地址的转换
policy source 172.16.1.0 0.0.0.255 源地址为172.16.1.0/24做NAT转换
easy-ip Ethernet0/0/0 转换的外网地址为Ethernet0/0/0的接口地址
#
一定要注意策略的优先级,反了就没有作用了。
(二)分之机构配置
分之机构1的配置详解
1、 配置本地IKE本地用户名
ike local-name fenzhi1
2、 配置ACL
acl number 3001 创建序号3001的高级访问控制列表
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
分之1到总部内网网段的***触发策略
3、 配置IKE安全提议
ike proposal 10 创建名称为10的IKE安全提议
authentication-algorithm md5 选择加密的算法为md5
4、 配置IKE PEER
ike peer a 创建名称为a的IKE PEER
exchange-mode aggressive 模式选择野蛮模式
pre-shared-key ccieh3c.taobao.com IKE协商的密钥为123456
ike-proposal 10 绑定IKE安全提议
undo version 2 选择V1的版本
local-id-type name 使用野蛮模式的IKE local-name验证
remote-address 119.97.240.106 总部的外网地址
nat traversal 打开NAT穿越
5、 创建IPSEC安全提议
ipsec proposal tran1 创建名称为tran1的IPSEC安全提议
esp authentication-algorithm sha1 选择安全算法为哈希算法sha1
6、 配置IPSEC安全策略
ipsec policy map1 10 isakmp 创建名称为map1的策略
security acl 3001 绑定触发ACL
ike-peer a 选择前面创建的 ike-peer a
proposal tran1 选择前面创建的IPSEC安全提议tran1
7、 在外网接口上应用IPSEC安全策略
interface Ethernet0/0/0
ip address 59.175.185.126 255.255.255.0
ipsec policy map1 应用map1的IPSEC ***策略
8、 NAT策略配置。
nat-policy interzone trust untrust outbound 进入NAT配置视图
policy 1 策略1(这是优先级,数字越小越优先)
action no-nat 不做NAT转换
policy destination 172.16.0.0 0.0.255.255 目的地址为172.16.0.0/16不做NAT转换
policy 2 策略2
action source-nat 基于源地址的转换
policy source 192.168.1.0 0.0.0.255 源地址为192.168.1.0/24做NAT转换
easy-ip Ethernet0/0/0 转换的外网地址为Ethernet0/0/0的接口地址
#
分之2的配置参照分之1, ACL源地址改成本地内网网段,IKE本地名称重新命名;其它主要***主要配置都一样
(三)配置总结
总部和分之的配置区别在于,总部采用IPSEC安全策略模板绑定到外网接口,分之机构使用安全策略。
完成所有配置后使用可以display ike sa、display ipsec sa 查看ike安全联盟状态和ipsec安全联盟状态;
三、详细配置文档(现网成功稳定运行配置文档)
1、总部的配置文档
#
ike local-name qndc
#
firewall packet-filter default permit interzone local trust direction inbound
firewall packet-filter default permit interzone local trust direction outbound
firewall packet-filter default permit interzone local untrust direction inbound
firewall packet-filter default permit interzone local untrust direction outbound
firewall packet-filter default permit interzone local dmz direction inbound
firewall packet-filter default permit interzone local dmz direction outbound
firewall packet-filter default permit interzone trust untrust direction inbound
firewall packet-filter default permit interzone trust untrust direction outbound
firewall packet-filter default permit interzone trust dmz direction inbound
firewall packet-filter default permit interzone trust dmz direction outbound
firewall packet-filter default permit interzone dmz untrust direction inbound
firewall packet-filter default permit interzone dmz untrust direction outbound
#
acl number 3001
rule 5 permit ip source 172.16.1.0 0.0.0.255 destination 192.168.1.0 0.0.0.255
rule 10 permit ip source 172.16.1.0 0.0.0.255 destination 192.168.2.0 0.0.0.255
#
ike proposal 10
authentication-algorithm md5
#
ike peer a
exchange-mode aggressive
pre-shared-key ccieh3c.taobao.com
ike-proposal 10
undo version 2
local-id-type name
nat traversal
#
ipsec proposal tran1
esp authentication-algorithm sha1
#
ipsec policy-template map 1
security acl 3001
ike-peer a
proposal tran1
#
ipsec policy map1 1 isakmp template map
#
interface Vlanif1
ip address 172.16.1.1 255.255.255.0
#
interface Cellular5/0/0
link-protocol ppp
#
interface Ethernet0/0/0
ip address 119.97.240.106 255.255.255.248
ipsec policy map1
#
interface Ethernet1/0/0
portswitch
port link-type access
#
interface Ethernet1/0/1
portswitch
port link-type access
#
interface Ethernet1/0/2
portswitch
port link-type access
#
interface Ethernet1/0/3
portswitch
port link-type access
#
interface Ethernet1/0/4
portswitch
port link-type access
#
interface Ethernet1/0/5
portswitch
port link-type access
#
interface Ethernet1/0/6
portswitch
port link-type access
#
interface Ethernet1/0/7
portswitch
port link-type access
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
add interface Ethernet1/0/0
add interface Ethernet1/0/1
add interface Ethernet1/0/2
add interface Ethernet1/0/3
add interface Ethernet1/0/4
add interface Ethernet1/0/5
add interface Ethernet1/0/6
add interface Ethernet1/0/7
add interface Vlanif1
#
firewall zone untrust
set priority 5
add interface Ethernet0/0/0
#
ip route-static 0.0.0.0 0.0.0.0 119.97.240.105
#
nat-policy interzone trust untrust outbound
policy 1
action no-nat
policy destination 182.168.0.0 0.0.255.255
policy 2
action source-nat
policy source 172.16.1.0 0.0.0.255
easy-ip Ethernet0/0/0
#
2、分之1的配置
#
ike local-name fenzhi-1
#
firewall packet-filter default permit interzone local trust direction inbound
firewall packet-filter default permit interzone local trust direction outbound
firewall packet-filter default permit interzone local untrust direction inbound
firewall packet-filter default permit interzone local untrust direction outbound
firewall packet-filter default permit interzone local dmz direction inbound
firewall packet-filter default permit interzone local dmz direction outbound
firewall packet-filter default permit interzone trust untrust direction inbound
firewall packet-filter default permit interzone trust untrust direction outbound
firewall packet-filter default permit interzone trust dmz direction inbound
firewall packet-filter default permit interzone trust dmz direction outbound
firewall packet-filter default permit interzone dmz untrust direction inbound
firewall packet-filter default permit interzone dmz untrust direction outbound
#
l2fwdfast enable
#
acl number 3001
rule 5 permit ip source 192.168.1.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
#
ike proposal 10
authentication-algorithm md5
#
ike peer a
exchange-mode aggressive
pre-shared-key ccieh3c.taobao.com
ike-proposal 10
undo version 2
local-id-type name
remote-address 119.97.240.106
nat traversal
#
ipsec proposal tran1
esp authentication-algorithm sha1
#
ipsec policy map1 10 isakmp
security acl 3001
ike-peer a
proposal tran1
#
interface Vlanif1
ip address 192.168.1.1 255.255.255.0
#
interface Cellular5/0/0
link-protocol ppp
#
interface Ethernet0/0/0
ip address 59.175.185.126 255.255.255.0
ipsec policy map1
#
interface Ethernet1/0/0
portswitch
port link-type access
#
interface Ethernet1/0/1
portswitch
port link-type access
#
interface Ethernet1/0/2
portswitch
port link-type access
#
interface Ethernet1/0/3
portswitch
port link-type access
#
interface Ethernet1/0/4
portswitch
port link-type access
#
interface Ethernet1/0/5
portswitch
port link-type access
#
interface Ethernet1/0/6
portswitch
port link-type access
#
interface Ethernet1/0/7
portswitch
port link-type access
#
interface Ethernet2/0/0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
detect ftp
add interface Ethernet1/0/0
add interface Ethernet1/0/1
add interface Ethernet1/0/2
add interface Ethernet1/0/3
add interface Ethernet1/0/4
add interface Ethernet1/0/5
add interface Ethernet1/0/6
add interface Ethernet1/0/7
add interface Vlanif1
#
firewall zone untrust
set priority 5
detect ftp
add interface Ethernet0/0/0
add interface Ethernet2/0/0
#
ip route-static 0.0.0.0 0.0.0.0 59.175.185.1
#
nat-policy interzone trust untrust outbound
policy 1
action no-nat
policy destination 172.16.0.0 0.0.255.255
policy 2
action source-nat
policy source 192.168.1.0 0.0.0.255
easy-ip Ethernet0/0/0
#
3、 分之2的配置文档
#
ike local-name fenzhi-2
#
firewall packet-filter default permit interzone local trust direction inbound
firewall packet-filter default permit interzone local trust direction outbound
firewall packet-filter default permit interzone local untrust direction inbound
firewall packet-filter default permit interzone local untrust direction outbound
firewall packet-filter default permit interzone local dmz direction inbound
firewall packet-filter default permit interzone local dmz direction outbound
firewall packet-filter default permit interzone trust untrust direction inbound
firewall packet-filter default permit interzone trust untrust direction outbound
firewall packet-filter default permit interzone trust dmz direction inbound
firewall packet-filter default permit interzone trust dmz direction outbound
firewall packet-filter default permit interzone dmz untrust direction inbound
firewall packet-filter default permit interzone dmz untrust direction outbound
#
l2fwdfast enable
#
acl number 3001
rule 5 permit ip source 192.168.2.0 0.0.0.255 destination 172.16.1.0 0.0.0.255
#
ike proposal 10
authentication-algorithm md5
#
ike peer a
exchange-mode aggressive
pre-shared-key 123456
ike-proposal 10
undo version 2
local-id-type name
remote-address 119.97.240.106
nat traversal
#
ipsec proposal tran1
esp authentication-algorithm sha1
#
ipsec policy map1 10 isakmp
security acl 3001
ike-peer a
proposal tran1
#
interface Vlanif1
ip address 192.168.2.1 255.255.255.0
#
interface Cellular5/0/0
link-protocol ppp
#
interface Ethernet0/0/0
ip address 172.16.235.50 255.255.255.0
ipsec policy map1
#
interface Ethernet1/0/0
portswitch
port link-type access
#
interface Ethernet1/0/1
portswitch
port link-type access
#
interface Ethernet1/0/2
portswitch
port link-type access
#
interface Ethernet1/0/3
portswitch
port link-type access
#
interface Ethernet1/0/4
portswitch
port link-type access
#
interface Ethernet1/0/5
portswitch
port link-type access
#
interface Ethernet1/0/6
portswitch
port link-type access
#
interface Ethernet1/0/7
portswitch
port link-type access
#
interface Ethernet2/0/0
#
interface NULL0
#
firewall zone local
set priority 100
#
firewall zone trust
set priority 85
detect ftp
add interface Ethernet1/0/0
add interface Ethernet1/0/1
add interface Ethernet1/0/2
add interface Ethernet1/0/3
add interface Ethernet1/0/4
add interface Ethernet1/0/5
add interface Ethernet1/0/6
add interface Ethernet1/0/7
add interface Vlanif1
#
firewall zone untrust
set priority 5
detect ftp
add interface Ethernet0/0/0
add interface Ethernet2/0/0
#
ip route-static 0.0.0.0 0.0.0.0 172.16.235.1
#
nat-policy interzone trust untrust outbound
policy 1
action no-nat
policy destination 172.16.1.0 0.0.0.255
policy 2
action source-nat
policy source 192.168.2.0 0.0.0.255
easy-ip Ethernet0/0/0
#
本文转载于公众号:网络之路博客