1 限定某个目录禁止解析
比喻网站有个目录可以上传图片的,别人通过一些手段上传php文件,那么就会解析该文件,这样容易被人上传木马文件,进而获取系统的权限,进行信息获取
其中SQL注入也是一种入侵,不过可以通过提交的端口做特殊符号的过滤,可以阻断这样入侵
核心配置文件内容
[root@linux01 ~]# vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
<VirtualHost *:80>
DocumentRoot "/data/wwwroot/111.com"
ServerName 111.com
ServerAlias www.111.com aaa.com
<Directory /data/wwwroot/111.com/upload>
php_admin_flag engine off
</Directory>
ErrorLog "logs/111.com-error_log"
CustomLog "logs/111.com-access_%Y%m%d.log 86400" combined
</VirtualHost>
或者另外一种方法:
<VirtualHost *:80>
DocumentRoot "/data/wwwroot/111.com"
ServerName 111.com
ServerAlias www.111.com aaa.com
<Directory /data/wwwroot/111.com/upload>
<FilesMatch (.*)\.php(.*)>
Order allow, deny
Deny from all
</FilesMatch>
</Directory>
ErrorLog "logs/111.com-error_log"
CustomLog "logs/111.com-access_%Y%m%d.log 86400" combined
</VirtualHost>
创建文件:
[root@linux01 111.com]# mkdir upload
[root@linux01 111.com]# vim upload/1.php
<?php
phpinfo();
?>
重新加载配置文件:
[root@linux01 ~]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@linux01 ~]# /usr/local/apache2.4/bin/apachectl graceful
curl测试:
[root@linux01 ~]# curl -x127.0.0.1:80 111.com/upload/1.php
<?php
phpinfo();
?>
只能返回源码,无法解析内容
2 限定user_agent
需求:网站受到攻击了(CC攻击),就是被别人控制的肉鸡攻击站点,网站就会挂掉
CC攻击有一个特别明显的特征是:user_agent都是一样的固定的
所以可以通过限制user_agent,可以阻止攻击
[root@linux01 ~]# vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
<VirtualHost *:80>
DocumentRoot "/data/wwwroot/111.com"
ServerName 111.com
ServerAlias www.111.com aaa.com
<IfModule mod_rewrite.c>
RewriteEngine on
RewriteCond %{HTTP_USER_AGENT} .*curl.* [NC,OR] //OR表示或的意思
RewriteCond %{HTTP_USER_AGENT} .*baidu.com.* [NC] //NC表示忽略大小写
RewriteRule .* - [F] //F表示forbidden的意思
</IfModule>
ErrorLog "logs/111.com-error_log"
CustomLog "logs/111.com-access_%Y%m%d.log 86400" combined
</VirtualHost>
重新加载配置文件:
[root@linux01 ~]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@linux01 ~]# /usr/local/apache2.4/bin/apachectl graceful
curl测试:
[root@linux01 ~]# curl -x127.0.0.1:80 111.com -I
HTTP/1.1 403 Forbidden
Date: Sun, 18 Nov 2018 02:00:32 GMT
Server: Apache/2.4.34 (Unix) PHP/5.6.32
Content-Type: text/html; charset=iso-8859-1
返回码是403,因为配置指定user-agent是curl不允许访问
自定义一个user-agent为hello:
[root@linux01 ~]# curl -A "hello" -x127.0.0.1:80 111.com -I
HTTP/1.1 200 OK
Date: Sun, 18 Nov 2018 02:03:30 GMT
Server: Apache/2.4.34 (Unix) PHP/5.6.32
Last-Modified: Wed, 14 Nov 2018 03:20:20 GMT
ETag: "8-57a9769fef5ef"
Accept-Ranges: bytes
Content-Length: 8
Content-Type: text/html
返回码是200,成功访问
3 php相关配置
查看php配置文件位置
/usr/local/php/bin/php -i|grep -i "loaded configuration file" (另外的办法就是在网站的访问文件创建一个1.php文件里添加函数phpinfo();,在浏览器访问即可查到)
[root@linux01 ~]# /usr/local/php/bin/php -i|grep -i "loaded configuration file"
Loaded Configuration File => /usr/local/php/etc/php.ini
PHP Warning: Unknown: It is not safe to rely on the system's timezone settings. You are *required* to use the date.timezone setting or the date_default_timezone_set() function. In case you used any of those methods and you are still getting this warning, you most likely misspelled the timezone identifier. We selected the timezone 'UTC' for now, but please set date.timezone to select your timezone. in Unknown on line 0
编辑php配置文件:
[root@linux01 ~]# vim /usr/local/php/etc/php.ini
date.timezone=Asia/Shanghai
disable_functions //禁止函数,eval(一句话木马使用这个函数解析)
eval,assert,popen,passthru,escapeshellarg,escapeshellcmd,passthru,exec,system,chroot,scandir,chgrp,chown,escapeshellcmd,escapeshellarg,shell_exec,proc_get_status,ini_alter,ini_restore,dl,pfsockopen,openlog,syslog,readlink,symlink,leak,popepassthru,stream_socket_server,popen,proc_open,proc_close,phpinfo
重新加载配置文件:
[root@linux01 ~]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@linux01 ~]# /usr/local/apache2.4/bin/apachectl graceful
curl测试:(需要把虚拟主机的配置文件的限制user-agent的配置去掉)
[root@linux01 ~]# curl -x127.0.0.1:80 111.com/index.php
<br />
<b>Warning</b>: phpinfo() has been disabled for security reasons in <b>/data/wwwroot/111.com/index.php</b> on line <b>2</b><br />
提示警告:phpinfo函数失效
在生产环境中,则不能把错误信息输出到浏览器上,暴露了文件的路
径,容易被黑客入侵
将错误信息关闭
[root@linux01 ~]# vim /usr/local/php/etc/php.ini
display_errors=Off
curl测试:
[root@linux01 ~]# curl -x127.0.0.1:80 111.com/index.php
没有错误信息显示了
开启错误日志记录,方便问题的查找
[root@linux01 ~]# vim /usr/local/php/etc/php.ini
log_errors=On
error_log=/tmp/php_error_log
设置错误日志输出级别:测试环境E_ALL所有的警告,提示信息都记录,实际生产环境使用E_ALL & ~E_NOTICE(生产环境出现的E_NOTICE的频率很高,但不是错误)
error_reporting =E_ALL
重新加载配置文件:
[root@linux01 ~]# /usr/local/apache2.4/bin/apachectl -t
Syntax OK
[root@linux01 ~]# /usr/local/apache2.4/bin/apachectl graceful
curl测试:
[root@linux01 ~]# curl -x127.0.0.1:80 111.com/index.php
查看错误日志文件:
[root@linux01 ~]# cat /tmp/php_errors.log
[18-Nov-2018 02:42:14 UTC] PHP Warning: phpinfo() has been disabled for security reasons in /data/wwwroot/111.com/index.php on line 2
注意:如果错误日志没有生成,需要手动创建,在设置777权限就行
创建一个测试文件:
[root@linux01 111.com]# vim 2.php
<?php
echo hello;
heelelelelle
curl测试:
[root@linux01 ~]# curl -x127.0.0.1:80 111.com/2.php -I
HTTP/1.0 500 Internal Server Error
Date: Sun, 18 Nov 2018 02:50:08 GMT
Server: Apache/2.4.34 (Unix) PHP/5.6.32
X-Powered-By: PHP/5.6.32
Connection: close
Content-Type: text/html; charset=UTF-8
查看错误日志文件:
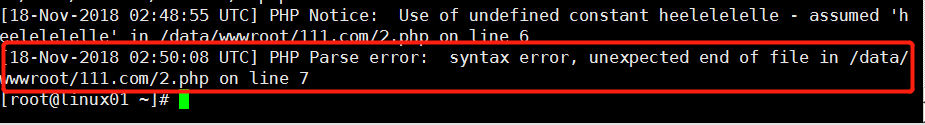
提示出现语法错误
需求:如果站点有AB两个目录,如果有黑客入侵了网站A目录,进而就会入侵B目录
所以可以对网站目录做隔离,与入侵目录隔离
open_basedir安全选项;做站点的隔离作用:隔离目录
open_basedir =/data/wwwroot/111.com/admin:/tmp///安全配置,tmp目录表示是上传文件的时候,临时存放地方
作用:只能访问/data/wwwroot/111.com/admin目录,而/data/wwwroot/111.com的目录无法访问了,做了隔离
curl测试:(admin目录)
[root@linux01 ~]# curl -x127.0.0.1:80 111.com/admin/index.php -I
HTTP/1.1 200 OK
Date: Sun, 18 Nov 2018 03:03:17 GMT
Server: Apache/2.4.34 (Unix) PHP/5.6.32
X-Powered-By: PHP/5.6.32
Content-Type: text/html; charset=UTF-8
返回状态码200,访问成功
curl测试:(111.com目录)
[root@linux01 ~]# curl -x127.0.0.1:80 111.com/index.php -I
HTTP/1.0 500 Internal Server Error
Date: Sun, 18 Nov 2018 03:03:24 GMT
Server: Apache/2.4.34 (Unix) PHP/5.6.32
X-Powered-By: PHP/5.6.32
Connection: close
Content-Type: text/html; charset=UTF-8
返回状态码500,无法访问
查看错误日志:
[root@linux01 ~]# cat /tmp/php_errors.log
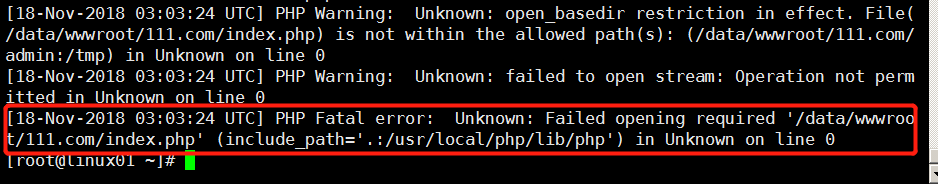
因为在php.ini配置文件中,只能对所有的站点,不能单个站点配置;不过可以在不同的虚拟主机里做单个站点配置
虚拟主机的配置文件:
[root@linux01 ~]# vim /usr/local/apache2.4/conf/extra/httpd-vhosts.conf
比如:
<VirtualHost *:80>
DocumentRoot "/data/wwwroot/abc.com"
ServerName abc.com
ServerAlias www.abc.com
php_admin_value open_basedir "/data/wwwroot/abc.com:/tmp/" (在对应的虚拟主机配置open_basedir)
ErrorLog "logs/abc.com-error_log"
CustomLog "logs/abc.com-access_log" common
</VirtualHost>
php_admin_value 这个参数可以定义php.ini里面的参数,还可以定义
error_log, log_errors, display_errors, error_reporting等等
扩展
apache开启压缩 http://ask.apelearn.com/question/5528
apache2.2到2.4配置文件变更 http://ask.apelearn.com/question/7292
apache options参数 http://ask.apelearn.com/question/1051
apache禁止trace或track防止xss http://ask.apelearn.com/question/1045
apache 配置https 支持ssl http://ask.apelearn.com/question/1029