基础知识
函数传参存在两种方式,一种是通过栈,一种是通过寄存器。对于x64体系结构,如果函数参数不大于6个时,使用寄存器传参,对于函数参数大于6个的函数,前六个参数使用寄存器传递,后面的使用栈传递。参数传递的规律是固定的,即前6个参数从左到右放入寄存器: rdi, rsi, rdx, rcx, r8, r9,后面的依次从 “右向左” 放入栈中。
例如:
H(a, b, c, d, e, f, g, h);
a->%rdi, b->%rsi, c->%rdx, d->%rcx, e->%r8, f->%r9
h->8(%rsp)
g->(%rsp)
实验验证
源码示例
1 #include <stdio.h>
2 #include <stdlib.h>
3 int test_pass_parm(int a, int b, int c, int d, int e, int f, int g, int h)
4 {
5 printf("a:%0x, b:%0x c:%0x d:%0x e:%0x f:%0x g;%0x h:%0x\n", a,b,c,d,e,f,g,h);
6 return 0;
7 }
8 int main(int argc, char **argv)
9 {
10 int a = 1, b= 2, c=3, d = 4, e =5, f=6, g= 7, h =8;
11 test_pass_parm(a,b,c,d,e,f,g,h);
12 return 0;
13 }
使用 gcc pass_parm.c -o pass_parm -g生成可执行程序 pass_parm.
反汇编 pass_parm
从中我们取出来main函数以及test_pass_parm 汇编进行分析验证。
main 汇编分析
119 int main(int argc, char **argv)
120 {
121 40057b: 55 push %rbp
122 40057c: 48 89 e5 mov %rsp,%rbp
123 40057f: 48 83 ec 40 sub $0x40,%rsp //rsp栈指针下移0x40(64)个字节
124 400583: 89 7d dc mov %edi,-0x24(%rbp) // main函数的第一个参数argc放置在距离栈底0x24字节处
125 400586: 48 89 75 d0 mov %rsi,-0x30(%rbp) // main函数的第一个参数argv放置在距离栈底0x30字节处
126 int a = 1, b= 2, c=3, d = 4, e =5, f=6, g= 7, h =8;
127 40058a: c7 45 fc 01 00 00 00 movl $0x1,-0x4(%rbp) //变量a
128 400591: c7 45 f8 02 00 00 00 movl $0x2,-0x8(%rbp)//变量b
129 400598: c7 45 f4 03 00 00 00 movl $0x3,-0xc(%rbp)//变量c
130 40059f: c7 45 f0 04 00 00 00 movl $0x4,-0x10(%rbp)//变量d
131 4005a6: c7 45 ec 05 00 00 00 movl $0x5,-0x14(%rbp)//变量e
132 4005ad: c7 45 e8 06 00 00 00 movl $0x6,-0x18(%rbp)//变量f
133 4005b4: c7 45 e4 07 00 00 00 movl $0x7,-0x1c(%rbp) //变量g
134 4005bb: c7 45 e0 08 00 00 00 movl $0x8,-0x20(%rbp) //变量h
135 // 以上汇编将main函数的局部a, b, c, d, e, f, g, h变量从左到右依次入栈
136 test_pass_parm(a,b,c,d,e,f,g,h);
137 4005c2: 44 8b 4d e8 mov -0x18(%rbp),%r9d //传送-0x18(%rbp)(变量f) 位置的值到r9寄存器中
138 4005c6: 44 8b 45 ec mov -0x14(%rbp),%r8d //传送-0x14(%rbp)(变量e) 位置的值到r8寄存器中
139 4005ca: 8b 4d f0 mov -0x10(%rbp),%ecx //传送-0x10(%rbp)(变量d) 位置的值到cx寄存器中
140 4005cd: 8b 55 f4 mov -0xc(%rbp),%edx //传送-0xc(%rbp)(变量c) 位置的值到dx寄存器中
141 4005d0: 8b 75 f8 mov -0x8(%rbp),%esi //传送-0x8(%rbp)(变量b) 位置的值到si寄存器中
142 4005d3: 8b 45 fc mov -0x4(%rbp),%eax //暂存-0x4(%rbp)(变量a) 位置的值到ax寄存器中
143 4005d6: 8b 7d e0 mov -0x20(%rbp),%edi //传送-0x20(%rbp)(变量h) 位置的值到di寄存器中中转
144 4005d9: 89 7c 24 08 mov %edi,0x8(%rsp) //传送di寄存器的值到(变量h) 0x8(%rsp)位置
145 4005dd: 8b 7d e4 mov -0x1c(%rbp),%edi //传送-0x1c(%rbp)(变量g) 位置的值到di寄存器中中转
146 4005e0: 89 3c 24 mov %edi,(%rsp) //传送di寄存器的值到(变量g) (%rsp)位置
147 4005e3: 89 c7 mov %eax,%edi //最后将ax寄存器保存的a变量的值传送到di寄存器
148 // 以上汇编准备传给test_pass_parm函数的参数,然后调用test_pass_parm
149 4005e5: e8 33 ff ff ff callq 40051d <test_pass_parm>
150 return 0;
151 4005ea: b8 00 00 00 00 mov $0x0,%eax
152 }
153 4005ef: c9 leaveq
154 4005f0: c3 retq
155 4005f1: 66 2e 0f 1f 84 00 00 nopw %cs:0x0(%rax,%rax,1)
156 4005f8: 00 00 00
157 4005fb: 0f 1f 44 00 00 nopl 0x0(%rax,%rax,1)
test_pass_parm 汇编分析
82 int test_pass_parm(int a, int b, int c, int d, int e, int f, int g, int h)
83 {
84 40051d: 55 push %rbp
85 40051e: 48 89 e5 mov %rsp,%rbp
86 400521: 48 83 ec 30 sub $0x30,%rsp
87 400525: 89 7d fc mov %edi,-0x4(%rbp) //a
88 400528: 89 75 f8 mov %esi,-0x8(%rbp) //b
89 40052b: 89 55 f4 mov %edx,-0xc(%rbp) //c
90 40052e: 89 4d f0 mov %ecx,-0x10(%rbp) //d
91 400531: 44 89 45 ec mov %r8d,-0x14(%rbp) //e
92 400535: 44 89 4d e8 mov %r9d,-0x18(%rbp) /f
93 //从寄存器恢复实参到当前函数的栈中
94 printf("a:%0x, b:%0x c:%0x d:%0x e:%0x f:%0x g;%0x h:%0x\n", a,b,c,d,e,f,g,h);
95 400539: 44 8b 45 ec mov -0x14(%rbp),%r8d
96 40053d: 8b 7d f0 mov -0x10(%rbp),%edi
97 400540: 8b 4d f4 mov -0xc(%rbp),%ecx
98 400543: 8b 55 f8 mov -0x8(%rbp),%edx
99 400546: 8b 45 fc mov -0x4(%rbp),%eax
100 400549: 8b 75 18 mov 0x18(%rbp),%esi //0x18(%rbp)的地址是上一个函数的栈顶位置 + 8,从这拿出h
101 40054c: 89 74 24 10 mov %esi,0x10(%rsp)
102 400550: 8b 75 10 mov 0x10(%rbp),%esi //0x10(%rbp)的地址是上一个函数的栈顶位置,从这拿出g
103 400553: 89 74 24 08 mov %esi,0x8(%rsp)
104 400557: 8b 75 e8 mov -0x18(%rbp),%esi
105 40055a: 89 34 24 mov %esi,(%rsp)
106 40055d: 45 89 c1 mov %r8d,%r9d
107 400560: 41 89 f8 mov %edi,%r8d
108 400563: 89 c6 mov %eax,%esi
109 400565: bf 90 06 40 00 mov $0x400690,%edi
110 40056a: b8 00 00 00 00 mov $0x0,%eax
111 // 以上汇编准备传给printf函数的参数,然后调用printf
112 40056f: e8 8c fe ff ff callq 400400 <printf@plt>
113 return 0;
114 400574: b8 00 00 00 00 mov $0x0,%eax
115 }
116 400579: c9 leaveq
117 40057a: c3 retq
实验
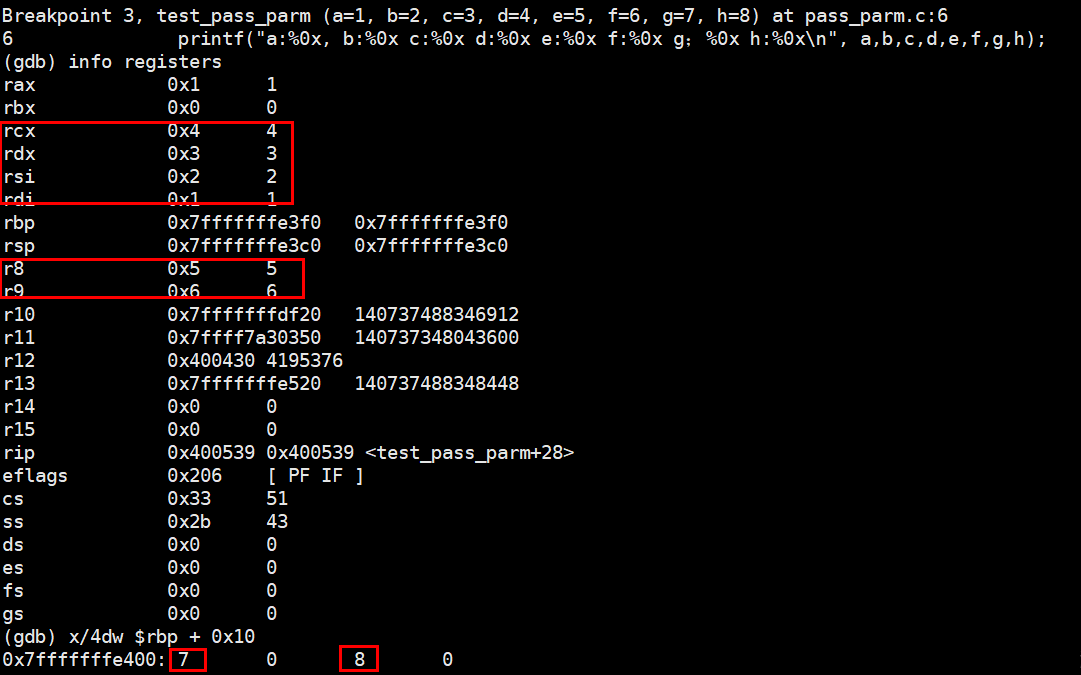
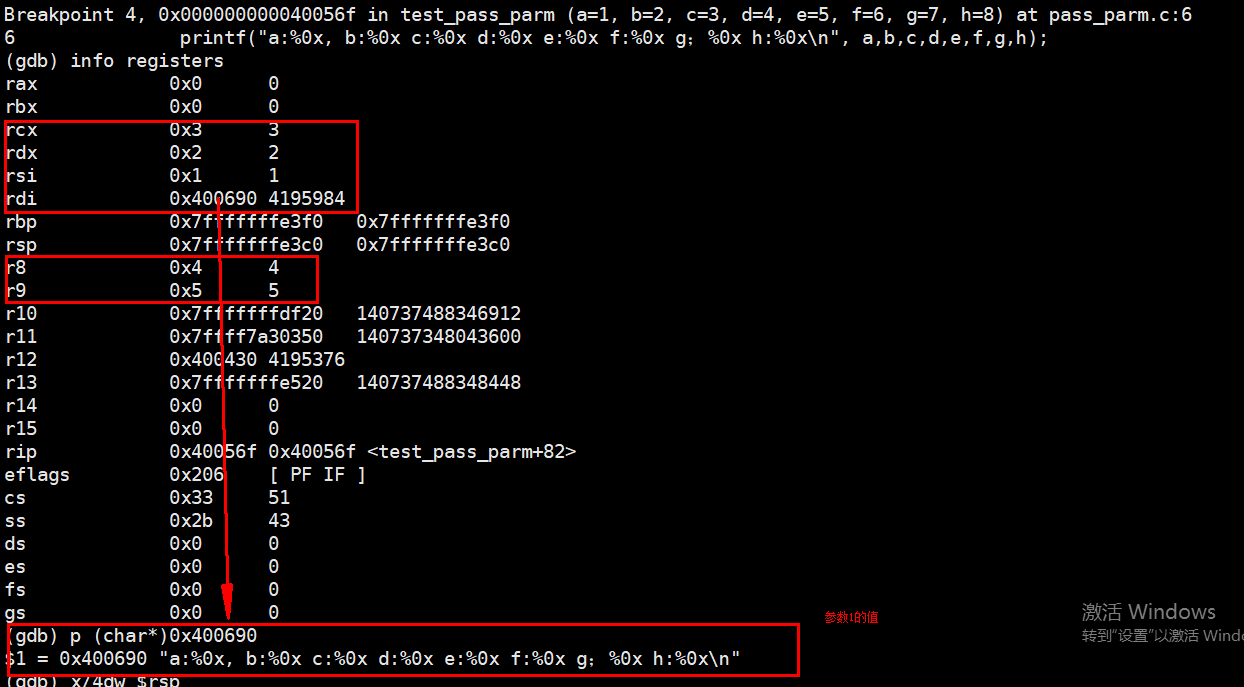
使用gdb进行汇编代码调试,分别在执行汇编指令的0x4005c2、0x4005e5、0x400539、0x40056f处设置断点,查看寄存器的值以及函数栈帧中的值,验证分析的结果。
设置断点
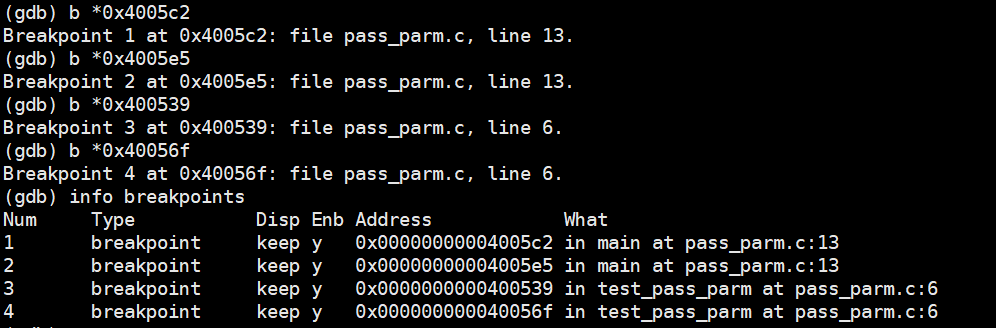
断点1处的栈数值
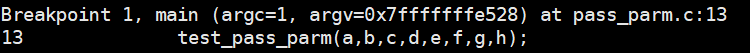
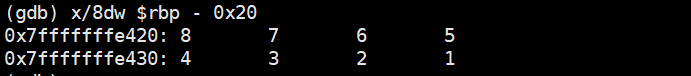
断点2处的栈数值以及寄存器值
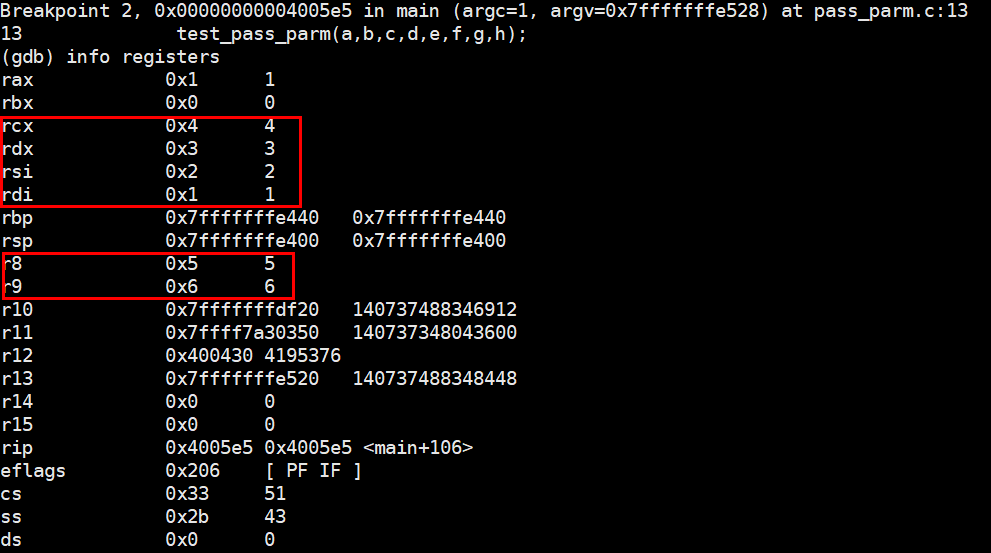
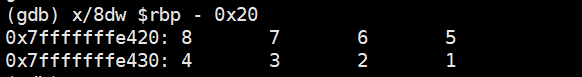
断点3处的栈数值以及寄存器值
断点4处的栈数值以及寄存器值

结论
实验结果完全验证了所分析的结果,从这次实践中可以更好地了解函数参数的传递过程以及函数调用所引起的堆栈变化,完整的调试过程见附录。
附录 完整汇编与调试过程
完整汇编代码
[root@localhost test]# objdump -j .text -S pass_parm > a.txt
[root@localhost test]# nl a.txt
1 pass_parm: 文件格式 elf64-x86-64
2 Disassembly of section .text:
3 0000000000400430 <_start>:
4 400430: 31 ed xor %ebp,%ebp
5 400432: 49 89 d1 mov %rdx,%r9
6 400435: 5e pop %rsi
7 400436: 48 89 e2 mov %rsp,%rdx
8 400439: 48 83 e4 f0 and $0xfffffffffffffff0,%rsp
9 40043d: 50 push %rax
10 40043e: 54 push %rsp
11 40043f: 49 c7 c0 70 06 40 00 mov $0x400670,%r8
12 400446: 48 c7 c1 00 06 40 00 mov $0x400600,%rcx
13 40044d: 48 c7 c7 7b 05 40 00 mov $0x40057b,%rdi
14 400454: e8 b7 ff ff ff callq 400410 <__libc_start_main@plt>
15 400459: f4 hlt
16 40045a: 66 0f 1f 44 00 00 nopw 0x0(%rax,%rax,1)
17 0000000000400460
:
18 400460: b8 37 10 60 00 mov $0x601037,%eax
19 400465: 55 push %rbp
20 400466: 48 2d 30 10 60 00 sub $0x601030,%rax
21 40046c: 48 83 f8 0e cmp $0xe,%rax
22 400470: 48 89 e5 mov %rsp,%rbp
23 400473: 77 02 ja 400477
24 400475: 5d pop %rbp
25 400476: c3 retq
26 400477: b8 00 00 00 00 mov $0x0,%eax
27 40047c: 48 85 c0 test %rax,%rax
28 40047f: 74 f4 je 400475
29 400481: 5d pop %rbp
30 400482: bf 30 10 60 00 mov $0x601030,%edi
31 400487: ff e0 jmpq *%rax
32 400489: 0f 1f 80 00 00 00 00 nopl 0x0(%rax)
33 0000000000400490
:
34 400490: b8 30 10 60 00 mov $0x601030,%eax
35 400495: 55 push %rbp
36 400496: 48 2d 30 10 60 00 sub $0x601030,%rax
37 40049c: 48 c1 f8 03 sar $0x3,%rax
38 4004a0: 48 89 e5 mov %rsp,%rbp
39 4004a3: 48 89 c2 mov %rax,%rdx
40 4004a6: 48 c1 ea 3f shr $0x3f,%rdx
41 4004aa: 48 01 d0 add %rdx,%rax
42 4004ad: 48 d1 f8 sar %rax
43 4004b0: 75 02 jne 4004b4
44 4004b2: 5d pop %rbp 45 4004b3: c3 retq 46 4004b4: ba 00 00 00 00 mov $0x0,%edx 47 4004b9: 48 85 d2 test %rdx,%rdx 48 4004bc: 74 f4 je 4004b2
49 4004be: 5d pop %rbp 50 4004bf: 48 89 c6 mov %rax,%rsi 51 4004c2: bf 30 10 60 00 mov $0x601030,%edi 52 4004c7: ff e2 jmpq *%rdx 53 4004c9: 0f 1f 80 00 00 00 00 nopl 0x0(%rax) 54 00000000004004d0 <__do_global_dtors_aux>: 55 4004d0: 80 3d 55 0b 20 00 00 cmpb $0x0,0x200b55(%rip) # 60102c <_edata> 56 4004d7: 75 11 jne 4004ea <__do_global_dtors_aux+0x1a> 57 4004d9: 55 push %rbp 58 4004da: 48 89 e5 mov %rsp,%rbp 59 4004dd: e8 7e ff ff ff callq 400460
60 4004e2: 5d pop %rbp 61 4004e3: c6 05 42 0b 20 00 01 movb $0x1,0x200b42(%rip) # 60102c <_edata> 62 4004ea: f3 c3 repz retq 63 4004ec: 0f 1f 40 00 nopl 0x0(%rax) 64 00000000004004f0
: 65 4004f0: 48 83 3d 28 09 20 00 cmpq $0x0,0x200928(%rip) # 600e20 <__JCR_END__> 66 4004f7: 00 67 4004f8: 74 1e je 400518
68 4004fa: b8 00 00 00 00 mov $0x0,%eax 69 4004ff: 48 85 c0 test %rax,%rax 70 400502: 74 14 je 400518
71 400504: 55 push %rbp 72 400505: bf 20 0e 60 00 mov $0x600e20,%edi 73 40050a: 48 89 e5 mov %rsp,%rbp 74 40050d: ff d0 callq *%rax 75 40050f: 5d pop %rbp 76 400510: e9 7b ff ff ff jmpq 400490
77 400515: 0f 1f 00 nopl (%rax) 78 400518: e9 73 ff ff ff jmpq 400490
79 000000000040051d
: 80 #include
81 #include
82 int test_pass_parm(int a, int b, int c, int d, int e, int f, int g, int h) 83 { 84 40051d: 55 push %rbp 85 40051e: 48 89 e5 mov %rsp,%rbp 86 400521: 48 83 ec 30 sub $0x30,%rsp 87 400525: 89 7d fc mov %edi,-0x4(%rbp) 88 400528: 89 75 f8 mov %esi,-0x8(%rbp) 89 40052b: 89 55 f4 mov %edx,-0xc(%rbp) 90 40052e: 89 4d f0 mov %ecx,-0x10(%rbp) 91 400531: 44 89 45 ec mov %r8d,-0x14(%rbp) 92 400535: 44 89 4d e8 mov %r9d,-0x18(%rbp) 93 printf("a:%0x, b:%0x c:%0x d:%0x e:%0x f:%0x g;%0x h:%0x\n", a,b,c,d,e,f,g,h); 94 400539: 44 8b 45 ec mov -0x14(%rbp),%r8d 95 40053d: 8b 7d f0 mov -0x10(%rbp),%edi 96 400540: 8b 4d f4 mov -0xc(%rbp),%ecx 97 400543: 8b 55 f8 mov -0x8(%rbp),%edx 98 400546: 8b 45 fc mov -0x4(%rbp),%eax 99 400549: 8b 75 18 mov 0x18(%rbp),%esi 100 40054c: 89 74 24 10 mov %esi,0x10(%rsp) 101 400550: 8b 75 10 mov 0x10(%rbp),%esi 102 400553: 89 74 24 08 mov %esi,0x8(%rsp) 103 400557: 8b 75 e8 mov -0x18(%rbp),%esi 104 40055a: 89 34 24 mov %esi,(%rsp) 105 40055d: 45 89 c1 mov %r8d,%r9d 106 400560: 41 89 f8 mov %edi,%r8d 107 400563: 89 c6 mov %eax,%esi 108 400565: bf 90 06 40 00 mov $0x400690,%edi 109 40056a: b8 00 00 00 00 mov $0x0,%eax 110 40056f: e8 8c fe ff ff callq 400400
111 return 0; 112 400574: b8 00 00 00 00 mov $0x0,%eax 113 } 114 400579: c9 leaveq 115 40057a: c3 retq 116 000000000040057b
: 117 int main(int argc, char **argv) 118 { 119 40057b: 55 push %rbp 120 40057c: 48 89 e5 mov %rsp,%rbp 121 40057f: 48 83 ec 40 sub $0x40,%rsp 122 400583: 89 7d dc mov %edi,-0x24(%rbp) 123 400586: 48 89 75 d0 mov %rsi,-0x30(%rbp) 124 int a = 1, b= 2, c=3, d = 4, e =5, f=6, g= 7, h =8; 125 40058a: c7 45 fc 01 00 00 00 movl $0x1,-0x4(%rbp) 126 400591: c7 45 f8 02 00 00 00 movl $0x2,-0x8(%rbp) 127 400598: c7 45 f4 03 00 00 00 movl $0x3,-0xc(%rbp) 128 40059f: c7 45 f0 04 00 00 00 movl $0x4,-0x10(%rbp) 129 4005a6: c7 45 ec 05 00 00 00 movl $0x5,-0x14(%rbp) 130 4005ad: c7 45 e8 06 00 00 00 movl $0x6,-0x18(%rbp) 131 4005b4: c7 45 e4 07 00 00 00 movl $0x7,-0x1c(%rbp) 132 4005bb: c7 45 e0 08 00 00 00 movl $0x8,-0x20(%rbp) 133 test_pass_parm(a,b,c,d,e,f,g,h); 134 4005c2: 44 8b 4d e8 mov -0x18(%rbp),%r9d 135 4005c6: 44 8b 45 ec mov -0x14(%rbp),%r8d 136 4005ca: 8b 4d f0 mov -0x10(%rbp),%ecx 137 4005cd: 8b 55 f4 mov -0xc(%rbp),%edx 138 4005d0: 8b 75 f8 mov -0x8(%rbp),%esi 139 4005d3: 8b 45 fc mov -0x4(%rbp),%eax 140 4005d6: 8b 7d e0 mov -0x20(%rbp),%edi 141 4005d9: 89 7c 24 08 mov %edi,0x8(%rsp) 142 4005dd: 8b 7d e4 mov -0x1c(%rbp),%edi 143 4005e0: 89 3c 24 mov %edi,(%rsp) 144 4005e3: 89 c7 mov %eax,%edi 145 4005e5: e8 33 ff ff ff callq 40051d
146 return 0; 147 4005ea: b8 00 00 00 00 mov $0x0,%eax 148 } 149 4005ef: c9 leaveq 150 4005f0: c3 retq 151 4005f1: 66 2e 0f 1f 84 00 00 nopw %cs:0x0(%rax,%rax,1) 152 4005f8: 00 00 00 153 4005fb: 0f 1f 44 00 00 nopl 0x0(%rax,%rax,1) 154 0000000000400600 <__libc_csu_init>: 155 400600: 41 57 push %r15 156 400602: 41 89 ff mov %edi,%r15d 157 400605: 41 56 push %r14 158 400607: 49 89 f6 mov %rsi,%r14 159 40060a: 41 55 push %r13 160 40060c: 49 89 d5 mov %rdx,%r13 161 40060f: 41 54 push %r12 162 400611: 4c 8d 25 f8 07 20 00 lea 0x2007f8(%rip),%r12 # 600e10 <__frame_dummy_init_array_entry> 163 400618: 55 push %rbp 164 400619: 48 8d 2d f8 07 20 00 lea 0x2007f8(%rip),%rbp # 600e18 <__init_array_end> 165 400620: 53 push %rbx 166 400621: 4c 29 e5 sub %r12,%rbp 167 400624: 31 db xor %ebx,%ebx 168 400626: 48 c1 fd 03 sar $0x3,%rbp 169 40062a: 48 83 ec 08 sub $0x8,%rsp 170 40062e: e8 95 fd ff ff callq 4003c8 <_init> 171 400633: 48 85 ed test %rbp,%rbp 172 400636: 74 1e je 400656 <__libc_csu_init+0x56> 173 400638: 0f 1f 84 00 00 00 00 nopl 0x0(%rax,%rax,1) 174 40063f: 00 175 400640: 4c 89 ea mov %r13,%rdx 176 400643: 4c 89 f6 mov %r14,%rsi 177 400646: 44 89 ff mov %r15d,%edi 178 400649: 41 ff 14 dc callq *(%r12,%rbx,8) 179 40064d: 48 83 c3 01 add $0x1,%rbx 180 400651: 48 39 eb cmp %rbp,%rbx 181 400654: 75 ea jne 400640 <__libc_csu_init+0x40> 182 400656: 48 83 c4 08 add $0x8,%rsp 183 40065a: 5b pop %rbx 184 40065b: 5d pop %rbp 185 40065c: 41 5c pop %r12 186 40065e: 41 5d pop %r13 187 400660: 41 5e pop %r14 188 400662: 41 5f pop %r15 189 400664: c3 retq 190 400665: 90 nop 191 400666: 66 2e 0f 1f 84 00 00 nopw %cs:0x0(%rax,%rax,1) 192 40066d: 00 00 00 193 0000000000400670 <__libc_csu_fini>: 194 400670: f3 c3 repz retq
完整调试过程
[root@kfzhao test]# gdb pass_parm
GNU gdb (GDB) Red Hat Enterprise Linux 7.6.1-110.el7
Copyright (C) 2013 Free Software Foundation, Inc.
License GPLv3+: GNU GPL version 3 or later
This is free software: you are free to change and redistribute it.
There is NO WARRANTY, to the extent permitted by law. Type "show copying"
and "show warranty" for details.
This GDB was configured as "x86_64-redhat-linux-gnu".
For bug reporting instructions, please see:
eflags 0x206 [ PF IF ]
cs 0x33 51
ss 0x2b 43
ds 0x0 0
es 0x0 0
fs 0x0 0
gs 0x0 0
(gdb) x/8dw $rbp - 0x20
0x7fffffffe420: 8 7 6 5
0x7fffffffe430: 4 3 2 1
(gdb) c
Continuing.
Breakpoint 2, 0x00000000004005e5 in main (argc=1, argv=0x7fffffffe528) at pass_parm.c:13
13 test_pass_parm(a,b,c,d,e,f,g,h);
(gdb) info registers
rax 0x1 1
rbx 0x0 0
rcx 0x4 4
rdx 0x3 3
rsi 0x2 2
rdi 0x1 1
rbp 0x7fffffffe440 0x7fffffffe440
rsp 0x7fffffffe400 0x7fffffffe400
r8 0x5 5
r9 0x6 6
r10 0x7fffffffdf20 140737488346912
r11 0x7ffff7a30350 140737348043600
r12 0x400430 4195376
r13 0x7fffffffe520 140737488348448
r14 0x0 0
r15 0x0 0
rip 0x4005e5 0x4005e5
eflags 0x206 [ PF IF ]
cs 0x33 51
ss 0x2b 43
ds 0x0 0
es 0x0 0
fs 0x0 0
gs 0x0 0
(gdb) x/8dw $rbp - 0x20
0x7fffffffe420: 8 7 6 5
0x7fffffffe430: 4 3 2 1
(gdb) c
Continuing.
Breakpoint 3, test_pass_parm (a=1, b=2, c=3, d=4, e=5, f=6, g=7, h=8) at pass_parm.c:6
6 printf("a:%0x, b:%0x c:%0x d:%0x e:%0x f:%0x g;%0x h:%0x\n", a,b,c,d,e,f,g,h);
(gdb) info registers
rax 0x1 1
rbx 0x0 0
rcx 0x4 4
rdx 0x3 3
rsi 0x2 2
rdi 0x1 1
rbp 0x7fffffffe3f0 0x7fffffffe3f0
rsp 0x7fffffffe3c0 0x7fffffffe3c0
r8 0x5 5
r9 0x6 6
r10 0x7fffffffdf20 140737488346912
r11 0x7ffff7a30350 140737348043600
r12 0x400430 4195376
r13 0x7fffffffe520 140737488348448
r14 0x0 0
r15 0x0 0
rip 0x400539 0x400539
eflags 0x206 [ PF IF ]
cs 0x33 51
ss 0x2b 43
ds 0x0 0
es 0x0 0
fs 0x0 0
gs 0x0 0
(gdb) x/4dw $rbp + 0x10
0x7fffffffe400: 7 0 8 0
(gdb) c
Continuing.
Breakpoint 4, 0x000000000040056f in test_pass_parm (a=1, b=2, c=3, d=4, e=5, f=6, g=7, h=8) at pass_parm.c:6
6 printf("a:%0x, b:%0x c:%0x d:%0x e:%0x f:%0x g;%0x h:%0x\n", a,b,c,d,e,f,g,h);
(gdb) info registers
rax 0x0 0
rbx 0x0 0
rcx 0x3 3
rdx 0x2 2
rsi 0x1 1
rdi 0x400690 4195984
rbp 0x7fffffffe3f0 0x7fffffffe3f0
rsp 0x7fffffffe3c0 0x7fffffffe3c0
r8 0x4 4
r9 0x5 5
r10 0x7fffffffdf20 140737488346912
r11 0x7ffff7a30350 140737348043600
r12 0x400430 4195376
r13 0x7fffffffe520 140737488348448
r14 0x0 0
r15 0x0 0
rip 0x40056f 0x40056f
eflags 0x206 [ PF IF ] cs 0x33 51 ss 0x2b 43 ds 0x0 0 es 0x0 0 fs 0x0 0 gs 0x0 0 (gdb) p (char*)0x400690 $1 = 0x400690 "a:%0x, b:%0x c:%0x d:%0x e:%0x f:%0x g;%0x h:%0x\n" (gdb) x/6dw $rsp 0x7fffffffe3c0: 6 32767 7 32767 0x7fffffffe3d0: 8 0 (gdb)