前言:之前https://blog.csdn.net/sinat_20059415/article/details/99686537 看WiFi如何分辨出不同加密方式的AP? 中提到“加密方式大概是从扫描结果中的ie解析出来放在一个叫做capabilities里的,后续上面判断加密方式就简单判断下是否包含特定加密方式的字符串就好了。”抓个包看下
1.probe request & response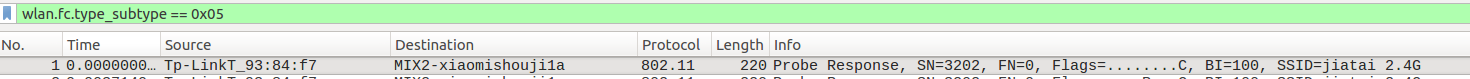
用wireshark看下有啥
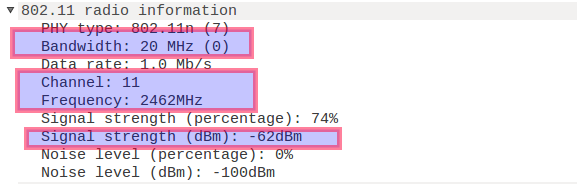
1.1 arrival time

1.2 radio informatin
1.3 probe response
主要显示了mac地址

1.4 wireless LAN
可以看到至少有ssid channel和加密方式

这个psk应该也是wireshark根据特定字段解析出来的,结合之前的梳理代码看下
// RSNE format (size unit: byte)
//
// | Element ID | Length | Version | Group Data Cipher Suite |
// 1 1 2 4
// | Pairwise Cipher Suite Count | Pairwise Cipher Suite List |
// 2 4 * m
// | AKM Suite Count | AKM Suite List | RSN Capabilities |
// 2 4 * n 2
// | PMKID Count | PMKID List | Group Management Cipher Suite |
// 2 16 * s 4
//
// Note: InformationElement.bytes has 'Element ID' and 'Length'
// stripped off already
private void parseRsnElement(InformationElement ie) {
ByteBuffer buf = ByteBuffer.wrap(ie.bytes).order(ByteOrder.LITTLE_ENDIAN);
try {
// version
if (buf.getShort() != RSNE_VERSION) {
// incorrect version
return;
}
// found the RSNE IE, hence start building the capability string
protocol.add(ScanResult.PROTOCOL_WPA2);
// group data cipher suite
groupCipher.add(parseRsnCipher(buf.getInt()));
// pairwise cipher suite count
short cipherCount = buf.getShort();
ArrayList<Integer> rsnPairwiseCipher = new ArrayList<>();
// pairwise cipher suite list
for (int i = 0; i < cipherCount; i++) {
rsnPairwiseCipher.add(parseRsnCipher(buf.getInt()));
}
pairwiseCipher.add(rsnPairwiseCipher);
// AKM
// AKM suite count
short akmCount = buf.getShort();
ArrayList<Integer> rsnKeyManagement = new ArrayList<>();
for (int i = 0; i < akmCount; i++) {
int akm = buf.getInt();
switch (akm) {
case WPA2_AKM_EAP:
rsnKeyManagement.add(ScanResult.KEY_MGMT_EAP);
break;
case WPA2_AKM_PSK:
rsnKeyManagement.add(ScanResult.KEY_MGMT_PSK);
break;
case WPA2_AKM_FT_EAP:
rsnKeyManagement.add(ScanResult.KEY_MGMT_FT_EAP);
break;
case WPA2_AKM_FT_PSK:
rsnKeyManagement.add(ScanResult.KEY_MGMT_FT_PSK);
break;
case WPA2_AKM_EAP_SHA256:
rsnKeyManagement.add(ScanResult.KEY_MGMT_EAP_SHA256);
break;
case WPA2_AKM_PSK_SHA256:
rsnKeyManagement.add(ScanResult.KEY_MGMT_PSK_SHA256);
break;
default:
// do nothing
break;
}
}
// Default AKM
if (rsnKeyManagement.isEmpty()) {
rsnKeyManagement.add(ScanResult.KEY_MGMT_EAP);
}
keyManagement.add(rsnKeyManagement);
} catch (BufferUnderflowException e) {
Log.e("IE_Capabilities", "Couldn't parse RSNE, buffer underflow");
}
}这边是解析的一个
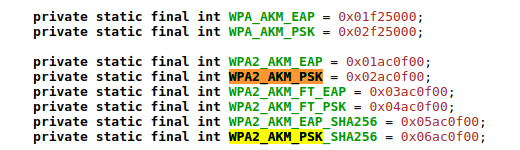
与报文对应

是反过来的
OUI:OUI认证应该是对应的wpa2
结合起来就是wpa2_psk的加密方式
2.beacon
待续,没抓到。。。尴尬
3.过滤器转载
https://my.oschina.net/665544/blog/1647001
| 帧类型 |
过滤器语法 |
| Management frame |
wlan.fc.type == 0 |
| Control frame |
wlan.fc.type == 1 |
| Data frame |
wlan.fc.type == 2 |
| Association request |
wlan.fc.type_subtype == 0x00 |
| Association response |
wlan.fc.type_subtype == 0x01 |
| Reassociation request |
wlan.fc.type_subtype == 0x02 |
| Reassociation response |
wlan.fc.type_subtype == 0x03 |
| Probe request |
wlan.fc.type_subtype == 0x04 |
| Probe response |
wlan.fc.type_subtype == 0x05 |
| Beacon |
wlan.fc.type_subtype == 0x08 |
| Disassociate |
wlan.fc.type_subtype == 0x0A |
| Authentication |
wlan.fc.type_subtype == 0x0B |
| Deauthentication |
wlan.fc.type_subtype == 0x0C |
| Action frame |
wlan.fc.type_subtype == 0x0D |
| Block ACK requests |
wlan.fc.type_subtype == 0x18 |
| Block ACK |
wlan.fc.type_subtype == 0x19 |
| Power save poll |
wlan.fc.type_subtype == 0x1A |
| Request to send |
wlan.fc.type_subtype == 0x1B |
| Clear to send |
wlan.fc.type_subtype == 0x1C |
| ACK |
wlan.fc.type_subtype == 0x1D |
| Contention free period end |
wlan.fc.type_subtype == 0x1E |
| NULL data |
wlan.fc.type_subtype == 0x24 |
| QoS data |
wlan.fc.type_subtype == 0x28 |
| Null QoS data |
wlan.fc.type_subtype == 0x2C |
4.总结
与之前总结基本一致,加密方式其实就是从datagram的特定字段解析出来的,结合抓包可以定位是解析的
RSN Information的AKM字段,里面包含认证和类型两个小字段,比如wpa2+psk

PS:
The RSN information element was brought out by the IEEE 802.11i Task Group. RSN stands for Robust Security Network and it made AES cipher mandatory with the use of Robust Security Network.
高级加密标准(Advanced Encryption Standard: AES)
IEEE 802.11i引入了RSN信息元素。RSN表示强健安全网络,它使用健壮安全网络和强制AES加密。
