IEEE Symposium on Security and Privacy,简称IEEE S&P。会议基本都在美国加州Oakland举办,也有人称其为Oakland。IEEE S&P之所以不简称SP,也是为了跟一个magazine IEEE Security & Privacy区分开来。S&P是CCF A类,Core Conference Ranking A*类会议,H5指数74,Impact Score 11.38。S&P被认为是计算机安全的最高会议,比ACM的CCS更受尊敬。该会自称接受一切与计算机安全的文章,以应用型为主,对理论性的文章尤其crypto-flavor的文章非常排斥。

S&P的录取率较低,基本是11%-15%之间浮动,而S&P'22的录用率为14.6%,创历史最高纪录!S&P的投稿量呈现出整体上升的趋势,去年的投稿量更是达到了1006篇,首次超过1000篇,S&P的录用量也随着投稿量的增加而增加,S&P'22达到147篇。S&P’23年的录用情况暂时还未查询到!据论文录用者透露,论文接收时并没有通知录用率,估计要开会时才知道。
会议基本信息
本届S&P的Symposium将于2023年5月22-24日举办,Security and Privacy Workshops 将于2023年5月25日举办。这两场活动都将在San Francisco, CA举办。大会的General Chair是来自Georgia State University的Daniel Takabi,同时还有2位Program Chairs,分别是来自Cornell Tech的Thomas Ristenpart以及University of Florida的Patrick Traynor。遗憾的是,本届S&P没有国内学者担任组织委员会主席。

在程序委员会成员(Program Committee Members)中,国内有8位学者入选,分别是来自南方科技大学Yinqian Zhang与Fengwei Zhang、清华大学Li Qi、香港科技大学Shuai Wang、香港中文大学的Wei Meng、浙江大学Wenyuan Xu、香港理工大学的Xiapu Luo、复旦大学Yuan Zhang。

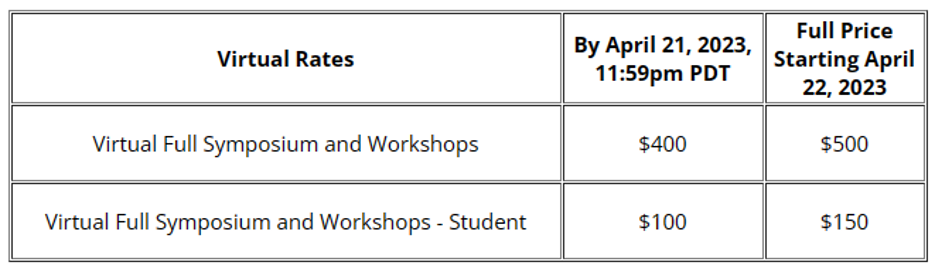
注册费信息
S&P'23的注册分为线上和线下两种,本别设置了早鸟票价和正常注册。线下注册为840刀起,线上注册为100刀起:

论文录用信息
本届S&P国内录用文章37篇,其中浙江大学10篇,清华7篇,复旦、中科院、港理工均为3篇。港城市、港中文、港科大、港大、南京大学、中科大、武汉大学、华为、上科大、山大、扬州大学均为1篇。具体如下:
D-DAE: Defense-Penetrating Model Extraction Attacks
Yanjiao Chen ( Zhejiang University ), Rui Guan ( Wuhan University ), Xueluan Gong ( Wuhan University ), Jianshuo Dong ( Wuhan University ), Meng Xue ( Wuhan University )
Bicoptor: Two-round Secure Three-party Non-linear Computation without Preprocessing for Privacy-preserving Machine Learning
Lijing Zhou ( Huawei Technology, China ), Ziyu Wang ( Huawei Technology, China ), Hongrui Cui ( Shanghai Jiao Tong University, China ), Qingrui Song ( Huawei Technology, China ), Yu Yu ( Shanghai Jiao Tong University, China )
AI-Guardian: Defeating Adversarial Attacks using Backdoors
Hong Zhu ( Chinese Academy of Sciences, China; University of Chinese Academy of Sciences, China ), Shengzhi Zhang ( Boston University, USA ), Kai Chen ( Chinese Academy of Sciences, China; University of Chinese Academy of Sciences, China )
REDEEM MYSELF: Purifying Backdoors in Deep Learning Models using Self Attention Distillation
Xueluan Gong ( School of Computer Science, Wuhan University, China ), Yanjiao Chen ( College of Electrical Engineering, Zhejiang University, China ), Wang Yang ( School of Cyber Science and Engineering, Wuhan University, China ), Qian Wang ( School of Cyber Science and Engineering, Wuhan University, China ), Yuzhe Gu ( School of Cyber Science and Engineering, Wuhan University, China ), Huayang Huang ( School of Cyber Science and Engineering, Wuhan University, China ), Chao Shen ( School of Cyber Science and Engineering, Xi’an Jiaotong University, China )
Spoofing Real-world Face Authentication Systems through Optical Synthesis
Yueli Yan ( ShanghaiTech University ), Yuelin Liu ( ShanghaiTech University ), Zhice Yang ( ShanghaiTech University )
DepthFake: Spoofing 3D Face Authentication with a 2D Photo
Zhihao Wu ( Zhejiang University, China ), Yushi Cheng ( Tsinghua University, China ), Jiahui Yang ( Zhejiang University, China ), Xiaoyu Ji ( Zhejiang University, China ), Wenyuan Xu ( Zhejiang University, China )
Understanding the (In)Security of Cross-side Face Verification Systems in Mobile Apps: A System Perspective
Xiaohan Zhang ( Fudan University, China ), Haoqi Ye ( Fudan University, China ), Ziqi Huang ( Fudan University, China ), Xiao Ye ( Fudan University, China ), Yinzhi Cao ( Johns Hopkins University, USA ), Yuan Zhang ( Fudan University, China ), Min Yang ( Fudan University, China )
Robust Multi-tab Website Fingerprinting Attacks in the Wild
Xinhao Deng ( Tsinghua University, China ), Qilei Yin ( Zhongguancun Laboratory, China ), Zhuotao Liu ( Tsinghua University, China ), Xiyuan Zhao ( Tsinghua University, China ), Qi Li ( Tsinghua University, China ), Mingwei Xu ( Tsinghua University, China ), Ke Xu ( Tsinghua University, Beijing ), Jianping Wu ( Tsinghua University, China )
WarpAttack: Bypassing CFI through Compiler-Introduced Double-Fetches
Jianhao Xu ( Nanjing University, China ), Luca Di Bartolomeo ( EPFL, Switzerland ), Flavio Toffalini ( EPFL, Switzerland ), Bing Mao ( Nanjing University, China ), Mathias Payer ( EPFL, Switzerland )
TeSec: Accurate Server-side Attack Investigation for Web Applications
Ruihua Wang ( KLISS, TNList, School of Software, Tsinghua University ), Yihao Peng ( KLISS, TNList, School of Software, Tsinghua University ), Yilun Sun ( KLISS, TNList, School of Software, Tsinghua University ), Xuancheng Zhang ( KLISS, TNList, School of Software, Tsinghua University ), Hai Wan ( KLISS, TNList, School of Software, Tsinghua University ), Xibin Zhao ( KLISS, TNList, School of Software, Tsinghua University )
Continuous Intrusion: Characterizing the Security of Continuous Integration Services
Yacong Gu ( Qi An Xin Technology Research Institute, China ), Lingyun Ying ( Qi An Xin Technology Research Institute, China ), Huajun Chai ( Qi An Xin Technology Research Institute, China ), Chu Qiao ( University of Delaware, USA ), Haixin Duan ( Tsinghua University; Tsinghua University-QI-ANXIN Group JCNS, China ), Xing Gao ( University of Delaware, USA )
Investigating Package Related Security Threats in Software Registries
Yacong Gu ( QI-ANXIN Technology Research Institute, China ), Lingyun Ying ( QI-ANXIN Technology Research Institute, China ), Yingyuan Pu ( Ocean University of China; QI-ANXIN Technology Research Institute, China ), Xiao Hu ( QI-ANXIN Technology Research Institute, China ), Huajun Chai ( QI-ANXIN Technology Research Institute, China ), Ruimin Wang ( Southeast University; QI-ANXIN Technology Research Institute, China ), Xing Gao ( University of Delaware, USA ), Haixin Duan ( Tsinghua University; Tsinghua University-QI-ANXIN Group JCNS, China )
StyleFool: Fooling Video Classification Systems via Style Transfer
Yuxin Cao ( Shenzhen International Graduate School, Tsinghua University, China ), Xi Xiao ( Shenzhen International Graduate School, Tsinghua University, China ), Ruoxi Sun ( CSIRO's Data61, Australia ), Derui Wang ( CSIRO's Data61, Australia ), Minhui Xue ( CSIRO's Data61, Australia ), Sheng Wen ( Swinburne University of Technology, Australia )
GeeSolver: A Generic, Efficient, and Effortless Solver with Self-Supervised Learning for Breaking Text Captchas
Ruijie Zhao ( Shanghai Jiao Tong University ), Xianwen Deng ( Shanghai Jiao Tong University ), Yanhao Wang ( QI-ANXIN ), Zhicong Yan ( Shanghai Jiao Tong University ), Zhengguang Han ( Shanghai Jiao Tong University ), Libo Chen ( Shanghai Jiao Tong University ), Zhi Xue ( Shanghai Jiao Tong University ), Yijun Wang ( Shanghai Jiao Tong University )
Volttack: Control IoT Devices by Manipulating Power Supply Voltage
Kai Wang ( Zhejiang University, China ), Shilin Xiao ( Zhejiang University, China ), Xiaoyu Ji ( Zhejiang University, China ), Chen Yan ( Zhejiang University, China ), Chaohao Li ( Hangzhou Hikvision Digital Technology Co., Ltd., China ), Wenyuan Xu ( Zhejiang University, China )
PLA-LiDAR: Physical Laser Attacks against LiDAR-based 3D Object Detection in Autonomous Vehicle
Zizhi Jin ( Zhejiang University ), Ji Xiaoyu ( Zhejiang University ), Yushi Cheng ( Tsinghua University ), Bo Yang ( Zhejiang University ), Chen Yan ( Zhejiang University ), Wenyuan Xu ( Zhejiang University )
mmEcho: A mmWave-based Acoustic Eavesdropping Method
Pengfei Hu ( Shandong University ), Wenhao Li ( Shandong University ), Riccardo Spolaor ( Shandong University ), Xiuzhen Cheng ( Shandong University )
3DFed: Adaptive and Extensible Framework for Covert Backdoor Attack in Federated Learning
Haoyang LI ( The Hong Kong Polytechnic University ), Qingqing Ye ( The Hong Kong Polytechnic University ), Haibo Hu ( The Hong Kong Polytechnic University ), Jin Li ( Guangzhou University ), Leixia Wang ( Renmin University of China ), Chengfang Fang ( Huawei International, Singapore ), Jie Shi ( Huawei International, Singapore )
Private, Efficient, and Accurate: Protecting Models Trained by Multi-party Learning with Differential Privacy
Wenqiang Ruan ( Fudan University, China ), Mingxin Xu ( Fudan University, China ), Wenjing Fnag ( Ant Group, China ), Li Wang ( Ant Group, China ), Lei Wang ( Ant Group, China ), Weili Han ( Fudan University, China )
AEM: Facilitating Cross-Version Exploitability Assessment of Linux Kernel Vulnerabilities
Zheyue Jiang ( Fudan University ), Yuan Zhang ( Fudan University ), Jun Xu ( University of Utah ), Xinqian Sun ( Fudan University ), Zhuang Liu ( Fudan University ), Min Yang ( Fudan University )
When Top-down Meets Bottom-up: Detecting and Exploiting Use-After-Cleanup Bugs in Linux Kernel
Lin Ma ( Zhejiang University, China ), Duoming Zhou ( Zhejiang University, China ), Hanjie Wu ( Carnegie Mellon University, USA ), Yajin Zhou ( Zhejiang University, China ), Rui Chang ( Zhejiang University, China ), Hao Xiong ( Zhejiang University, China ), Lei Wu ( Zhejiang University, China ), Kui Ren ( Zhejiang University, China )
RSFuzzer: Discovering Deep SMI Handler Vulnerabilities in UEFI Firmware with Hybrid Fuzzing
Jiawei Yin ( Institute of Information Engineering, Chinese Academy of Sciences, Beijing, China and School of Cyber Security, University of Chinese Academy of Sciences, Beijing, China; Key Laboratory of Network Assessment Technology, Chinese Academy of Sciences; Beijing Key Laboratory of Network Security and Protection Technology ), Menghao Li ( Institute of Information Engineering, Chinese Academy of Sciences, Beijing, China and School of Cyber Security, University of Chinese Academy of Sciences, Beijing, China; Key Laboratory of Network Assessment Technology, Chinese Academy of Sciences; Beijing Key Laboratory of Network Security and Protection Technology ), Yuekang Li ( Nanyang Technological University ), Yong Yu ( Institute of Information Engineering, Chinese Academy of Sciences, Beijing, China; Key Laboratory of Network Assessment Technology, Chinese Academy of Sciences; Beijing Key Laboratory of Network Security and Protection Technology ), Boru Lin ( Institute of Information Engineering, Chinese Academy of Sciences, Beijing, China and School of Cyber Security, University of Chinese Academy of Sciences, Beijing, China; Key Laboratory of Network Assessment Technology, Chinese Academy of Sciences; Beijing Key Laboratory of Network Security and Protection Technology ), Yanyan zou ( Institute of Information Engineering, Chinese Academy of Sciences, Beijing, China and School of Cyber Security, University of Chinese Academy of Sciences, Beijing, China; Key Laboratory of Network Assessment Technology, Chinese Academy of Sciences; Beijing Key Laboratory of Network Security and Protection Technology ), Yang Liu ( Nanyang Technological University ), Wei Huo ( nstitute of Information Engineering, Chinese Academy of Sciences, Beijing, China and School of Cyber Security, University of Chinese Academy of Sciences, Beijing, China; Key Laboratory of Network Assessment Technology, Chinese Academy of Sciences; Beijing Key Laboratory of Network Security and Protection Technology ), Jingling Xue ( UNSW Sydney )
Continual Observation under User-level Differential Privacy
Wei Dong ( Hong Kong University of Science and Technology, China ), Qiyao Luo ( Hong Kong University of Science and Technology, China ), Ke Yi ( Hong Kong University of Science and Technology, China )
Discop: Provably Secure Steganography in Practice Based on “Distribution Copies”
Jinyang Ding ( University of Science and Technology of China, China ), Kejiang Chen ( University of Science and Technology of China, China ), Yaofei Wang ( Hefei University of Technology, China ), Na Zhao ( University of Science and Technology of China, China ), Weiming Zhang ( University of Science and Technology of China, China ), Nenghai Yu ( University of Science and Technology of China, China )
Callee: Recovering Call Graphs for Binaries with Transfer and Contrastive Learning
Wenyu Zhu ( Tsinghua University & BNRist, China ), Zhiyao Feng ( Tsinghua University & BNRist, China ), Zihan Zhang ( Tsinghua University & BNRist, China ), Jianjun Chen ( Tsinghua University & Zhongguancun Laboratory, China ), Zhijian Ou ( Tsinghua University, China ), Min Yang ( Fudan University, China ), Chao Zhang ( Tsinghua University & BNRist & Zhongguancun Laboratory, China )
Effective ReDoS Detection by Principled Vulnerability Modeling and Exploit Generation
Xinyi Wang ( Institute of Information Engineering, Chinese Academy of Sciences, China ), Cen Zhang ( Nanyang Technological University ), Yeting Li ( Institute of Information Engineering, Chinese Academy of Sciences, China ), Zhiwu Xu ( Shenzhen University ), Shuailin Huang ( Institute of Information Engineering, Chinese Academy of Sciences, China ), Yi Liu ( Nanyang Technological University ), Yican Yao ( Institute of Information Engineering, Chinese Academy of Sciences, China ), Yang Xiao ( Institute of Information Engineering, Chinese Academy of Sciences, China ), Yanyan Zou ( Institute of Information Engineering, Chinese Academy of Sciences, China ), Yang Liu ( Institute of Information Engineering, Chinese Academy of Sciences, China ), Wei Huo ( Institute of Information Engineering, Chinese Academy of Sciences, China )
BlindHub: Bitcoin-Compatible Privacy-Preserving Payment Channel Hubs Supporting Variable Amounts
Xianrui Qin ( The University of Hong Kong ), Shimin Pan ( The University of Hong Kong ), Arash Mirzaei ( Monash University ), Zhimei Sui ( Monash University ), Oguzhan Ersoy ( Radboud University and Delft University of Technology ), Amin Sakzad ( Monash University ), Muhammed Esgin ( Monash University and CSIRO’s Data61 ), Joseph K. Liu ( Monash University ), Jiangshan Yu ( Monash University ), Tsz Hon Yuen ( The University of Hong Kong )
Tyr: Finding Consensus Failure Bugs in Blockchain System with Behaviour Divergent Model
Yuanliang Chen ( Tsinghua University ), Fuchen Ma ( Tsinghua University ), Yuanhang Zhou ( Tsinghua University ), Yu Jiang ( Tsinghua University ), Ting Chen ( University of Electronic Science and Technology of China ), Jiaguang Sun ( Tsinghua University )
Leaking Arbitrarily Many Secrets: Any-out-of-Many Proofs and Applications to RingCT Protocols
Tianyu Zheng ( The Hong Kong Polytechnic University ), Shang Gao ( The Hong Kong Polytechnic University ), Yubo Song ( Southeast University ), Bin Xiao ( The Hong Kong Polytechnic University )
Limits of I/O Based Ransomware Detection: An Imitation Based Attack
Chijin Zhou ( Tsinghua University, China ), Lihua Guo ( Tsinghua University, China ), Yiwei Hou ( Tsinghua University, China ), Zhenya Ma ( Tsinghua University, China ), Quan Zhang ( Tsinghua University, China ), Mingzhe Wang ( Tsinghua University, China ), Zhe Liu ( Nanjing University of Aeronautics and Astronautics, China ), Yu Jiang ( Tsinghua University, China )
SelectFuzz: Efficient Directed Fuzzing with Selective Path Exploration
Changhua Luo ( Chinese University of Hong Kong ), Wei Meng ( Chinese University of Hong Kong ), Penghui Li ( Chinese University of Hong Kong )
ODDFUZZ: Discovering Java Deserialization Vulnerabilities via Structure-Aware Directed Greybox Fuzzing
Sicong Cao ( Yangzhou University, China ), Biao He ( Ant Group, China ), Xiaobing Sun ( Yangzhou University, China ), Yu Ouyang ( Ant Group, China ), Chao Zhang ( Tsinghua University, China ), Xiaoxue Wu ( Yangzhou University, China ), Ting Su ( East China Normal University ), Lili Bo ( Yangzhou University, China ), Bin Li ( Yangzhou University, China ), Chuanlei Ma ( Ant Group, China ), Jiajia Li ( Ant Group, China )
DeHiREC: Detecting Hidden Voice Recorders via ADC Electromagnetic Radiation
Ruochen Zhou ( Zhejiang University ), Xiaoyu Ji ( Zhejiang University ), Chen Yan ( Zhejiang University ), Yi-Chao Chen ( Shanghai Jiao Tong University; Microsoft Research Asia ), Wenyuan Xu ( Zhejiang University ), Chaohao Li ( Zhejiang University )
Man-in-the-Middle Attacks without Rogue AP: When WPAs Meet ICMP Redirects
Xuewei Feng ( Tsinghua University, China ), Qi Li ( Tsinghua University and Zhongguancun Lab, China ), Kun Sun ( George Mason University, USA ), Yuxiang Yang ( Tsinghua University ), Ke Xu ( Tsinghua University and Zhongguancun Lab, China )
VIDEZZO: Dependency-aware Virtual Device Fuzzing
Qiang Liu ( Zhejiang University, China; EPFL, Switzerland ), Flavio Toffalini ( EPFL, Switzerland ), Yajin Zhou ( Zhejiang University, China ), Mathias Payer ( EPFL, Switzerland )
How IoT Re-using Threatens Your Sensitive Data: Exploring the User-Data Disposal in Used IoT Devices
Peiyu Liu ( Zhejiang University, China ), Shouling Ji ( Zhejiang University, China ), Lirong Fu ( Zhejiang University, China ), Kangjie Lu ( University of Minnesota, USA ), Xuhong Zhang ( Zhejiang University, China ), Jingchang Qin ( Zhejiang University, China ), Wenhai Wang ( Zhejiang University, China ), Wenzhi Chen ( Zhejiang University, China )
Uncovering User Interactions on Smartphones via Contactless Wireless Charging Side Channels
Tao Ni ( City University of Hong Kong ), Xiaokuan Zhang ( George Mason University ), Chaoshun Zuo ( The Ohio State University ), Jianfeng Li ( The Hong Kong Polytechnic University ), Zhenyu Yan ( The Chinese University of Hong Kong ), Wubing Wang ( DBAPPSecurity Co., Ltd ), Weitao Xu ( City University of Hong Kong ), Xiapu Luo ( The Hong Kong Polytechnic University ), Qingchuan Zhao ( City University of Hong Kong )
MagBackdoor: Beware of Your Loudspeaker as A Backdoor For Magnetic Injection Attacks
Tiantian Liu ( Zhejiang University, Hangzhou, Zhejiang, China ), Feng Lin ( Zhejiang University, Hangzhou, Zhejiang, China ), Zhangsen Wang ( Zhejiang University, Hangzhou, Zhejiang, China ), Chao Wang ( Zhejiang University, Hangzhou, Zhejiang, China ), Zhongjie Ba ( Zhejiang University, Hangzhou, Zhejiang, China ), Li Lu ( Zhejiang University, Hangzhou, Zhejiang, China ), Wenyao Xu ( University at Buffalo, Buffalo, New York, USA ), Kui Ren ( Zhejiang University, Hangzhou, Zhejiang, China )
【详情请参考:】https://www.ieee-security.org/TC/SP2023/program.html